The automatic analysis of potential security flaws has become one of the essential tasks for developers, researchers and experts in vulnerability assessment, as it allows taking a proactive approach, thus preventing security threats from generating irreversible damage to a system.
This time, vulnerability assessment specialists from the International Institute of Cyber Security (IICS) will show you how to use Deepfence ThreatMapper, a tool for monitoring security threats and protecting applications in Kubernetes, Docker, Fargate Serverless and cloud deployments. This tool is available at GitHub.
According to experts, among the main features of this security tool are:
- Detection of running processes: ThreatMapper scans all user platforms for pods, containers, applications, and infrastructure. Using this tool will provide a detailed description of the application topology and potential attack surfaces
- Vulnerability detection: ThreatMapper obtains dependency manifests from running pods and containers, serverless applications, applications, and operating system to perform comparisons with vulnerability databases and identify potential bugs
- Vulnerability classification: ThreatMapper classifies detected vulnerabilities according to current scoring systems and other indicators, such as exploitation method, attack surface availability, and risk in the wild
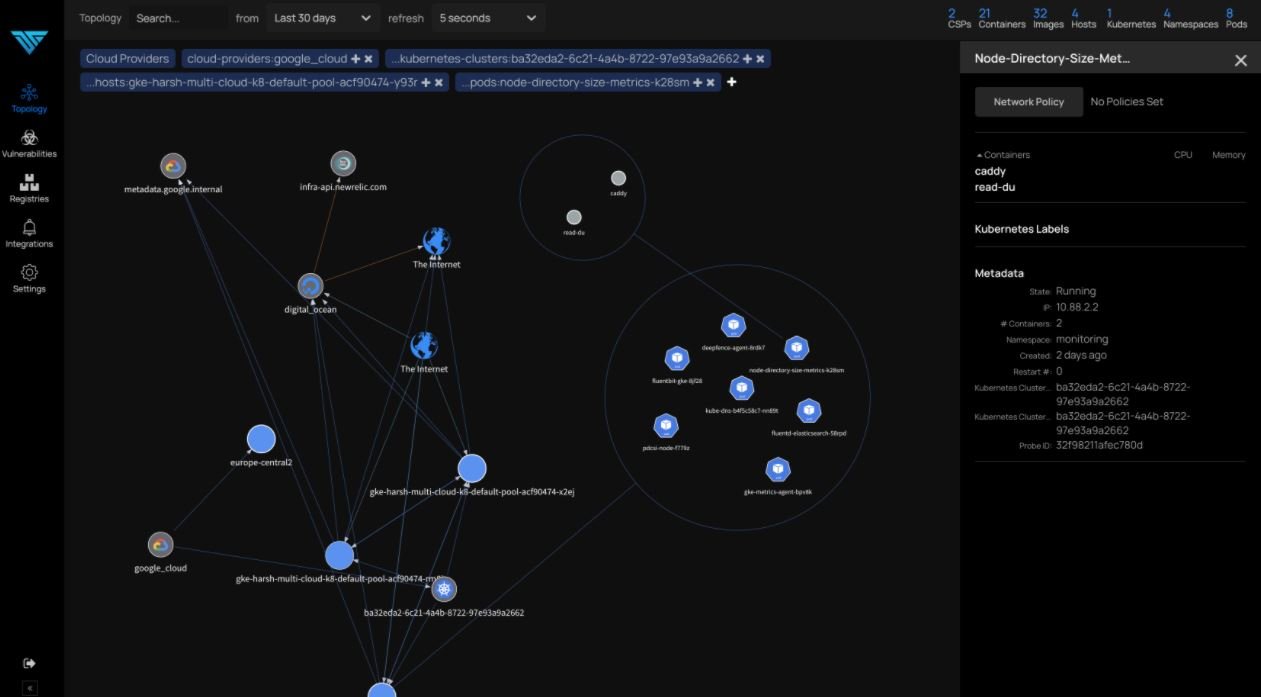
What’s inside Deepfence ThreatMapper?
Vulnerability assessment experts mention that Deepfence ThreatMapper has two components: Deepfence Management Console and Deepfence Sensors. While the first element calculates the topology of the analyzed applications and performs threat mapping, the sensors are deployed on the analyzed platforms and send telemetry to the console.
