Cybersecurity specialists from the firm Kryptowire report the detection of CVE-2022-22292, a severe vulnerability in some Samsung devices with versions 9, 10, 11 and 12 of the Android operating system. According to the report, exploiting the flaw would allow the delivery of arbitrary Intent objects to be executed by a pre-installed application with high privileges.
In addition to this issue, an underlying vulnerability would allow a third-party application to be used to send data to arbitrary activity application components in the context of a pre-installed application. This opens up a large attack surface for third-party applications, allowing arbitrary Intent objects with embedded data to be sent to activities that appear to originate from the affected system itself. In other words, an unprivileged application can use an unprotected interface to send Intent objects and perform actions on its behalf.
What is this flaw?
Mobile apps are limited to their own context when you launch an activity app component through an Intent object. This flaw would allow local applications to indirectly use the context of a pre-installed application with the system’s User ID (UID) when initiating activities through a malicious Intent object.
The concept of an attacker-controlled Intent object refers to the pre-installed application affected by this vulnerability using the system UID to obtain an Intent object embedded within another Intent object sent from a malicious application, which will then execute an application activity component using the embedded Intent object. This can be conceptualized as “intent forwarding,” where the attacker controls the Intent object that sends a privileged process that would allow the start of non-exported application activity components (android:exported=”false”).
This condition allows third-party applications to control the contents of Intent objects sent by a pre-installed application running with the system UID. The affected pre-installed application that forwards the Intent objects it receives is a tool with a package name com.android.server.telecom, and apparently the problem in the application exists due to incorrect access control on a dynamically registered transmission receiver in com.android.server.telecom.
This does not seem to be a problem originated in Android Open Source Project (AOSP), because at the moment it only seems to affect some Samsung devices managing com.android.server.telecom files. A local application capable of exploiting the vulnerability can run in the background to initiate specific activities completely inadvertently.
By exploiting the vulnerability, the local application can use specific activities to gain additional capabilities programmatically through privilege escalation, including factory reset, installation of arbitrary applications, arbitrary application installing and uninstalling, and access to sensitive information.
Compromised devices
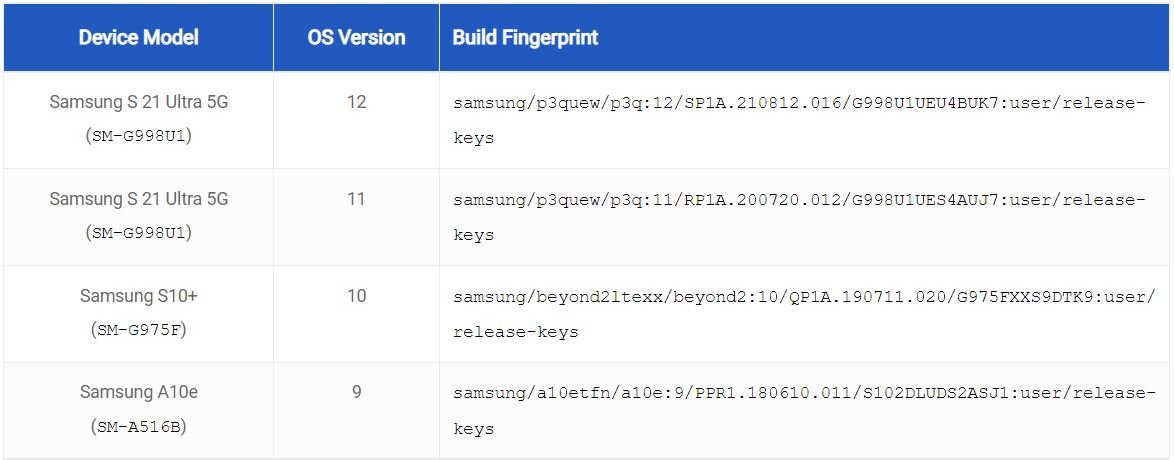
The following table contains a list of the affected Samsung Android devices. This table is not intended to be exhaustive, and has been put together only to show that researchers have verified that a variety of Android versions, models, and builds are vulnerable:
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











