The legal conflict between Hollywood stars Johnny Depp and Amber Heard has caught everyone’s attention, reaching social media trends for a couple of weeks now. Although he has already lost a previous trial in the United Kingdom, Depp has not stopped receiving signs of support from his fans, some more daring than others.
According to entertainment-focused media outlet TMZ, a hacker accessed without authorization the systems of the International Movie Database (IMDb), an online database that stores all available information about movies and TV series, in order to modify the profile of the actress to rename her as “Amber Turd”, in a pun referring to the excrement.
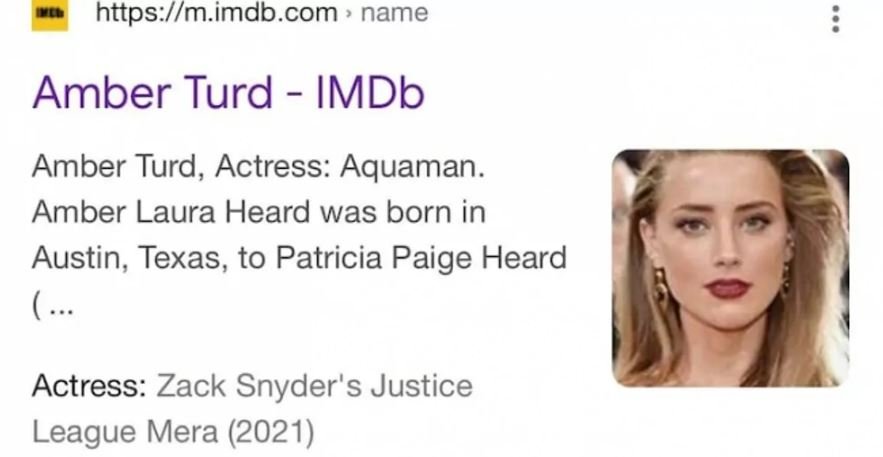
It is unknown how this unusual attack occurred, although it is most likely that the hacker, or group of hackers, accessed through stolen access credentials, available on some hacking forum.
Heard has been the subject of ridicule and harassment since the controversy began with her now ex-husband, as Depp’s fans consider her guilty of the actor being fired from productions such as “Fantastic Beasts” or the successful saga “Pirates of the Caribbean”, in addition to facing increasing difficulties in finding new roles in films. Consequently, Depp’s fans have flooded social media with very direct comments against the actress.
Most of these Internet users accuse Heard of lying, pointing out the multiple contradictions in his testimonies and referencing the evidence presented by Depp’s lawyers, who claim that it was the actor who suffered from domestic violence.
Last Friday it transpired that both parties agreed to a week off the trial, so the activities will be resumed on May 16. Closing arguments are expected to be filed on May 27, so a verdict is only a few weeks away.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










