In a joint statement, the Federal Bureau of Investigation (FBI) and the U.S. Department of Justice (DOJ) announced the seizure of the domain name WeLeakInfo.to and two other domain names (ipstress.in and ovh-booter.com) as part of an international investigation related to illegal access to personal information.
The message describes these online platforms as “worryingly common threats,” detailing how threat actors used these sites for trafficking in stolen personal information: “Using strong relationships with our international partners, we will address crimes like these, which threaten privacy, security, and commerce around the world.”
WeLeakInfo.to operators claimed to provide their users with a search engine to review and obtain personal information illegally obtained in more than 10,000 data breach incidents, with around 7 billion records indexed, exposing data such as full names, phone numbers, email addresses, and even online account passwords.
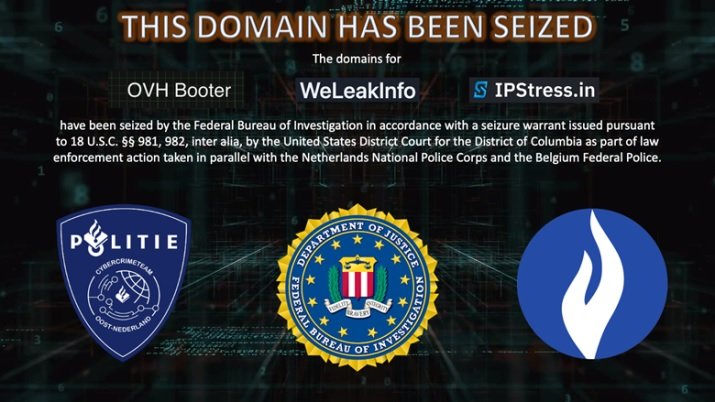
On the domains ipstress.in and ovh-booter.com, the report describes them as platforms for launching denial of service (DoS) attacks, commonly known as booting or stressor services. From these websites, threat actors could flood a specific web server with malicious traffic, making them inaccessible to legitimate users.
As of this operation, the seized domain names, and any related domains, are now in the custody of the federal government, effectively suspending the operation of these malicious services. Visitors to the site will now find a seizure sign, reporting that U.S. federal authorities are responsible for the seizure.
The seizures of these domains were part of coordinated police action with the authorities of Belgium and the Netherlands. These police agencies arrested one of the main operators of these platforms, in addition to collaborating with various raids.
U.S. authorities have asked anyone who has information about other members of this cybercriminal operation to file a complaint immediately, as this is a critical time to act against these groups.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











