This week concluded the most recent edition of the ethical hacking event Pwn2Own Miami 2022, during which prizes of $ 400,000 USD were awarded thanks to the report of 26 zero-day exploits to abuse ICS and SCADA products. In this edition, the researchers focused on implementations such as control servers, data gateways, and human-machine interface.
The Zero Day Initiative (ZDI) posted a message thanking those involved in the event: “Thank you again to all competitors and participating suppliers for their cooperation and for fixing the errors revealed.” Affected product vendors have 120 days to release patches for the reported flaws in Pwn2Own.
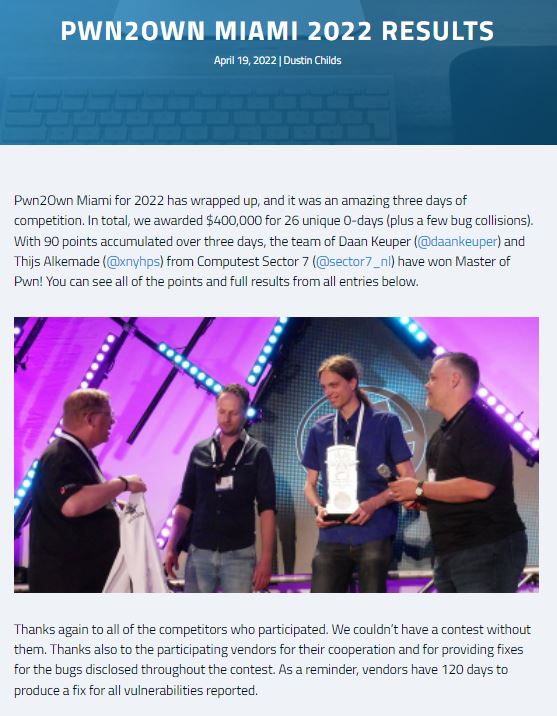
The main winners of the Pwn2Own Miami 2022 event are Daan Keuper and Thijs Alkemade of Computest Sector 7. During the first day, the team earned $20,000 USD by demonstrating a code execution attack on the Inductive Automation Ignition SCADA solution, exploiting a missing authentication flaw. During this day Computest Sector 7 also demonstrated a remote code execution (RCE) attack on AVEVA Edge HMI/SCADA, receiving a reward of $20,000 USD.
On the second day, the researchers exploited an infinite loop error to trigger a denial of service (DoS) condition against Unified Automation’s C++ demo server, earning $5,000 USD, in addition to demonstrating an authentication evasion attack on OPC Foundation OPC UA .NET Standard, earning $40,000 USD more.
Computest Sector 7 won the Master of Pwn title after winning a total of $90,000 over the three days of the contest and taking first place on the leaderboard with a total of 90 points.
This year’s Pwn2Own Miami was held in person and also allowed the remote participation of some researchers. During the first edition of Pwn2Own Miami, with the theme of ICS, held in January 2020, ZDI awarded $280,000 for the reporting of 24 zero-day vulnerabilities in ICS and SCADA products.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











