Security researcher Wolfie Christl has detailed how a seemingly harmless custom keyboard mobile app with millions of downloads has almost complete access to the devices where it is installed, in addition to hiding tracking code from 20 companies, including Google, Facebook, Amazon, and other data brokers, some linked to the Russian government.
GO Keyboard – Emojis & Themes is described as an app for keyboard customization, with more than 1,000 themes, emojis and fonts for the user to add to their devices. In its Google Play Store profile, it can be seen that the app has more than 100 million downloads and even assure its users that their confidential information will never be collected, something that we could already doubt.
Since the app is still on the Play Store, any Android user might assume that this is a reliable tool. Unfortunately, sometimes unscrupulous developers manage to evade the security mechanisms of the application repository, either by hiding dangerous variants or, as in this case, by requesting highly invasive permissions on the affected systems.
According to Christl, the GO Keyboard code contains a total of 27 trackers, which allow collection data about certain characteristics of a smartphone or user activities, mainly for marketing purposes. Among the trackers used by GO Keyboard are Amazon Advertisement, Facebook Ads, Facebook Analytics and Google AdMob.
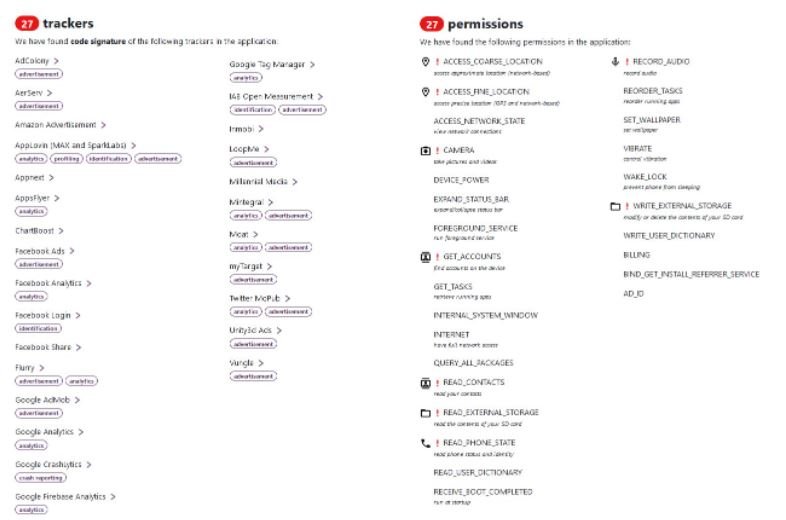
The app also contains code signed by myTarget, an advertising platform provided by Mail.Ru Group and including all major Russian-speaking social networks.
As if that were not enough, at the time of its installation GO Keyboard requests 27 permissions on the system, including access to the precise location of the device, execution of the service in the foreground, access to network connections, full access to the network, use of the device’s camera, audio recording, access, modification and deletion of the contents of the SD card, and prevent the device from sleeping. Specialists at Exodus, which detects whether mobile apps contain third-party tracking code, find it worrisome that a simple tool to customize a smartphone’s keyboard requests so many permissions on the affected systems.
These findings have already been shared with Google, although the app is still available on the Play Store and its developers don’t seem to have made any changes. In addition, there are hundreds of applications that maintain similar practices, accumulating millions of downloads and exposing users to all kinds of risks. As usual, the recommendation for Android users is to uninstall this app from their devices.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










