Cybersecurity specialists report the detection of a new ransomware variant apparently operated by FIN8, a dangerous hacking group with financial motivations and a focus on point of sale (PoS) engagement. Dubbed as White Rabbit, this new malicious development was spotted by Michael Gillespie, a ransomware research specialist and founder of the No More Ransom cybersecurity initiative.
Trend Micro experts were also able to analyze this new variant, discovering that the ransomware executable is a payload of just 100 KB, plus it requires a password for its decryption. After its execution, White Rabbit will start scanning all the folders of the infected device, encrypting specific files and showing the ransom note to the victim for each encrypted file.
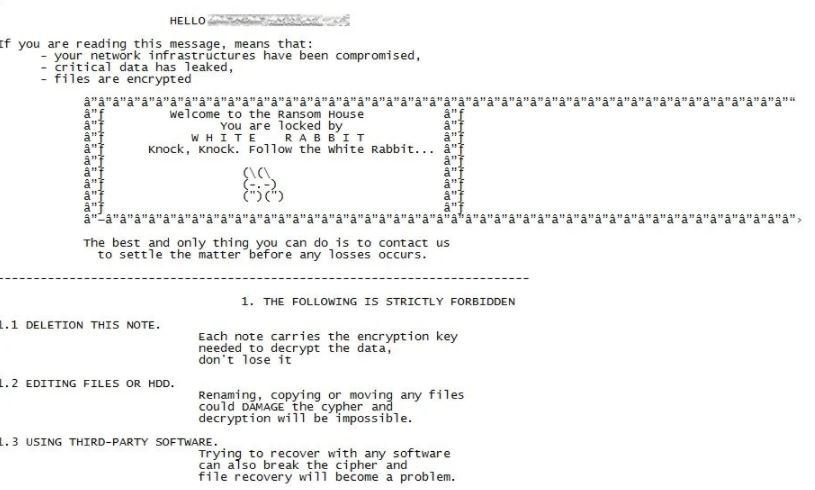
Encryption of affected devices also affects removable drives and other devices connected to the same network. In addition, the ransom note mentions to the victim that their files were extracted, threatening to sell this data if payments are not met.
The hackers also show a four-day limit for the victim to pay the ransom; the note mentions that, if users do not make the payment, their data will be sent to the data protection authorities, generating fines for violations of the General Data Protection Regulation (GDPR).
The hackers’ payment platform, hosted on Tor, displays a homepage showing some files stolen from victims, as well as including a chat section to communicate with threat actors.
Experts add that the link between this ransomware operation and the FIN8 hacking group can be seen in the implementation of the malware, since in both cases the use of a custom backdoor stands out and that it receives maintenance on a regular basis.
At the moment the scope of this malicious campaign is unknown, although it is believed that the operators of White Rabbit have kept a low profile until now, leaving for later the deployment of a campaign of massive exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











