In cybersecurity, steganography is a technique that allows you to hide snippets of code in a legitimate-looking file, mainly images in various formats and even some documents. This practice is increasingly popular among cybersecurity researchers, since it has been proven that multiple hacking groups have used it in different attacks successfully, so it is better to know how an attack works and how we can prevent it.
This time, specialists from the International Institute of Cyber Security (IICS) will show us some of the most popular steganography tools, used both by cybersecurity experts and hackers from around the world.
Before continuing, we remind you that this material was prepared for informational purposes only and should not be taken as a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
SilentEye
SilentEye is an open source tool used for steganography, mainly to hide messages in images or sounds. According to cybersecurity experts, the tool provides an easy-to-use interface and simple integration process for the new steganography algorithm and cryptography processes through a plugin system.
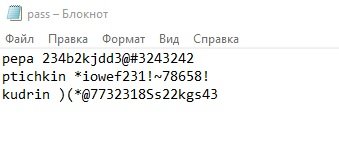
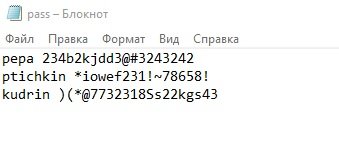
In this example, we have a pass.txt file that contains credentials to access information systems. Using SilentEye, this file is hidden in an image.
The tool can be downloaded from https://silenteye.v1kings.io/download.html?i2. When downloading, click the downloaded EXE file and follow the installation instructions. In addition to Windows, the installation files for Linux and MAC are available for download.
The process of steganography can be divided into these stages:
- Drag the image to the program launch window
- After adding the image, click on the encoding option

- Select the header position as “signature”, and enter a password position to access the file
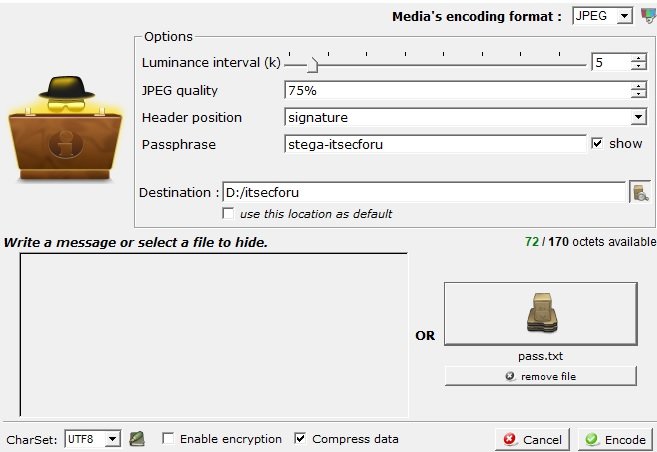
- Select the file you want to hide in the image and click Encode
- The image will be saved in the destination folder specified in the previous step. We can see that the encoded image looks exactly the same and the hidden file is impossible to detect at simpe view
- To decode this image, click on the Decode option

- Select the title position as “signature” and enter the password that was used to encode this image, then select the Decode option
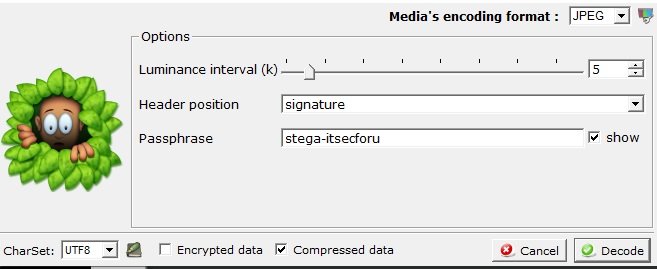
- The decoded file is shown below
iSTEG
This is an open source steganography tool that is used to hide files within a jpeg image. While it’s available only for Mac devices and is a relatively old program, it’s sure to prove to be a great source of learning for cybersecurity enthusiasts.
OpenStego
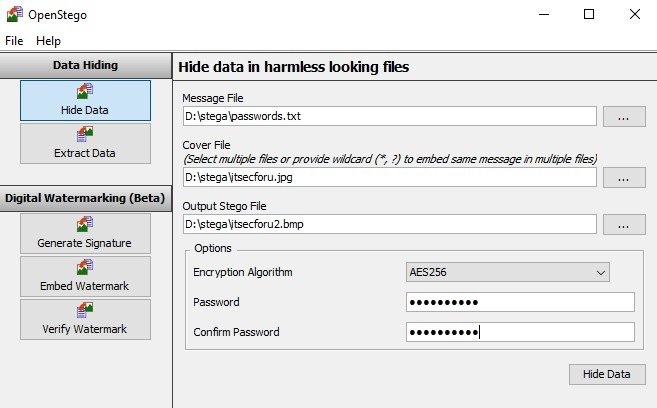
OpenStego is also an open source steganography tool that allows you to hide data in images or apply watermarks and detect unauthorized copies of specific files. The watermark can also be useful when sending the same document to different organizations with labels for each of them, allowing the source of possible leaks to be detected.
