Researchers from the firm Netlab Cybersecurity report the detection of a massive new botnet capable of launching powerful denial of service (DoS) attacks thanks to the detection of more than 1.5 million devices connected to the Internet. Identified as Pink, this botnet is also capable of inserting arbitrary ads into legitimate traffic and operates primarily in China.
Pink is the largest botnet detected since 2015, with scans that have identified up to 1,963,000 active IP addresses associated with this malicious infrastructure in a day. On the other hand, at the beginning of 2020 the CNCERT reported that the bot node IP addresses associated with this botnet exceed 5 million. Home IP addresses are dynamically assigned, so the actual size of infected devices behind this data cannot be accurately calculated, although it is certain that these are millions of devices.
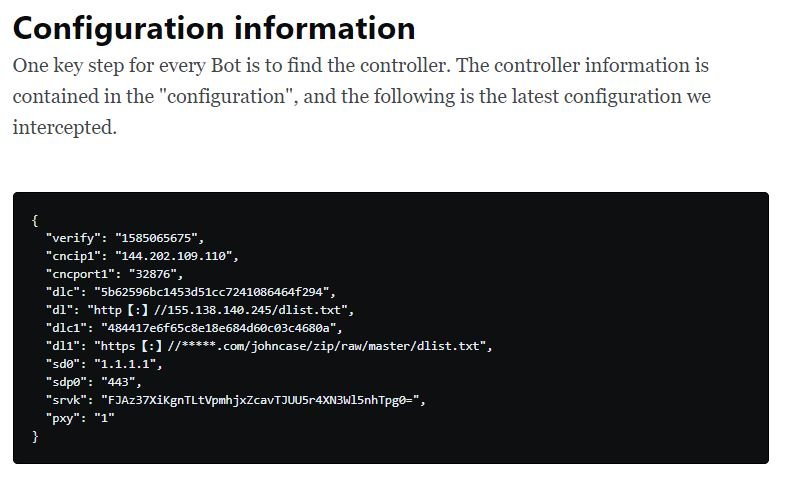
Pink’s first reports came in late 2019, when a researcher shared with some security firms a sample of the malware employed by operators: “From the beginning we found it surprising, since in its peak hour it had a total infection of more than 1.6 million devices, most of them based in China”, the researchers point out.
Pink’s controllers appear to base their operation on a combination of third-party services, P2P and C&C servers, which translates into an architecture resistant to attempts to disrupt their activities, and it is difficult for security firms to detect this malicious activity. Operators have so many resources that every time a service provider tried to address the problem, a botmaster would send firmware updates to disrupt these activities.
In addition, threat actors exploit a zero-day flaw in broadband devices of certain brands with a wide presence in China and other regions of Asia because the malware used by Pink can only compromise MIPS implementations employed by Asian manufacturers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











