Cybersecurity specialists report the appearance of a new toy with Bluetooth capabilities whose malicious use would allow threat actors to deploy complex espionage tasks against the homes where it is used, affecting both infants and their parents and other relatives.
The device in question is the Chatter Special Edition, which at first glance is just an accessory to add Bluetooth function and a speaker to Fisher Price’s classic toy phone, characterized by having eyes, mouth and wheels, an old favorite in homes around the world.
The launch of this device has been accompanied by an ambitious advertising campaign in which manufacturers enthusiastically announce that this phone is no longer implemented a toy and children will be able to receive phone calls through the speaker and Bluetooth connection.
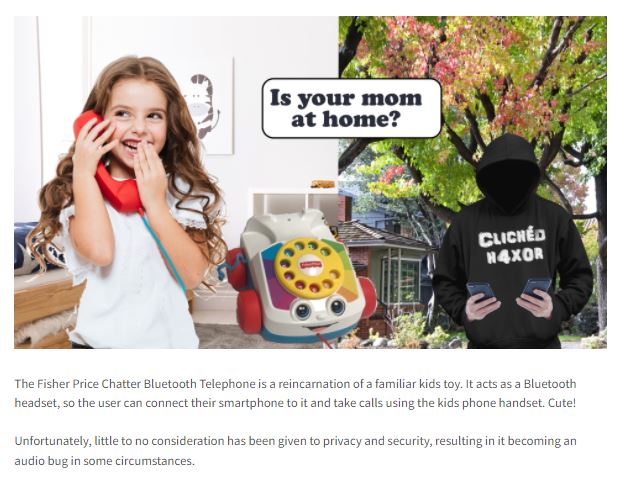
The 2021 version of the device connects to a smartphone and can be used as a speaker or to make calls. To the surprise of many, the device’s rotating markup does work, unlike its predecessors. This all sounds great, although we must be careful with any technological device, including toys. According to the security firm PenTest Partners, Chatter has severe flaws that could turn it into a spying smartphone.
The researchers mention that Chatter uses a classic Bluetooth protocol without sufficient security measures, which means it accepts any pairing requests. In other words, any actor in the Chatter range could plug in a Bluetooth device and tune in to whatever is said within range of the Chatter’s microphone.
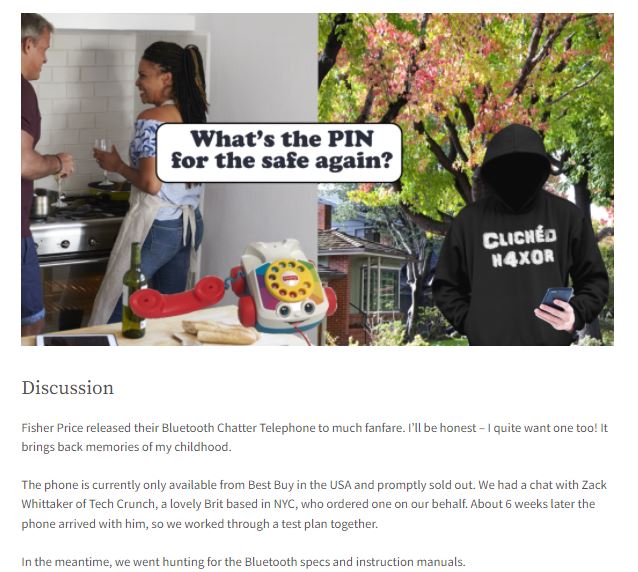
Other interesting findings from PenTest Partner include:
- A threat actor in a nearby location could use the phone to talk and listen to a child in their home
- If the phone’s headset is left off, the device automatically answers any calls to a connected smartphone
- The same attacker can also make Chatter’s phone ring, so a child is likely to respond without adult supervision
The Chatter is already sold out, although fortunately it was only sold in the United States. Another piece of good news is that the toy phone, with no technological capabilities, is available almost globally for less than $20 USD.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











