In its latest alert, the Cybersecurity and Infrastructure Security Agency (CISA) invites VMware administrators to update their deployments to address a critical vulnerability in Workspace ONE UEM. According to the report, this flaw could be exploited to access sensitive information on the affected systems.
Tracked as CVE-2021-22054, the vulnerability was described as a server-side request forgery (SSRF) bug and received a score of 9.1/10 under the Common Vulnerability Scoring System (CVSS). The problem lies in multiple versions of the ONE UEM console.
The Agency mentions that unauthenticated malicious hackers can exploit this vulnerability remotely in relatively simple attacks and without target user interaction: “An attacker with network access to UEM can send their requests without authentication and exploit the bug to gain access to sensitive information.”
The table below shows the affected versions of the console and the mitigation that administrators should apply:
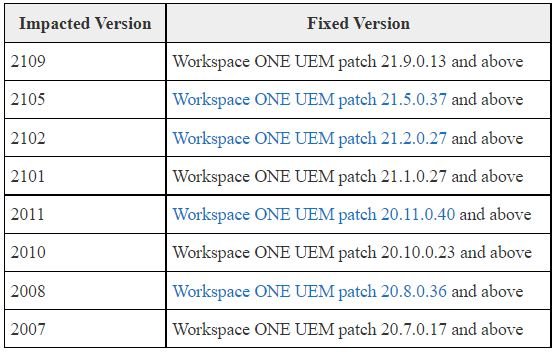
For those users who are not in a position to apply the corresponding updates, VMware issued a series of recommendations to enable a workaround that blocks exploitation attempts.
This workaround requires editing the web.config file in UEM by following the steps described by VMware, in addition to restarting the server instances on which the temporary patch has been applied. The company also provides the steps to validate that this workaround can successfully block malicious hacking attempts.
To verify that this temporary patch has been successfully deployed, you need to open a web browser and navigate to one of the URLs shown below. If in response you get just 404 Not Found messages, the patch has been successfully applied:
https://[UEM Console URL]/airwatch/blobhandler.ashx?url=test
https://[UEM Console URL]/catalog/blobhandler.ashx?url=test
https://[UEM Console URL]/airwatch/blobhandler.ashx?param1=test&url=test
https://[UEM Console URL]/catalog/blobhandler.ashx?param1=test&url=test
VMware concludes by mentioning that resetting IIS will cause the instances being fixed to be logged out, so the final step is to log back in to ONE EMU.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











