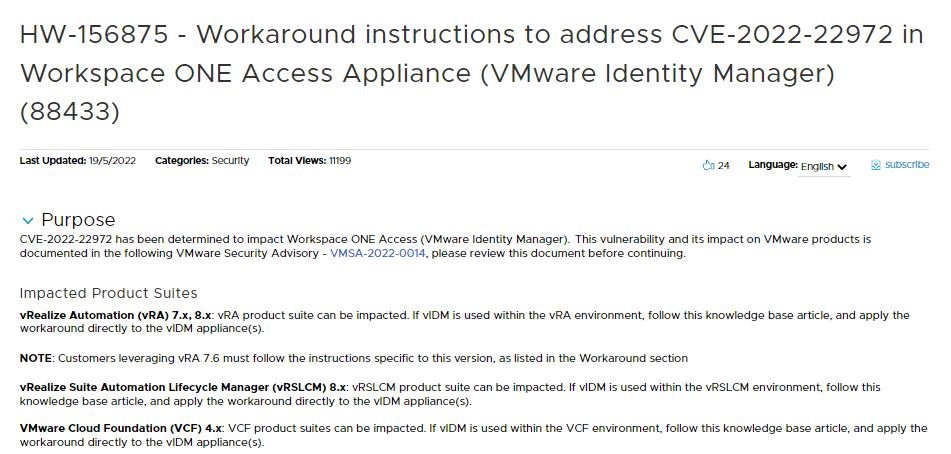
A proof of concept (PoC) code for CVE-2022-22972, a critical vulnerability in some VMware products such as Workspace ONE Access, Identity Manager, and vRealize Automation, has been publicly disclosed.
This PoC was published by researchers at security firm Horizon3, in conjunction with technical analysis, after VMware released corresponding updates: “This script can be used by circumventing authentication in vRealize Automation,” the researchers report.
A scan with Shodan shows a limited number of potentially compromised VMware devices, most used by industry organizations, hospitals, and government entities. Horizon3 experts mention that this header manipulation vulnerability is relatively simple and threat actors should not have great difficulty exploiting unpatched deployments.
In this regard, the Cybersecurity and Infrastructure Security Agency (CISA) issued an Emergency Directive in which federal agencies in the U.S. are ordered to immediately update vulnerable VMware products, and even eliminate them if necessary.
While this flaw has not been exploited in the wild, threat actors have begun to attack corrected implementations to try to inject a cryptocurrency miner: “CISA expects threat actors to quickly develop the ability to exploit these vulnerabilities.”
This has been a difficult year for VMware. In April, the company fixed two critical remote execution and privilege escalation vulnerabilities tracked as CVE-2022-22954 and CVE-2022-229600 in VMware Workspace ONE Access and VMware Identity Manager.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











