As of this morning, multiple users of the LastPass password management tool began reporting that their master passwords were compromised after receiving a warning about login attempts in unknown locations. These email notifications also mention that access attempts may have been blocked.
Reports of compromised master passwords have been piling up for hours across social platforms like Facebook, Twitter and Reddit.
Senior Director Nikolett Bacso-Albaum said LastPass is investigating recent reports of possible malicious activity, determining that this is related to a common bot campaign. Apparently, threat actors are using users’ email addresses to try to access their online accounts arbitrarily using the well-known credential stuffing attack.
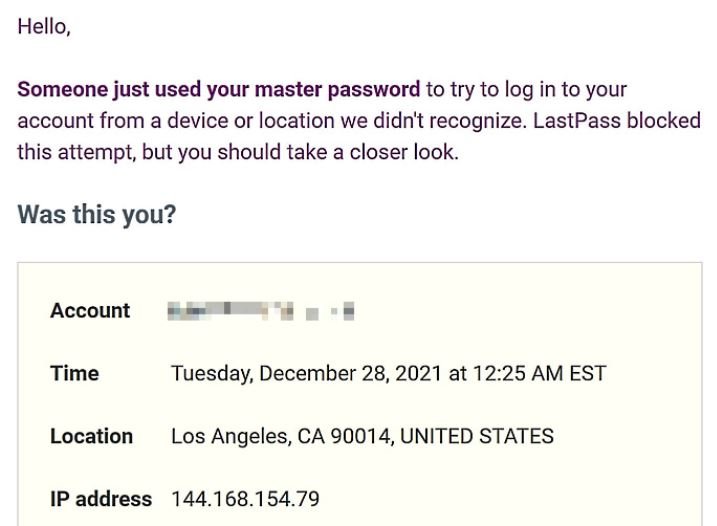
Even though these access attempts have been unsuccessful, users claim that their master passwords are unique to LastPass and should not have been found in separate cybersecurity incidents. The company does not yet seem to have an answer to this question.
LastPass did not add any details about how cybercriminals obtained these records, although researcher Bob Diachenko recently reported the detection of thousands of the platform’s credentials during the analysis of another leak. At the moment the picture seems complicated, as affected customers can’t even disable their LastPass accounts; when a user tries to do this, an unknown error message appears.
Given this situation, users of the platform are advised to keep abreast of any new updates on the incident.
This isn’t the first time LastPass users have suffered a similar incident. Two years ago, the company announced the fix of a critical vulnerability in the password manager Chrome extension that could have allowed malicious hackers to steal credentials last used to log into a website. Although the bug was addressed shortly, it left a very bad precedent for the company.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











