Cybersecurity specialists from Abnormal Security report the detection of at least 200 malicious emails as part of a phishing campaign targeting Microsoft Office 365 users. Apparently, the primary goal of the attackers was to intercept login credentials.
An unusual feature of this campaign is the use of QR codes embedded in the content of the email, which supposedly redirect the target user to a voicemail, allowing threat actors to take another approach and prevent victims from having to download attachments or click on suspicious URLs. This technique is known as quishing.
This fraudulent scheme also involved the use of compromised email accounts thanks to the exploitation of a flaw in Outlook. Moreover, threat actors hosted the phishing pages to which they redirect these QR codes in an enterprise survey service.
The first hint of this attack was detected in September, when hackers sent a first version of the message and used a URL link hidden behind an image that appears to be an audio file. Although the method is ingenious, malicious activity was immediately detected and contained.
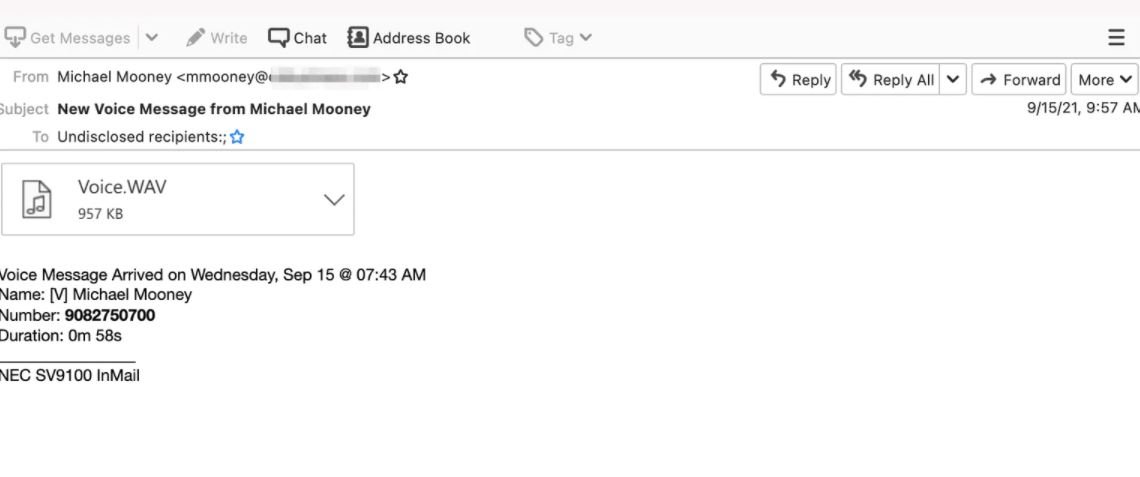
After noticing that this attack failed, hackers began replacing the images with a QR code, an attack variant first detected in mid-2021 by researchers at the British agency Better Business Bureau.
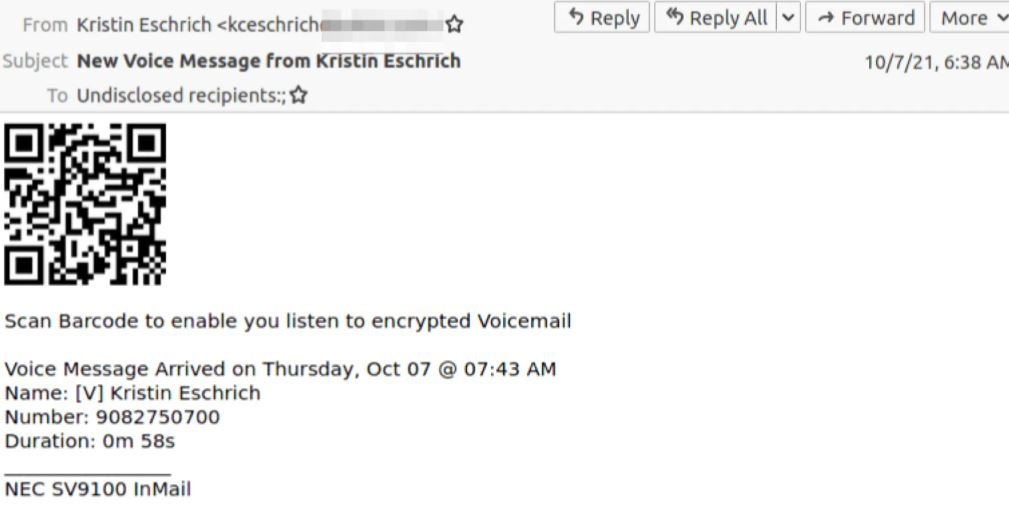
As mentioned above, the operators of this campaign took control of a legitimate Outlook account to evade security controls, resulting in an ingenious cyberattack campaign.
