According to a report by Trend Micro, the hacking group identified as TeamTNT has been attacking Docker servers with exposed REST APIs as part of an ambitious exploitation campaign, resorting to the execution of malicious scripts for the injection of a tool for mining the Monero cryptocurrency.
Apparently, this attack starts with creating a Docker on the vulnerable host using an exposed Docker REST API; subsequently, a malicious image of the Docker Hub accounts under the control of the threat actors is downloaded.
The scripts executed and the tools used by the hackers were sufficient evidence to attribute this campaign to the aforementioned hacking group. The researchers claim to have detected one of the main Docker Hub accounts, actively used by TeamTNT and with more than 150,000 malicious image extractions.
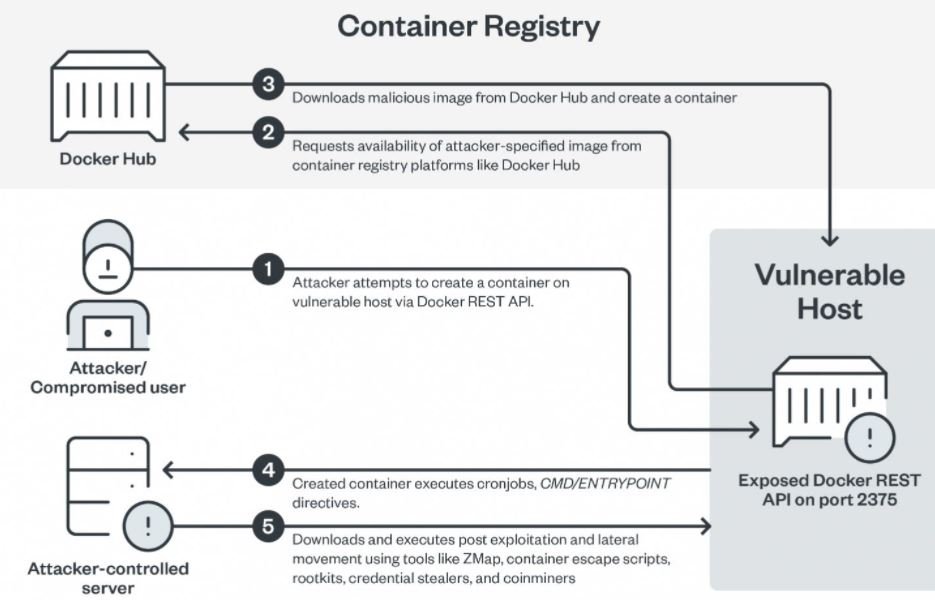
Once the container has been created, it runs cronjobs and recovers various post-exploit tools and side-move tools, container escape scripts, rootkits, credential thieves, and miners. Cybercriminals also scan the web for ports 2375, 2376, 2377, 4243, and 4244 in order to collect details of the target server, including operating system type, container logs, architecture, and the number of CPU cores.
About TeamTNT, experts point out that this is a cryptojacking operation active since the beginning of 2020 and that it aims at Docker installations. Trend Micro has been closely monitoring the activities of this hacking group, finding that this cybercriminal infrastructure can also attack vulnerable Kubernetes implementations.
The attacks described in this article appear to be part of the same hacking campaign, identified as Chimaera. This campaign is aimed at administrators of Windows systems, Linux distributions, and other deployments such as Amazon Web Services (AWS), Docker, and Kubernetes; although their targets may vary, hackers usually use these attacks as part of a cryptojacking campaign.
Chimaera reached its highest activity point in August 2021, when multiple malware samples were detected that at the time had an antivirus detection rate close to 0%. In other words, hackers are constantly evolving the malicious tools used.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











