Cisco Talos researchers reported detecting a new hacking campaign by the group identified as Transparent Tribe and targeting government organizations in India. Active at least since mid-2021, this campaign is based on the use of fraudulent web domains that pose as official Indian government platforms for the delivery of malicious payloads, a tactic associated with this group of hackers.
Experts mention that the group, also known as APT36 or Mythic Leopard, has undergone significant changes over the past year, adopting new attack mechanisms and multiple malware variants during its intrusions. Specifically hackers have used small, customizable downloaders, capable of adapting to various environments quickly and efficiently.
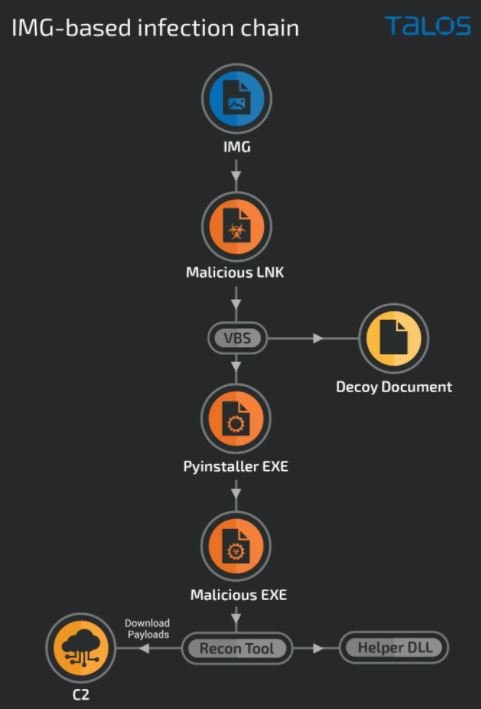
In the most recent campaign by Trasparent Tribe, multiple malware delivery methods were identified, including executables disguised as legitimate application installers or storage files. Indian users who encountered any of these malicious payloads could have been infected with one of the malware variants described below:
- CrimsonRAT, a remote access Trojan (RAT) variant frequently used by these hackers to deploy cyber spying operations targeting military organizations
- A lightweight .NET-based implant able to run arbitrary commands on infected systems
- A previously unknown Python-based stager that leads to the deployment of .NET-based reconnaissance tools and RATs
This operation also relies on the use of fake domains posing as legitimate government organizations to deliver malicious payloads. This is a tactic commonly linked with this group. Besides, although not their most common tactic, threat actors can also use phishing messages from the Indian government regarding the COVID-19 pandemic.

The researchers believe that tools like CrimsonRAT would allow threat actors to persist and long-term remote access to affected systems for espionage purposes, plus the attack vector remains functional for this and other groups of threat actors. While Transparent Tribe is not considered a sophisticated hacking group, its practices demonstrate great persistence and motivation to maintain an attack, so this threat should not be taken lightly especially considering their main goal seems to be cyber spying and remote access to critical systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











