Cybersecurity specialists report finding 14 new variants of cross-site leaking attacks (XS-Leaks) affecting some of the most popular web browsers, including Chrome, Edge, Safari, Mozilla and Firefox. Successful exploitation of these attacks would allow threat actors to evade security mechanisms such as the same-origin policy and force the extraction of information from a website in the background.
According to cybersecurity experts, XS-Leaks are based on the use of side channels available on the web to reveal sensitive information about users, such as their data in other web applications, which under normal conditions should be out of reach of hackers.
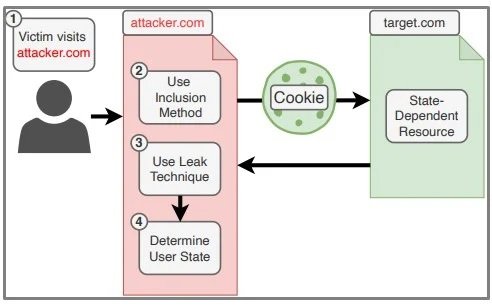
According to researchers at Ruhr-Universität Bochum, they initially detected three features of cross-site leaks and evaluated all inclusion methods and leakage techniques for a large set of web browsers. The three main ingredients of any similar flaw are inclusion methods, filtration techniques, and detectable differences. After creating a model based on the above, the researchers found 34 vulnerabilities, 14 of which were completely new.
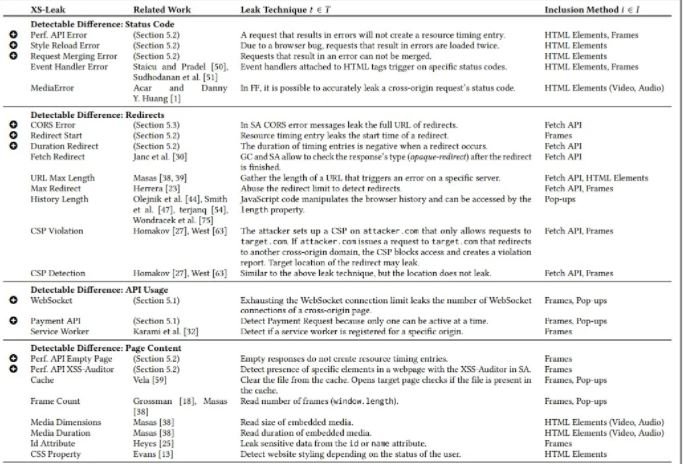
The vulnerabilities found were used in 56 combinations of browsers and operating systems to determine their real scope, in addition to creating XSinator, a web application composed of three components:
- A test website acting as an attacking platform
- A vulnerable Web application that simulates the behavior of a dependent resource
- A database with all the results of the previous tests
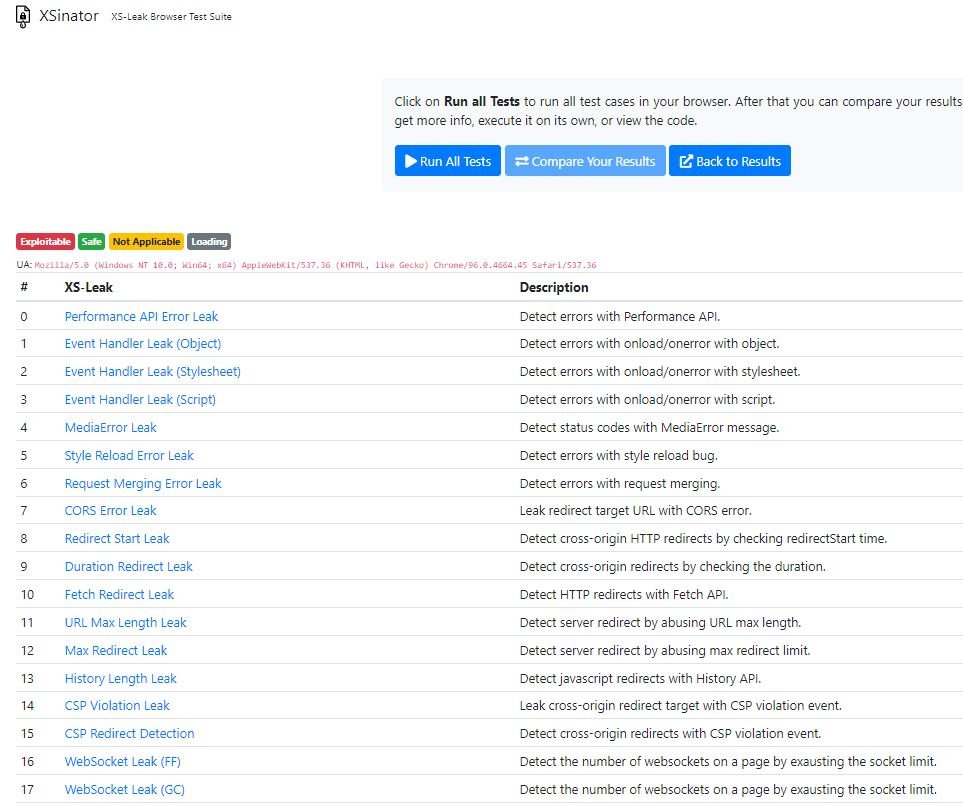
The researchers believe that a potential solution is for browsers to reject all event handler messages, in addition to minimizing the appearance of error messages, creating new history properties, and applying stricter restrictions.
Other possible security measures include using X-Frame-Options to prevent loading HTML iframes and implementing the CORP header to control whether pages can embed a resource. Finally, the researchers reported their findings to the development teams of the affected web browsers. The flaws have already been addressed in the most recent versions of these tools, so users of affected implementations are advised to correct them as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