To hide data in the Message File field, select the file with the passwords you want to hide in the Cover File field and select the source image that will be the container for the text file. In the Output Stego File field, specify the name of the final image with the secret. Then, select the encryption algorithm (AES256 in this case) and set the password. Then click Hide Date to get the result.
Below we can notice that the image with the attachment is much larger than the original:
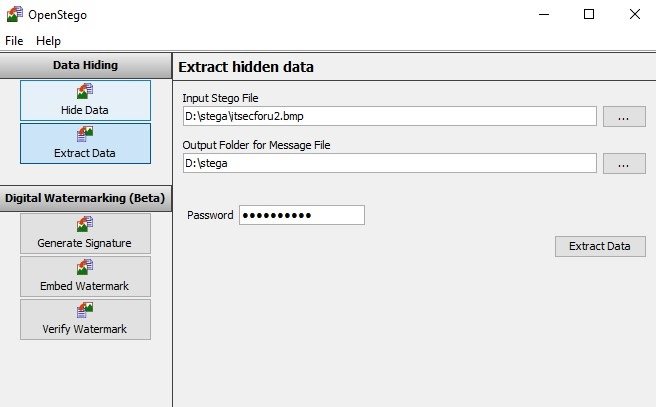
For reverse actions, respectively, on the Extract Data tab, you need to select a file with hidden data, select a path to save the file to the output, enter a password and click Extract Data and get the file passwords.txt.
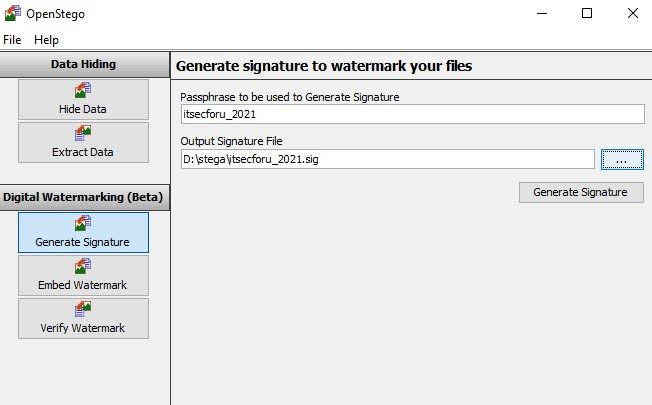
As mentioned above, the functionality of the program also allows to put a watermark with a specific signature. You need to generate a signature file first and then it can be used to mark with water or validate.
You can generate an electronic signature in .sig format:
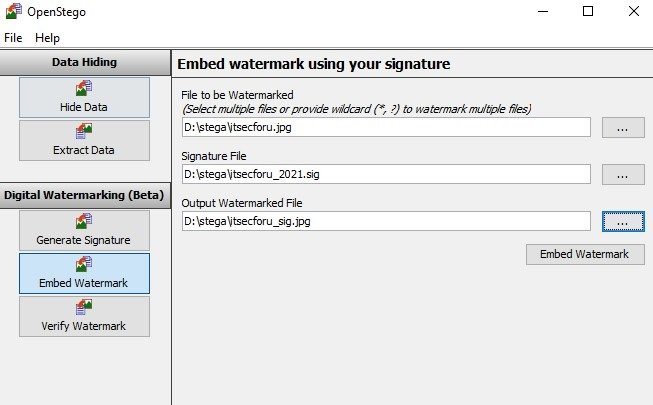
The result of adding the watermark is a signed image file isecforu_sig.jpg:
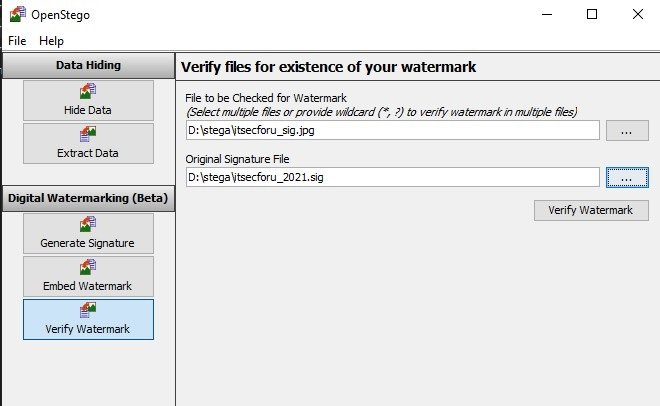
To check the watermark on the Verify Watermark tab, you need to select the file with the watermark and the signature file, respectively:
Open Puff
This is a free steganography software for Microsoft Windows and Linux systems. In addition to images and audio, it works with video and PDF files and includes detailed documentation to understand its use perfectly.
