Cybersecurity specialists report the detection of at least eight critical vulnerabilities in 16 URL parsing libraries that would allow threat actors to deploy denial of service (DoS), remote code execution (RCE) and sensitive information leaking attacks in various web applications. As these flaws reside in web packages written for all kinds of deployments, the problem could extend to thousands of web applications.
According to the report, the flaws lie in the following developments:
- Flask, a micro web framework written in Python
- Video.js, an HTML5 video player
- Belledonne, a free VOIP and IP video calling platform
- Nagios XI, for monitoring networks and servers
- Clearance, for Ruby password authentication
As you may recall, URL parsing is the process of splitting the different components of a web address to properly route traffic through different links or to different servers. URL parsing libraries are imported into applications to fulfill this function and are available in various programming languages.
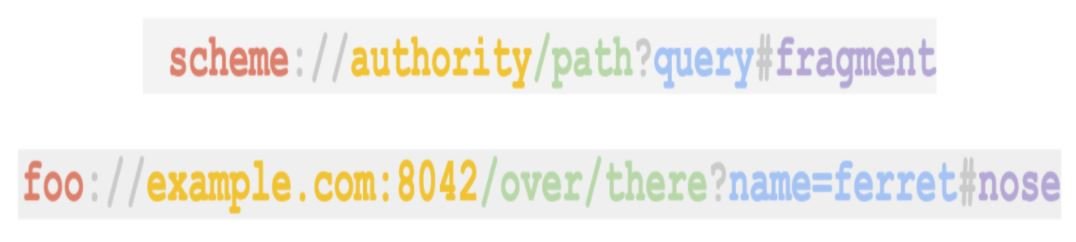
The components of a URL are known as schema, authority, path, query and fragments, which fulfill certain functions for their correct operation.
In their research, the experts found that flaws exist because of differences in the way each library performs this analysis. According to the report, the flaws reside in the following URL parsing libraries:
- urllib (Python)
- urllib3 (Python)
- rfc3986 (Python)
- httptools (Python)
- curl lib (cURL)
- Wget
- Chrome
- Uri (.NET)
- URL (Java)
- URI (Java)
- parse_url (PHP)
- url (NodeJS)
- url-parse (NodeJS)
- net/url (Go)
- uri (Ruby)
- URI (Perl)
The analysis revealed a total of eight critical vulnerabilities in third-party web applications using these libraries. At the time of writing, all flaws had been addressed, except for those residing in versions of Flask that have ceased to receive support. The following describes the flaws detected:
- CVE-2021-23385: Open redirection in Flask-security (Python)
- CVE-2021-32618: Open redirection in Flask-security-too (Python)
- CVE-2021-23401: Open redirection in Flask-User (Python)
- CVE-2021-23393: Open redirect triggered in Flask (Python)
- CVE-2021-33056: Denial of Service (DoS) in Belledonne SIP Stack (C)
- CVE-2021-23414: Cross-site script (XSS) error in Video.js (JavaScript)
- CVE-2021-37352: Open redirection in Nagios XI (PHP)
- CVE-2021-23435: Open Authorization Redirection (Ruby)
Although these are all the flaws reported in this research, experts mention that the appearance of many other security flaws should not be ruled out, including server-side request forgery (SSRF) bugs and open redirection flaws, which would allow the deployment of sophisticated phishing campaigns and other hacking variants.
Users of affected deployments should carefully analyze all potential risks when using the affected URL parsing libraries, in order to configure the necessary security measures to prevent malicious exploitation of these errors.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











