Phishing is still one of the most common and efficient cybercriminal practices, since in many cases attackers target unsuspecting users without knowledge in cybersecurity, not to mention that hackers resort to all kinds of deceptions to gain the trust of victims.
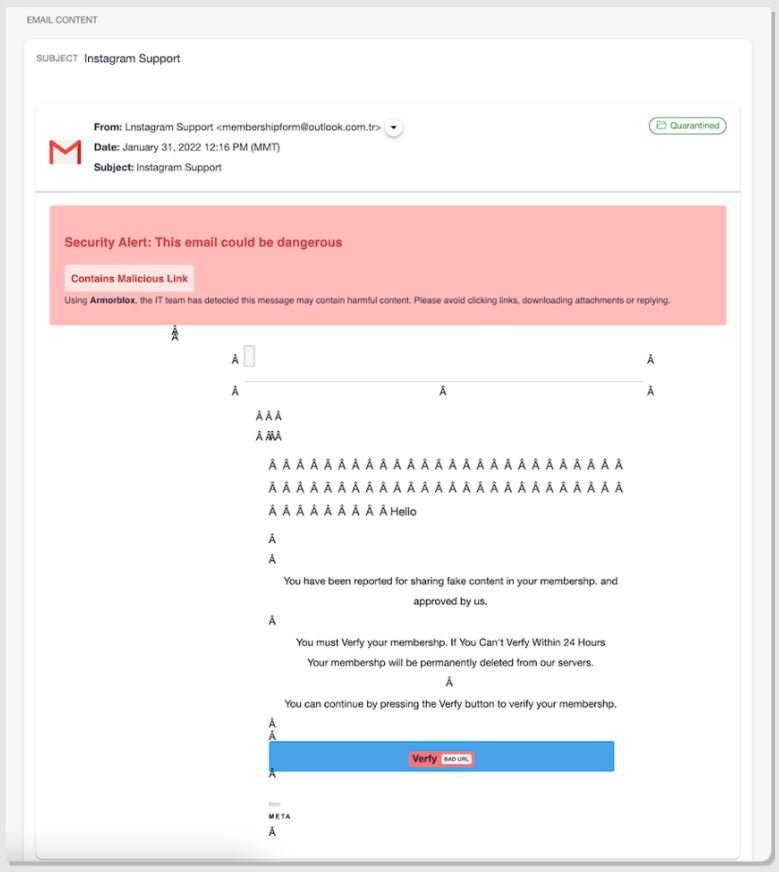
Specialists have detected a new Instagram phishing campaign in which threat actors use an email supposedly sent from this social media platform arguing that the user has to respond to an alleged “Instagram claim”. In the following screenshot, we can observe that the message is in plain text and in the subject line it simply mentions “INSTAGRAM SUPPORT”, just like in the sender’s line.
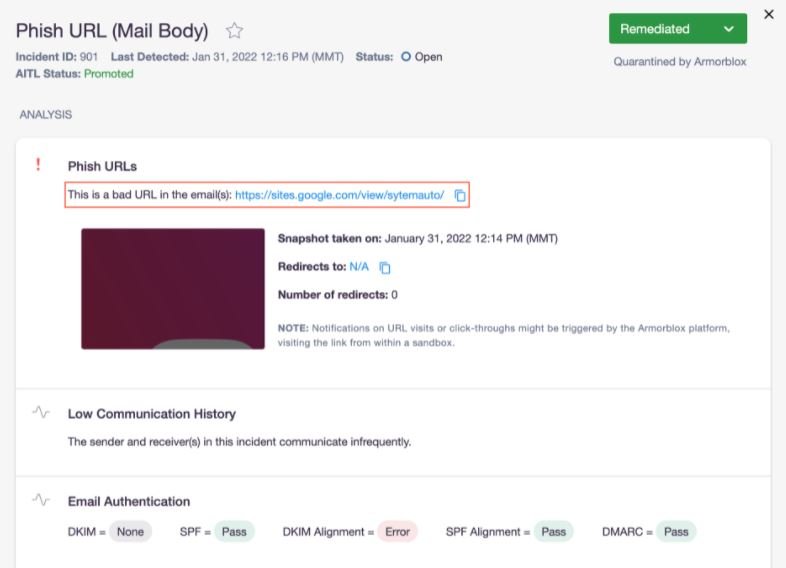
According to the report, this phishing and social engineering campaign is aimed at employees of an insurer in the U.S., under the guise of Instagram Support. The message was sent from a legitimate Outlook domain, and the hackers employed various techniques to evade Google’s email security mechanisms.
As for the content of the message, it states that the target user was reported because their activity on Instagram violates copyright laws. The attackers strategically designed this message with the clear intention of creating a sense of urgency in the user and forcing him to click on the attached link, setting a limit of 24 hours to respond to the alleged report.

As you can guess, the link redirects the user to a fraudulent website with a fake Instagram account verification page; you can even see the Meta logos and the web browser used. On this site the target user is asked to enter their Instagram login credentials and complete a supposed verification form.
If the target user falls into the trap, their login credentials will be sent to a C&C server controlled by the hackers, so these sensitive logs will be completely exposed.
This is an active campaign and can be highly harmful to affected organizations and users, so it will be necessary to follow some recommendations to avoid a catastrophic scenario. The risks of this and other phishing campaigns can be reduced by following the following recommendations:
- Be careful before opening any unsolicited email. No legitimate company or organization requests personal information without prior contact
- Do not download attachments or click on links included in these messages
- Use different login credentials for your personal applications and business applications. Using the same passwords increases the risk of exposure in case hackers can access one of your passwords
- Use multi-factor authentication for your online platforms whenever possible
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










