On Monday, Microsoft announced that it has decided to disable Excel 4.0 macros by default in the latest version of the application to keep users protected against some security risks associated with this feature.
As you may already know, a macro is a series of commands to automate a repeated task and that can be executed when you have to perform the specific task. These macros can be used for malicious purposes and do not need to be manually enabled to view or edit a file.
Using macros, cybercriminals will try to trick unsuspecting users into enabling macros and then use that functionality as part of the attack.
This move is an attempt by the company to counter a spike in ransomware and other malware variants infections that abuse Excel 4.0 macros as part of an initial infection. Hackers, mainly nation-state sponsored groups, began experimenting with legacy Excel 4.0 macros in response to Microsoft’s 2018 crackdown on macro scripts written in VBA.
Previously, Excel Trust Center configurations were aimed at organizations that wanted VBA and legacy macros to run through the “Enable Excel 4.0 macros when VBA macros are enabled” setting, thus allowing administrators to control macro behavior without affecting VBA macros.
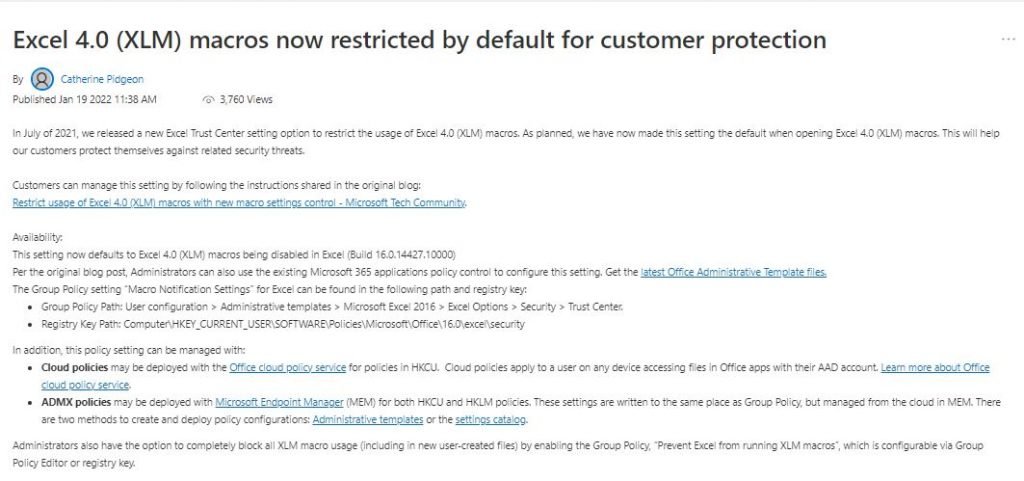
Macros are now disabled by default in Excel, including builds 16.0.14427.10000 and later. Users will also be able to modify settings in the Microsoft 365 app policy control.
In addition to these settings, Microsoft added the option to manage policy settings in the Office Cloud Policy Service, which applies to users who access Office applications from any device using Active Azure Directory accounts.
Finally, to block XLM across the board, administrators can configure Group Policy to prevent Excel from running XLM. Implementing these measures should help administrators mitigate VBA and XLM malware threats through the policy.
Microsoft addressed the antivirus aspect of defense through an integration between Antimalware Scan Interface (AMSI) and Office 365 for additional protection of antivirus solutions.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











