After several days of uncertainty and confirmed attacks, the Apache Software Foundation has finally released an update to address CVE-2021-44228, the zero-day vulnerability that caused problems for thousands of online platforms using the Log4j log library. The vulnerability, also known as Log4Shell, can be exploited by forcing Java applications and servers to register a specific string on their internal systems.
While the vulnerability has already been addressed, since it was first reported hundreds of developers expressed doubts about Log4j and how to check its installation on a given system.
Although some developers assume that, being a Java library, if the administrator does not use Java applications his system cannot have Log4j installed. However, cybersecurity experts mention that applications can include their own JRE, so it is not necessary to have installed Java for Java applications to run on the system.
Through Stack Exchange, a developer shared a script that can help other users identify the Log4j installation on a system:
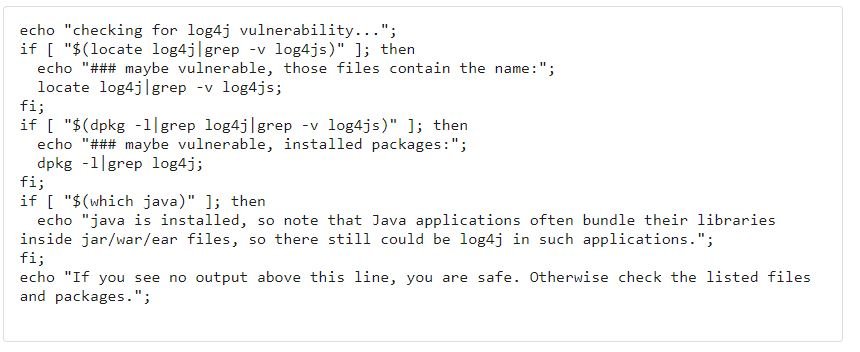
Subsequently, the command shown below is executed:
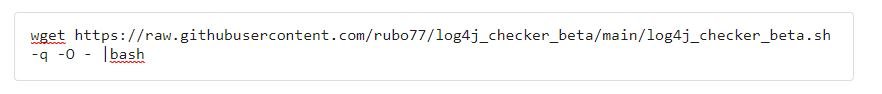
Additional comments are available on GitHub.
The researcher who initially reported the flaw in Log4j also mentions that it is only possible to exploit CVE-2021-44228 if the log4j2.formatMsgNoLookups option in the library settings is set to false. The most recent reports on this issue indicate that the latest version of the affected library keeps this setting set to true, which definitely prevents any attempt at exploitation.
However, threat actors are still looking for vulnerable deployments, so administrators should manually set the feature to true before their systems are affected.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