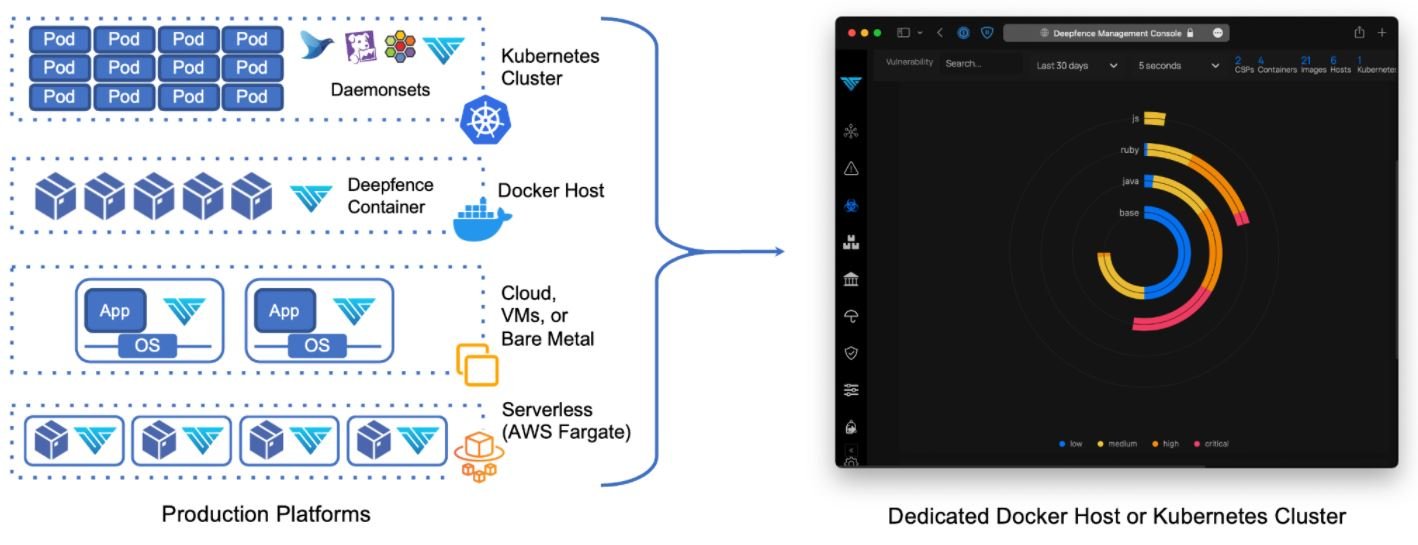
Below we will analyze more in depth both components of Deepfence
Deepfence Management Console
As the name suggests, this is a console that acts as a standalone application, deployed as a fleet of containers. It must be deployed on a single docker host or on a dedicated Kubernetes cluster. The console is self-contained and exposes an HTTPS interface for API management and automation, vulnerability assessment experts say.
The console features advanced capabilities, including:
- Manage users with console access
- Visualization of Kubernetes clusters, virtual machines, containers and images, running processes and network connections in real time
- Vulnerability assessment in containers and running applications
- Scan container logs for vulnerabilities to review workloads before deploying
- Scanning image builds during CI/CD pipeline, compatible with CircleCI, Jenkins and GitLab
The tool also supports multiple production deployments simultaneously for better visualization and scanning of workloads.
Deepfence Sensors
This second component is deployed directly to the user’s production platforms and functions as a set of sensors that securely communicate with the console to receive instructions on scans and forwarding of telemetry data.
According to experts, the sensors support a variety of production platforms, including:
- Kubernetes
- Docker
- Virtual machines
- AWS Fargate
System requirements
Installing the DeepFence Management Console requires our system to meet certain features:
- 4-core CPU
- 16 GB ram
- Disk space of at least 120 GB
- Telemetry and data from Deepfence Sensors on port 8000, protected with firewall
- Administrative access and API on port 443, protected with firewall
- Docker binaries v18.03 or later
- Docker-compose binary v1.20.1
Larger deployments (with 250 or more production nodes) will require additional CPU and RAM resources, vulnerability assessment experts say. For enterprise-scale deployments (more than 1,000 production nodes), the ThreatMapper console must be deployed on a Kubernetes cluster of 3 or more nodes.
