A security report from Check Point notes that three vulnerabilities in audio decoders on Qualcomm and MediaTek chips would allow threat actors to remotely access audio conversations on millions of mobile devices. In addition, in critical cases the exploitation would allow remote code execution (RCE) attacks to be carried out through a specially designed audio file.
In their report, the researchers note that remote code execution and information theft aren’t the only risks, as a malicious hacker could use an unprivileged Android app to perform a privilege-escalation attack and gain access to user data.
Apparently, these flaws exist due to an open-source audio encoding format developed by Apple in 2011. Known as Apple Lossless Audio Codec (ALAC) or Apple Lossless, this is an audio codec format used for digital music data compression. Since its launch, multiple third-party vendors such as Qualcomm and MediaTek have incorporated it into their own audio decoders.
Although Apple fixed its proprietary version of ALAC, the open-source variant of the codec has not received any maintenance since its publication on GitHub, which occurred in October 2011. The flaws reported by Check Point reside in this free-to-use version, used by Qualcomm and MediaTek processors. Below is a list of the reported flaws:
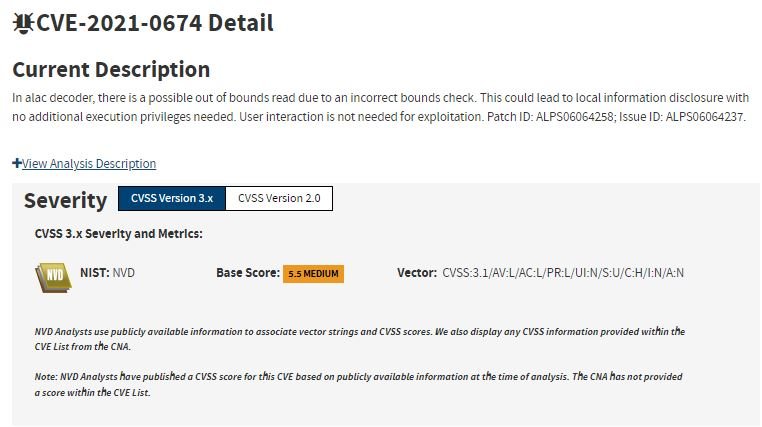
- CVE-2021-0674: Incorrect input validation error in ALAC decoder leading to disclosure of information without user interaction in MediaTek
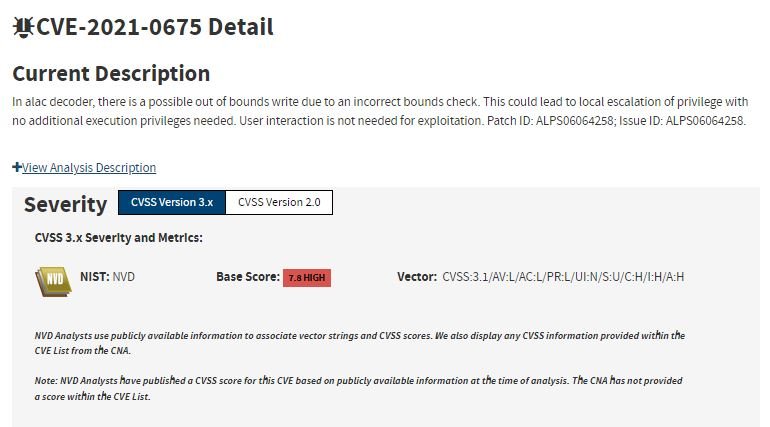
- CVE-2021-0675: Local privilege escalation failure in ALAC decoder resulting from an off-limits write in MediaTek
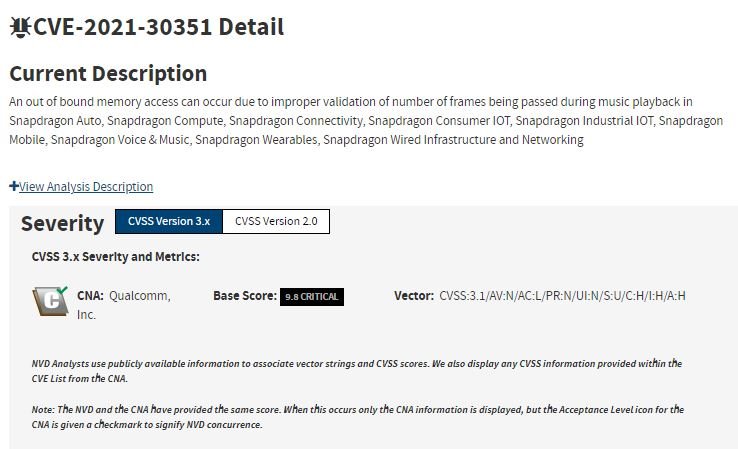
- CVE-2021-30351: Out-of-bound memory access due to improper validation of the number of frames passed during music playback on Qualcomm chipsets
In a proof-of-concept (PoC) exploit, the successful exploit allowed the phone’s camera flow to be stolen, says Check Point researcher Slava Makkaveev, who is credited with discovering these vulnerabilities.
Vulnerable chipset manufacturers addressed this vulnerability in December 2021. In his announcement, Makkaveev insists: “The threat actors could have sent one (or any multimedia file) and, when played, could have injected a code into the privileged media service. The hackers could have seen what the affected phone user sees on their device.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











