In a message shared with an international media outlet, phone operator Vodafone confirmed it is investigating reports of an alleged data breach revealed by hackers from cybercriminal group Lapsus$.
Through their Telegram channel, the alleged hackers published a survey for their subscribers to decide what the next leak of the group would be after revealing confidential information from chipmaker NVIDIA. Among the options was a supposed 200 GB file storing Vodafone’s source code.
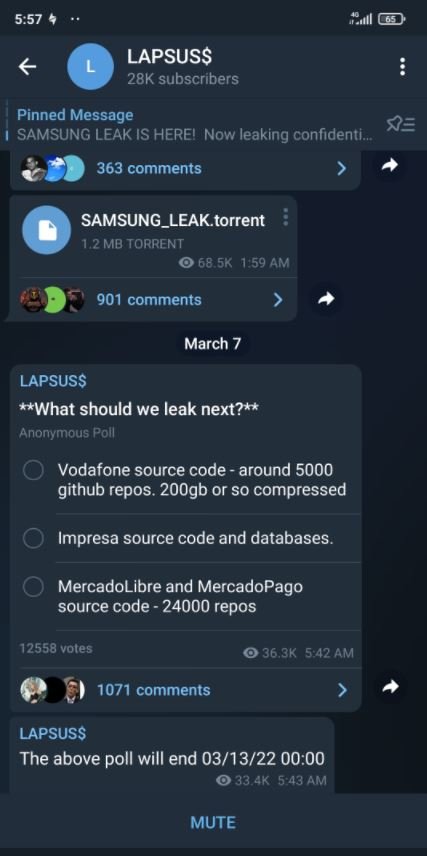
The survey also included as options the source code and databases of the Portuguese media firm Impresa, and the source code of MercadoLibre, the e-commerce giant based in Argentina. Subscribers to the Telegram channel seem to prefer that data be leaked from Vodafone, which was leading the vote at the time of writing.
In its message, the telecommunications company says it is aware of Lapsus$’s threats: “We are investigating these reports together with the police; at the moment we cannot affirm the veracity of this report. However, we are in a position to state that, in general, the types of repositories referenced in the complaint contain proprietary source code and do not contain data from our customers.”
Operating from somewhere in South America, Lapsus$ has hogged cybersecurity reports in recent weeks. In addition to the attack on NVIDIA, hackers reportedly managed to compromise Samsung’s systems, stealing snippets of the source code used in the Galaxy family of smartphones and other sensitive details.
To the misfortune of its users, Vodafone has become a frequent target for hacking groups. A few weeks ago, the firm confirmed that its branch in Portugal suffered a cyberattack that interrupted its services for a long time, ensuring that the leak did not involve personal information of its clients.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