On the other hand, our system must meet the following requirements for the correct use of Deepfence ThreatMapper Console:
- 2-core CPU
- 1 GB ram
- Disk space of at least 30 GB
- Linux kernel version 4.4 and later
- Docker binaries v18.03 or later
- Access to the IP address of the Deepfence Management Console by port 8000
Installation
Below, vulnerability assessment experts will show us how to start a Docker-based installation on a single host system:
- Download the docker-compose.yml file to the host system for the console
- Run the following command to install and run the console:

- Open the console in a browser and register a new account. Additional users can then be added at the invitation of an administrator
- Get the CONSOLE API key. Go to Settings – User Management and take note of the API key; this information will be needed to implement the sensors
Once the console has started, it will begin to acquire Intel Threat power data; this can take several minutes or up to an hour. Vulnerability assessment experts recommend checking the status of this process in Settings – Diagnostics.
Below we will review the steps required to install Deepfence Sensors. Before you begin, consider the following factors:
- Make sure you have the Deepfence API key and console IP address available
- Verify that the host systems for the sensors can be connected to port 8000 on the IP address of the console
Install Deepfence Sensors on a Docker host
Run the following command:
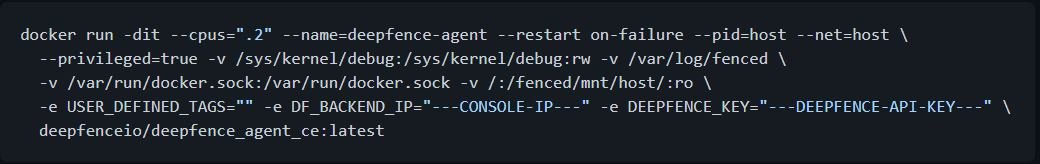
Optionally, the sensor container can be tagged using USER_DEFINED_TAGS =“” in the command above. Labels must be separated by commas.
Install Deepfence Sensors on a Kubernetes cluster
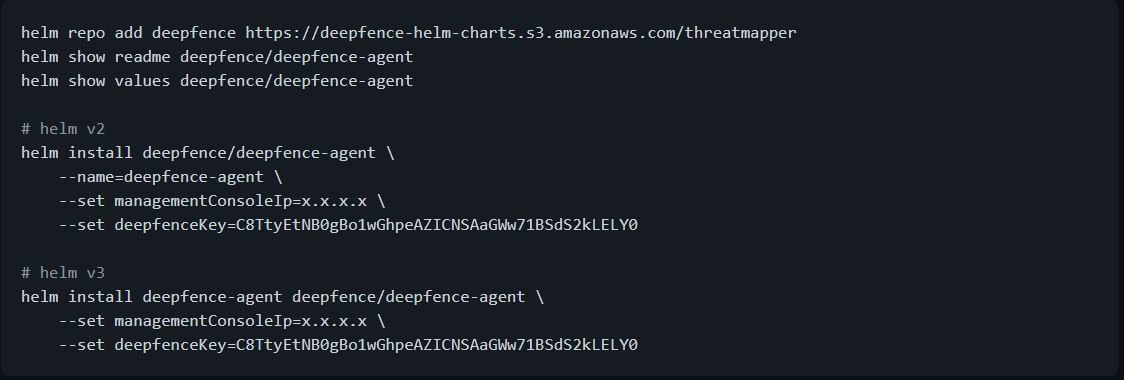
Deepfence Sensors is more easily implemented using the Helm table:
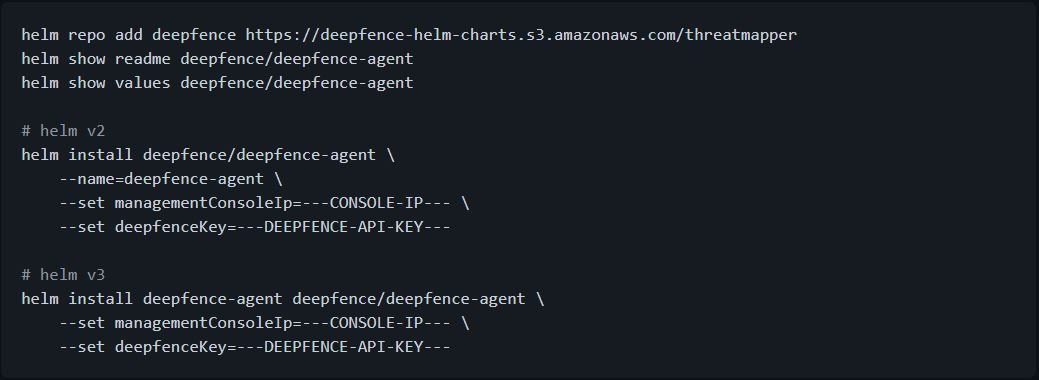
To remove Deepfence Sensors:

Install Deepfence Sensors on Google GKE
According to vulnerability assessment experts, the Deepfence Management Console is installed separately outside the GKE cluster according to standard instructions.
