Researchers at security firm Sophos recently reported a hacking campaign related to the ProxyLogon and ProxyShell exploits for the exploitation of an unpatched Microsoft Exchange server. This compromised server was used for the mass distribution of Squirrelwaffle, a malware loader delivered via email threads as a method of deceiving employees in the affected organizations in order to commit electronic fraud.
About Squirrelwaffle, the researchers mention that this is a malware loader distributed as a malicious Microsoft Office document in spam campaigns. This tool allows threat actors to gain access to the victim’s system and facilitates the delivery of malware variants for later attack stages, including phishing and banking fraud.
If a target user opens an email with an infected attachment and enables macros, a Visual Basic script is executed for the Cobalt Strike Beacons download, giving hackers full control of the vulnerable system.
Although this is a well-known hacking variant, Squirrelwaffle’s latest operation stands out on its own merits. While conventional attacks are cut short by applying security updates, the use of email threads in this last incident allowed hackers to maintain the attack persistently, so not even the application of security patches stopped the intrusion.
Using the information contained in these emails, the hackers registered a web domain deceptively similar to a legitimate platform, using a small misspelling to avoid detection. Taking the conversation out of the victim’s email infrastructure allowed the attackers to calmly carry out the rest of the process.
The next step only involved sending malicious emails to the conversation, trying to trick finance employees into making transfers to bank accounts controlled by the hackers. The use of other methods, such as creating more deceptive domains, made this deception almost undetectable, as seen below:

In a supposed follow-up email included in the thread, reference is made to the new bank details and attempts are made to create a sense of urgency in the minds of the attacked employees. In the operation detected by Sophos, threat actors continued to seek to obtain bank transfers sent fake urgent messages.
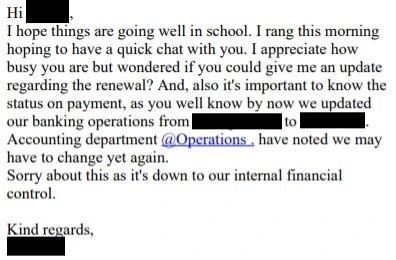
After days of exerting pressure, the hackers are finally informed that the payment is being processed.

According to Sophos, the theft was about to take place, although one of the financial institutions involved detected signs of electronic fraud and the transfer was interrupted.
This is an even more complex variant of a known attack, so it is necessary to take action on it. To begin with, it is best to apply all the updates available for your system, in addition to applying email security policies that help prevent members of an organization from interacting with malicious content.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