Emails in this campaign may have headers appealing to the target user, as well as contain information such as sender, location details, and IP address.
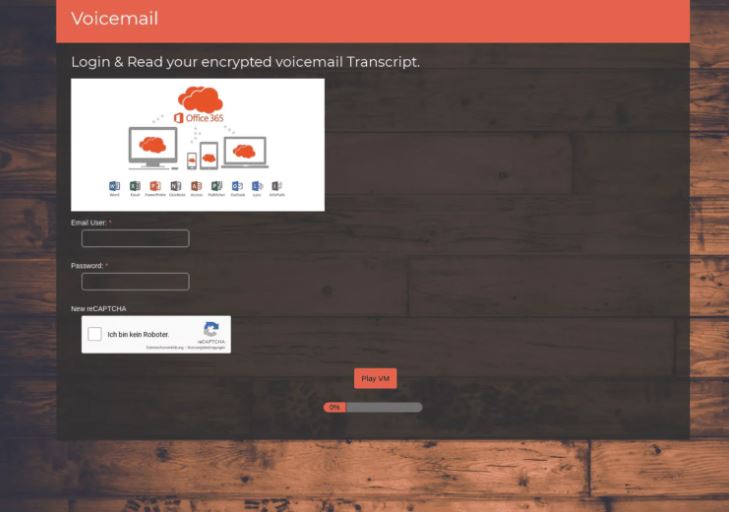
Although phishing messages and pages are in English, attackers use a German reCAPTCHA at the bottom of their phishing page. According to the researchers, each phishing page is connected to several IP addresses, all located in the United States or Germany and registered with Amazon or Google.
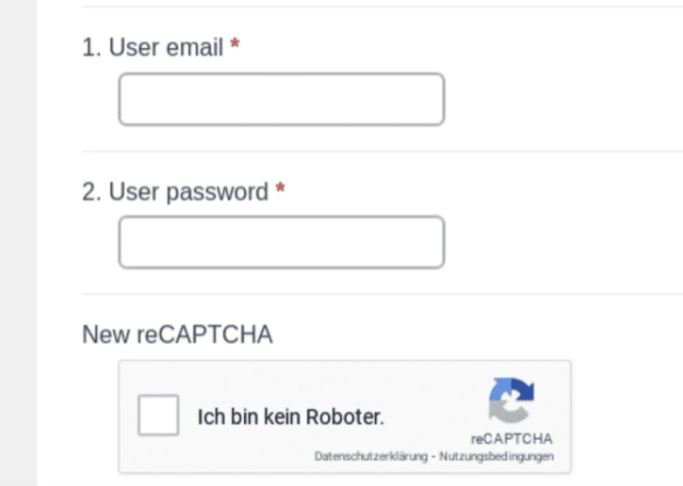
Once on the phishing page, threat actors will try to trick users into entering their login credentials, leading to compromise of the affected Office 365 account. It is important to remember that no company or government entity sends QR codes via email, so if you find a similar message in your inbox you can be sure that it is a scam attempt.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











