Privilege escalation attacks pose a severe cyber security risk to all kinds of systems in public and private organizations. In these attacks, threat actors exploit vulnerabilities or design flaws in operating systems and software applications to gain illegitimate access to resources that would otherwise be restricted to authorized users only, triggering dangerous hacking scenarios.
As with other variants of hacking, prevention becomes a fundamental issue, as a protected computer system and constantly monitored and updated will be less exposed to privilege escalation attacks, so it is important to know this and other attack methods.
Next, specialists from the International Institute of Cyber Security’s (IICS) cyber security awareness course will show you a tool for deploying local privilege escalation attacks on Windows. The tool, called localbrute.ps1, is written in PowerShell to apply brute force against local Windows administrator accounts.
This tool is lightweight and does not require any third-party modules, making it a great addition to traditional privilege escalation methods applicable to various pentesting scenarios.
Risks of privilege escalation
An attack on local administrative accounts can be a significant attack vector, especially when an account lockout policy is missing. According to the experts of the cyber security awareness course, we can try as many login attempts as we want and, if we manage to guess the password, we will obtain full control of the system, allowing all kinds of hacking tasks such as:
- Disable all system security features
- Extract access credentials and other sensitive details
- Create raw network packets and execute exploits for subsequent attacks
The tool performs a local brute force attack on the target system, so its use is very specific. This tool can be useful in cases where user credentials exist with low privileges and where it is possible to execute commands.
Features of the tool
According to the experts of the cyber security awareness course, localbrute.ps1 makes login attempts locally to the system using native functions of the same Windows system. Among the main features are:
- Small size
- Able to make login attempts against any selected local account using the given word list
- Written in pure PowerShell
- It is not considered a malicious tool, so it is not detected by antivirus tools
There are two versions of localbrute.ps1, a regular version and a longer version. Let’s see more in detail the operation of the tool.
Using localbrute.ps1
According to the experts of the cyber security awareness course, the first thing we should consider is to define what an administrator account is in the system. These accounts typically include:
- Members of the local administrators group
- The local administrator account itself
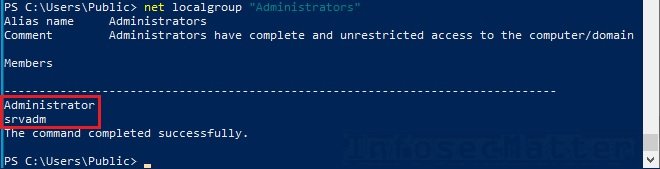
Here’s how we can find the accounts in the Local Admins group:
net localgroup administrators
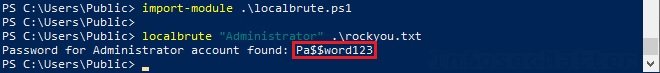
Now, run localbrute:
Import-Module .\localbrute.ps1
To continue, run the following command:
localbrute [debug]
For example:
localbrute Administrator .\rockyou.txt
Remember that a brute force attack can take considerable time.
How does it work?
The tool simply applies brute force using a list of words for the user to try to authenticate to the system. This software uses the internal functions of Windows DirectoryServices.AccountManagement in the context of the local computer. Below is a PowerShell code snippet to verify credentials locally:
$u = 'Administrator'
$p = 'Pa$$w0rd!'
Add-Type -AssemblyName System.DirectoryServices.AccountManagement
$t = [DirectoryServices.AccountManagement.ContextType]::Machine
$a = [DirectoryServices.AccountManagement.PrincipalContext]::new($t)
$a.ValidateCredentials($u,$p)
The extended version of the tool has some additional features to improve usability when working with large word lists. That is, it maintains a status file (localbrute.state) in the current working directory to track progress, mention the specialists of the cyber security awareness course.
After a break (^ C), the tool will type the last password found from the given word list for the given username. This allows the attack to continue after a restart.
The status file also stores records of accounts that have already been hacked.
You can enable debug mode to view the iteration in progress:
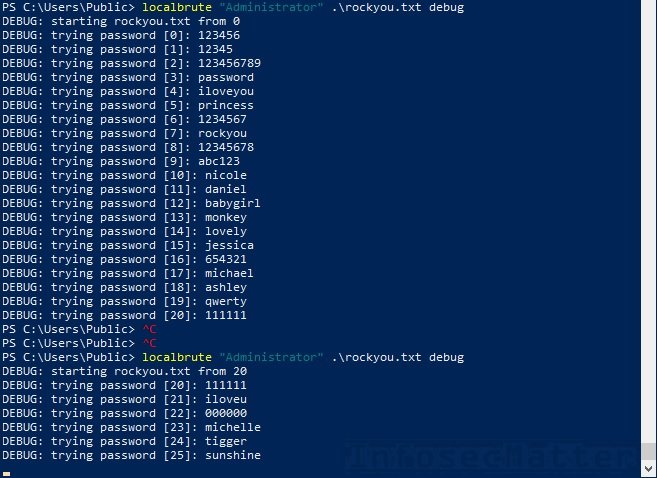
The speed is about 100 to 200 login attempts per second, depending on the performance of the target system. This is not a quick process, but it is still much more efficient than other similar tools. Running multiple instances of the localbrute script in parallel will not speed up iteration, so the experts in the cyber security awareness course do not recommend implementing these kinds of methods.
Please note that this article was prepared for informational purposes only and does not represent a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
To learn more about computer security risks, malware, vulnerabilities, information technologies, and more information about the cyber security awareness course, do not hesitate to enter the website of the International Institute of Cyber Security (IICS).

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










