Cybersecurity experts recently detected a new way to hijack WhatsApp accounts and take control of users’ contact lists that could affect millions of people. The good news is that you can prevent falling victim of this attack variant.
Before get started, users should know the tactics used by threat actors: The attack often starts with a text message posing as a contact on the users’ lists. Thus, the user receives the text containing a six-digit number from the WhatsApp platform arriving from the chat of their contacts: “Can you lend me some money? I will return it to you within 2 hours, please”, reads the message sent by threat actors posing as a victim relative or friend. Below we can see an example of this scam, reported by an unknown user in Mexico:
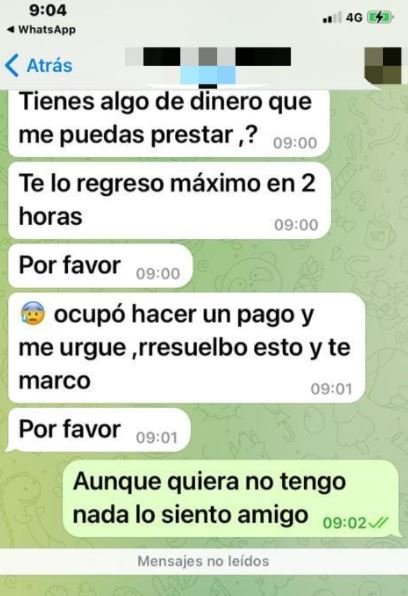
This will ultimately lead to the victim losing some money or having their WhatsApp account hijacked by the hackers, thus it can be used to further malicious tasks.
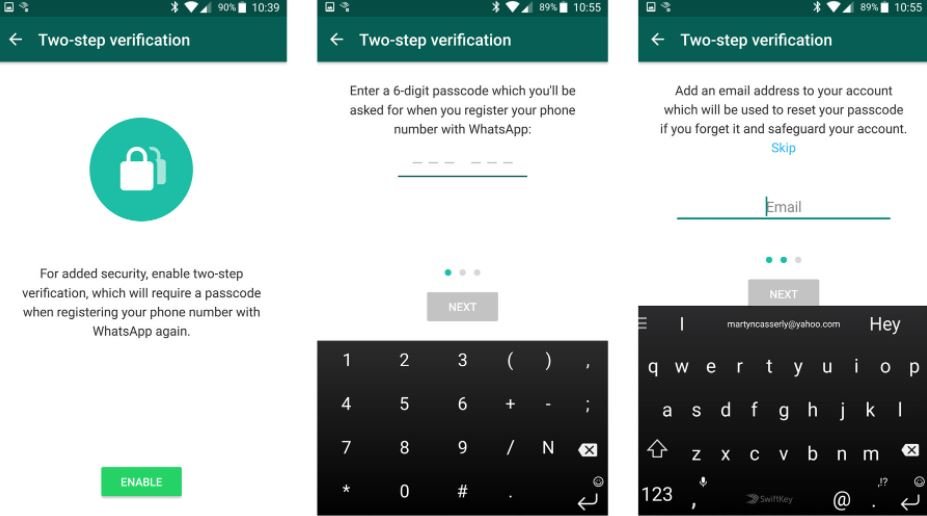
A fast and safe option to keep hackers away from our messaging platform accounts is enabling the two-factor authentication mechanism integrated in WhatsApp, which will request an additional identity validation. This setting can be done directly from your WhatsApp account in less than 5 minutes.
The first step to follow is to go to WhatsApp settings and click on the Account option, which gives the option to carry out the two-step validation. Once there you must add a password and an email address to your account to be able to reset your pin in case you forget your password and thus protect your account.
The reason for the hack is still unknown, however, the most frequent reasons are usually to take control over accounts within the platform and then extort the user to collect a ransom, ask for money, among others.
The problem, which is added to the hack itself, is that the criminal is left with access to all your contacts to repeat the modus operandi and get new victims who fall into his trap, only this time impersonating them.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