The tool supports image formats such as BMP, JPG, PCX, PNG, TGA, audio formats such as AIFF, MP#, NEXT/SUN, WAV, and video formats such as 3GP, FLV, MP4, MPG, SWF, and VOB, in addition to the popular PDF format.
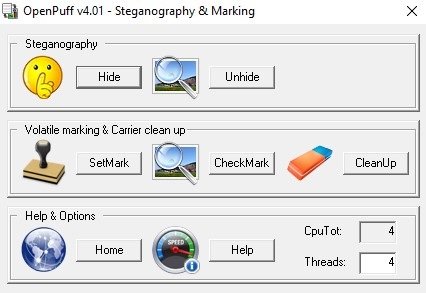
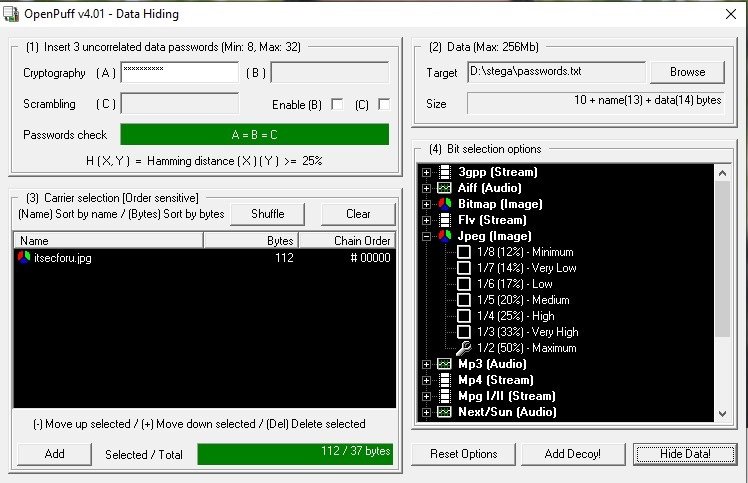
To hide, it is proposed to enter 3 different passwords (A, B and C). However, passwords B and C can be disabled by unchecking the Enable (B) and Enable (C) parameters, so we will do this and enter the password in the A field. Then, in the Data block, select the file with passwords passwords .txt. In the third step, select the itsecforu.jpg image file as the media. Next, select the output file format and persistence, click Hide Data, and select a directory to save the file with hidden data.
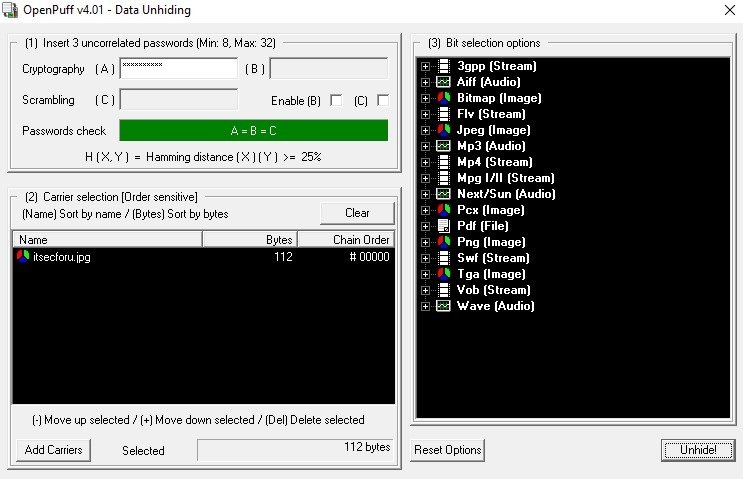
To extract the file, you need to select Unhide from the start menu, enter the password in block A, select the itsecforu container.jpg and click Unhide:
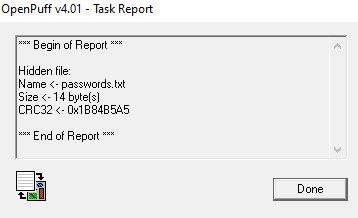
As you can see, we get our password file.txt
The file tagging process is also simple and straightforward, so we won’t consider it.
Steghide
This is a program to hide data in various types of images and audio files. We wrote about this in the article “Steganography in Kali Linux – Hiding data in an image”. According to cybersecurity experts, the principle of operation is similar when working on the Windows operating system.
