In its latest security alert, Siemens announced the release of patches to address multiple critical vulnerabilities whose exploitation would allow some models of programmable logic controllers (PLC) to be remotely blocked.
The company fixed a total of 27 vulnerabilities, three of which could be exploited by unauthenticated remote threat actors for the deployment of denial of service (DoS) attacks against some SIMATIC family products.
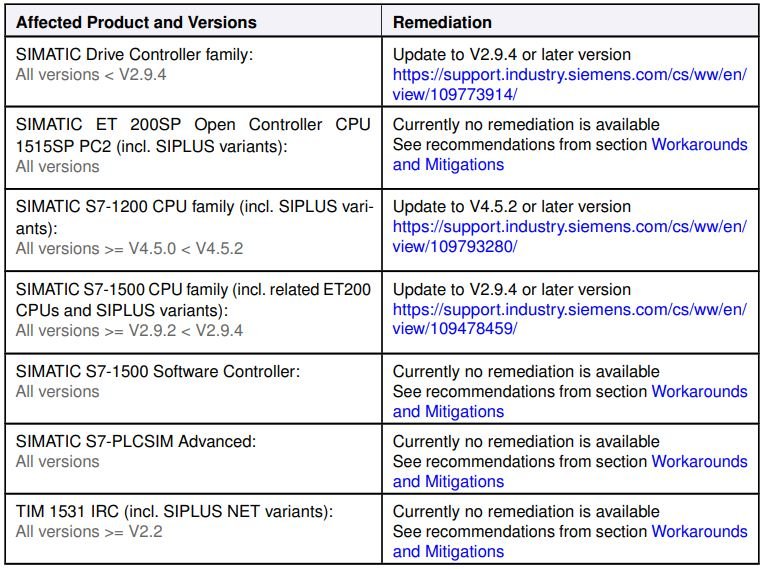
The three most severe faults were identified as CVE-2021-37185, CVE-2021-37204 and CVE-2021-37205 and could be exploited by sending specially crafted packets over TCP port 102 to the affected device. The successful attack would force the interruption of services, which could only be corrected with the restart of PLC devices.
Siemens reports that faults reside in the SIMATIC S7-1200 and S7-1500 PLC products, SIMATIC Drive Controller, ET 200SP Open Controller, S7-1500 Software Controller, SIMATIC S7-PLCSIM Advanced, TIM 1531 IRC communication module and SIPLUS extreme products.
Gao Jian, a security researcher who submitted the report to Siemens, mentions that these are just some of the eight vulnerabilities he has recently reported to the company. The remaining problems continue to be investigated.
Jian explained that the vulnerabilities are related to the OMS+ communication protocol stack used by Siemens products. Siemens PLC products can be protected against unauthorized operations by enabling an access level option and setting a password, although the attack works even if these protections are enabled.
That is why faults can be exploited even with the best protections available for PLC systems: “These flaws can be exploited by malicious hackers with access to the target device on TCP port 102. Exploitation directly from the Internet may also be possible if the PLC is exposed online,” explains the researcher.
A full report is available on Siemens’ official platforms. Administrators of affected deployments should update as soon as possible to prevent exploitation risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











