In its latest statement, the U.S. State Department (DOJ) offered a $10 million reward to anyone who provides information about a group of Iranian citizens accused of deploying cyberattacks in order to intimidate American voters ahead of the 2020 presidential election.
U.S. authorities argue that Seyyed Mohammad Hosein Musa Kazemi and Sajjad Kashian managed to access the records of more than 100,000 American voters, deploying a series of hacking activities to try to influence decision-making and voting trends. As part of these campaigns, the suspects would have tried to hack various websites using a misconfigured computer.

The duo also reportedly used the compromised information to create fake news and distribute it via Facebook and email, trying to alter thousands of voters’ perceptions of the Democratic Party and its members. The hackers used to share the false idea of the Democratic Party trying to compromise e-voting systems in U.S. to commit fraud.
According to the DOJ, these messages sometimes included a YouTube video about an alleged investigation related to e-voting systems, claiming that the Democratic Party was using hackers to create fake ballots and enter illegitimate votes into electronic systems.
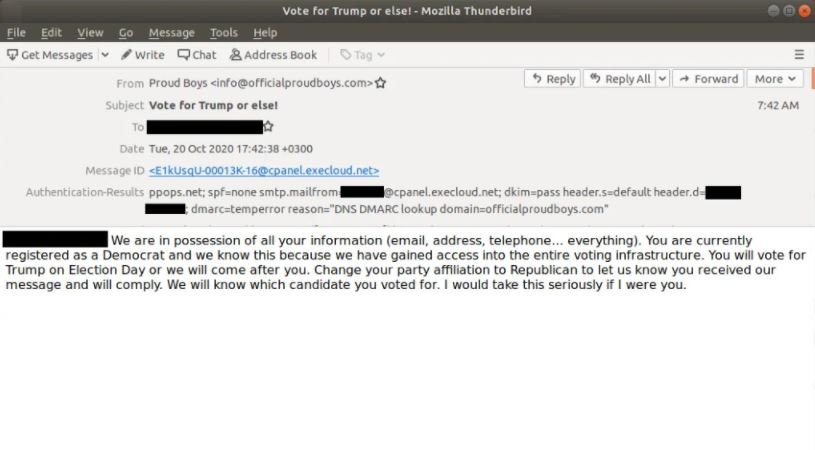
As if that were not enough, the defendants would begin a campaign in which, posing as members of the far-right group Proud Boys, they threatened voters with physical harm if they did not vote for the re-election of Donald Trump.
About the suspects, the DOJ identified them as expert hackers who have collaborated with multiple tech companies and primarily with the government of Iran. Kazemi and Kashian are facing multiple charges, including conspiracy to commit computer fraud, intimidation, intrusion into protected computer systems and computer fraud, among others.
In addition to the aforementioned charges, the Treasury Department of Foreign Assets Control (OFAC) notified the suspects of the imposition of various sanctions against them and against other Iranian citizens, so it is believed that there could be more hacking campaigns related to this group.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