Run the utility from the command line and to see all available options:
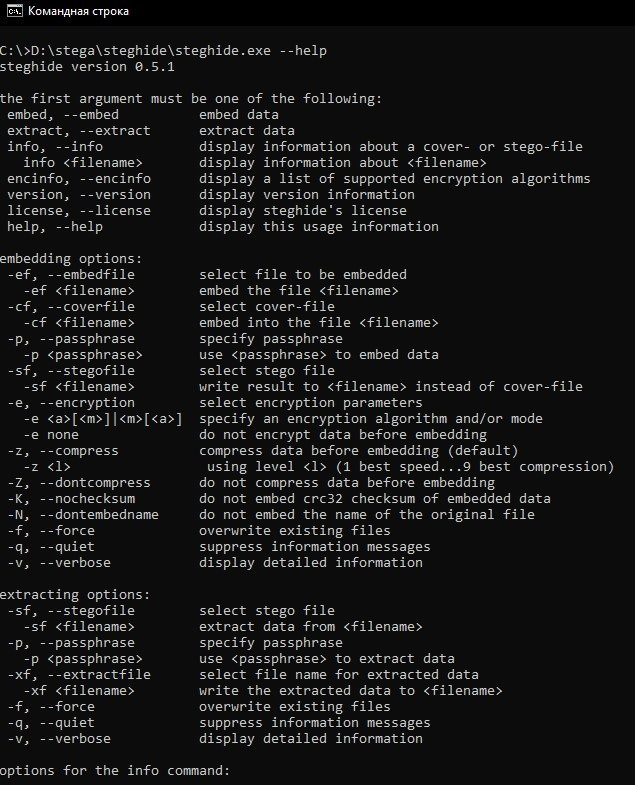
To hide the password.txt file in the itsecforu.jpg image file, enter the following command:
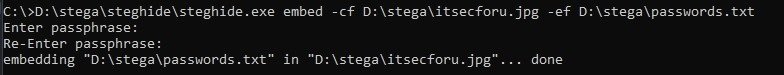
steghide.exe embed -cf D:\stega\itsecforu.jpg -ef D:\stega\passwords.txt
Now the password and password confirmation are entered and the itsecforu file is obtained.jpg already with hidden data
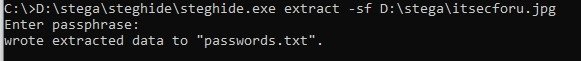
Accordingly, to extract hidden data, enter the following command:
steghide.exe extract -sf D:\stega\itsecforu.jpg
Enter the password to get the password.txt file:
Spammic
Spammic.com is a website for converting messages into spam. This site gives users access to a program that turns short messages into spam in the form of a coded message, cybersecurity specialists note.
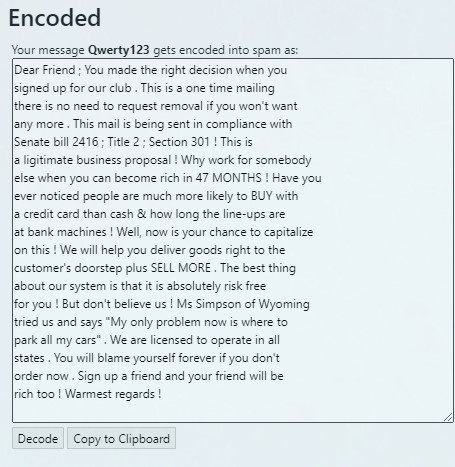
The tool would allow users to send confidential information via email with the confidence that threat actors will not identify the content, sharing it in a secure way.
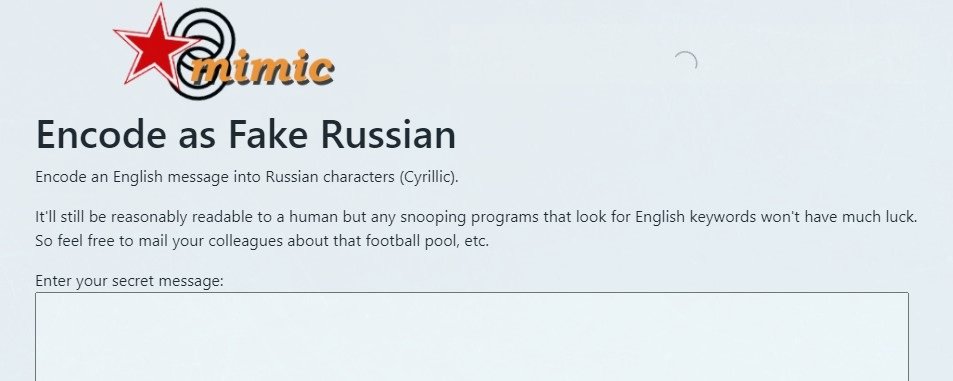
This website includes a function known as “Encode as Fake Russian”, which allows you to encode a message in English with Cyrillic characters, readable enough for an operating person impossible to decipher for automated systems.
Cybersecurity experts recommend paying attention to the right resources.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











