Cybersecurity specialists report the detection of three zero-day vulnerabilities in uninterruptible power supply (UPS) devices developed by APC, a subsidiary of the well known tech company Schneider Electric. The set of vulnerabilities, dubbed as TLStorm, resides in APC Smart-UPS devices, very popular in sectors such as industry, commerce and computer security.
The security firm Armis, in charge of this finding, mentions that two of the reported flaws, tracked as CVE-2022-22805 and CVE-2022-22806 reside in the implementation of the Transport Layer Security (TLS) protocol, which connects Smart-UPS SmartConnect devices with the Schneider Electric management cloud.
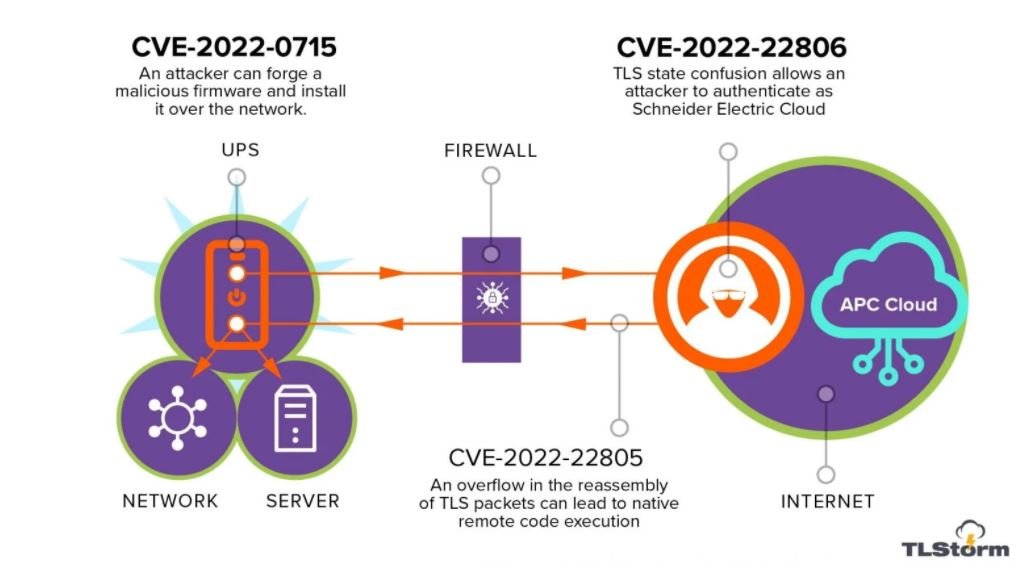
On the other hand, the flaw tracked as CVE-2022-0715 relates to the firmware of almost all Smart-UPS devices, which is not cryptographically signed and its authenticity cannot be verified during its installation on the system.
This absence of signature would allow threat actors to create a malicious version of the firmware and deliver it as an update to the affected UPS devices, leading to a remote code execution (RCE) scenario.
During testing, the researchers were able to exploit the flaw and create a malicious APC firmware version that was accepted by Smart-UPS devices as an official update. The consequences of the attack vary depending on the affected device:
- Smart-UPS devices that feature SmartConnect cloud connection functionality can be upgraded from the cloud management console
- Older Smart-UPS devices that use the Network Management Card (NMC) can be upgraded over the local network
- Most Smart-UPS devices can also be upgraded via a USB drive
Vulnerable APC UPS units are used in approximately eight out of 10 companies, so malicious exploitation of these vulnerabilities could have a major impact on various industries. To increase the risk, Armis points out that the reported TLS failures appear to be much more serious than previously thought, as they could be exploited in zero-click attacks without the interaction of the target user.
Users of affected devices are advised to adhere to the recommendations issued by the firm to mitigate the risk of exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











