Zoom security teams announced the release of patches for two vulnerabilities that could affect Windows, iOS, macOS, Android and Linux users. Reported by Google Project Zero, the flaws reside in the Zoom client for major platforms and their exploitation would allow the deployment of code execution attacks.
Tracked as CVE-2021-34423, the first of the flaws is considered to be of high severity and could also affect other components and software development kits (SDK). According to Zoom, this would allow threat actors blocking the affected services or applications, in addition to forcing arbitrary code execution.
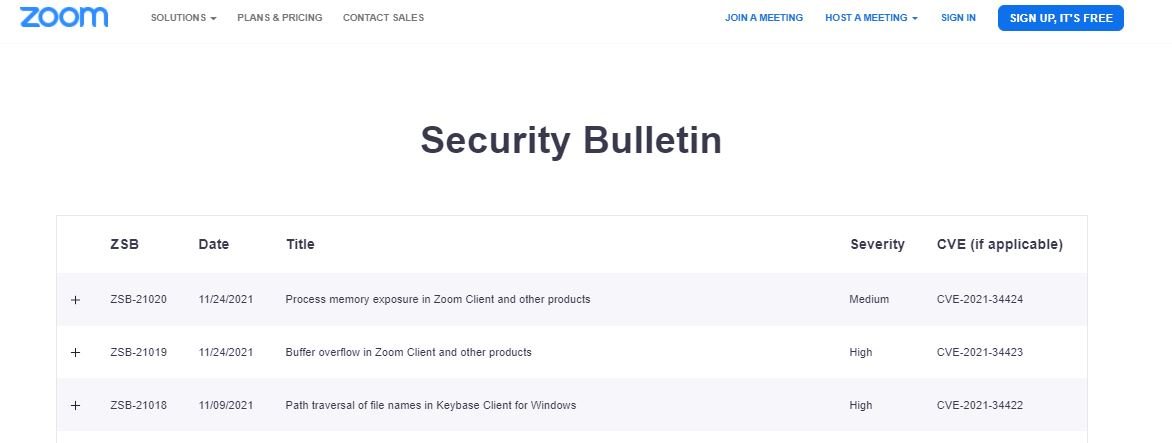
The second vulnerability, tracked as CVE-2021-34424, was described as a memory corruption error that would allow the state of the process memory to be exposed in various processes in multiple products and components: “The flaw could be exploited to obtain information about arbitrary areas in the memory of the affected product,” the report states.
Among the affected products are:
- Zoom Client for Meetings for Android, iOS, Linux, macOS and Windows, versions earlier than 5.8.4
- Zoom Client for Meetings for Blackberry (iOS and Android) versions earlier than 5.8.1
- Zoom Client for Meetings for intune (iOS and Android), versions earlier than 5.8.4
- Zoom Client for Meetings for Chrome, versions earlier than 5.0.1
- Zoom Rooms for Conference Room (Android, AndroidBali, macOS, and Windows), versions earlier than 5.8.3
- Drivers for Zoom Rooms (iOS, Android and Windows) earlier than v5.8.3
- VDI zoom prior to v5.8.4
- Zoom Meeting SDK for Android, versions earlier than 5.7.6.1922
- Zoom Meeting SDK for iOS, versions earlier than 5.7.6.1082
- Zoom Meeting SDK for macOS, versions earlier than 5.7.6.1340
- Zoom Meeting SDK for Windows, versions earlier than 5.7.6.1081
- Zoom Video SDK (iOS, Android, macOS and Windows), prior to versions 1.1.2
- Zoom On-Premise Meeting driver, versions prior to 4.8.12.20211115
- Zoom On-Premise Meeting, versions prior to 4.8.12.20211115
- Zoom On-Premise Recording connector, versions prior to 5.1.0.65.20211116
Zoom also implemented a new automatic update mechanism to the desktop version of the software to help users find and apply security updates in a timely manner, preventing known flaws from being exploited.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











