Cybersecurity specialists from Intezer reported the detection of a new cross-platform malware variant capable of infecting Windows, macOS and Linux systems. Dubbed as SysJoker, the malware is highly evasive and even VirusTotal has trouble identifying iterations for Linux and Mac systems.
This malware variant was first identified in mid-2021 during a cyberattack targeting a Linux-based server operated by a renowned educational institution. An in-depth analysis revealed that SysJoker also included modules for Mach-O Windows PE, according to information obtained from its C&C server.
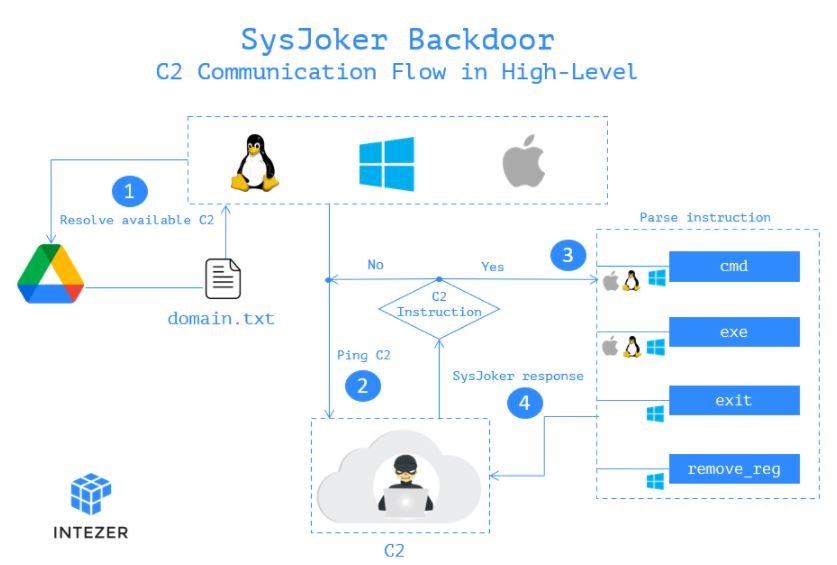
In the process of intrusion to exposed systems, SysJoker poses as a system update, generating its C&C connection by decoding a string extracted from a text file hosted in Google Drive. Experts mention that the C&C changed three times during its analysis, showing that the attack is still active and has been monitoring the affected systems.
The malware is written in C++ and the detected samples are adapted to the vulnerable operating system; as mentioned above, VirusTotal does not detect samples for macOS and Linux. SysJoker was loaded into VirusTotal with the .ts suffix, used for TypeScript files. A possible attack vector is through an infected npm packet.
The researchers recommend reviewing your full report to check for indicators of compromise or weaknesses in these systems that may facilitate the entry of malware. If a compromise is detected, affected system administrators are encouraged to implement any of the following:
- Stop any SysJoker-related processes, remove the relevant persistence mechanism and all files linked to the malware
- Try to find out what the hackers’ entry point was to know if a server has been infected with SysJoker
- After deleting these files, perform a memory scan to verify that your system has removed the malware completely
SysJoker isn’t the only cross-platform malware detected recently. In September 2021, a group of experts identified Vermilion Strike, a powerful malware variant capable of infecting Windows systems and virtually any Linux distribution.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