- Connect to your GKE cluster with gcloud shell:
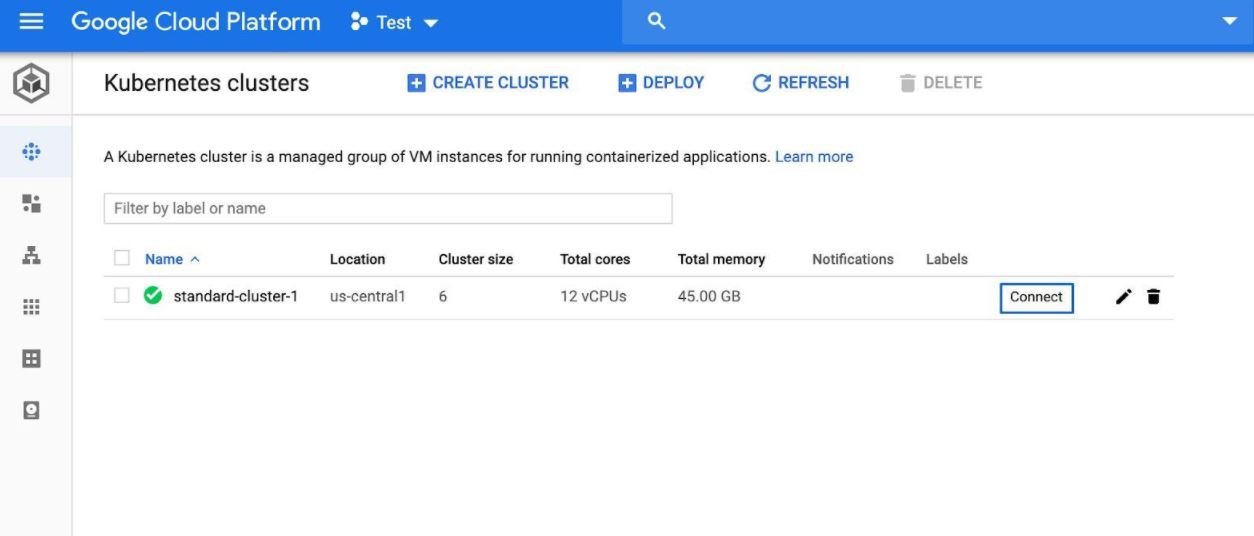
- Grant permissions for the installation with the following command:
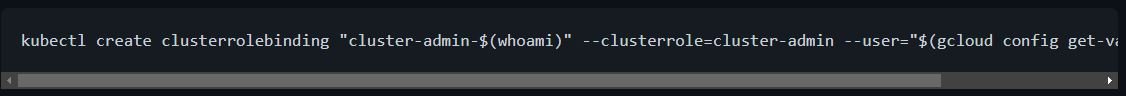
- Start the deepfence agent
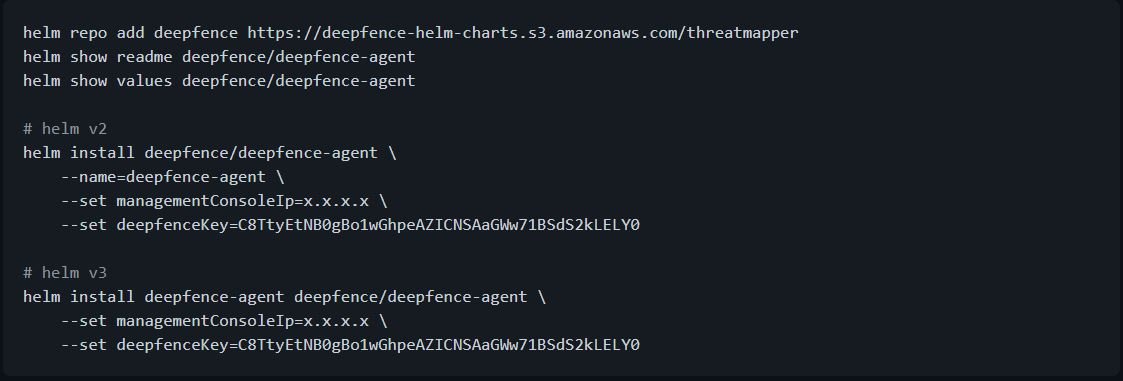
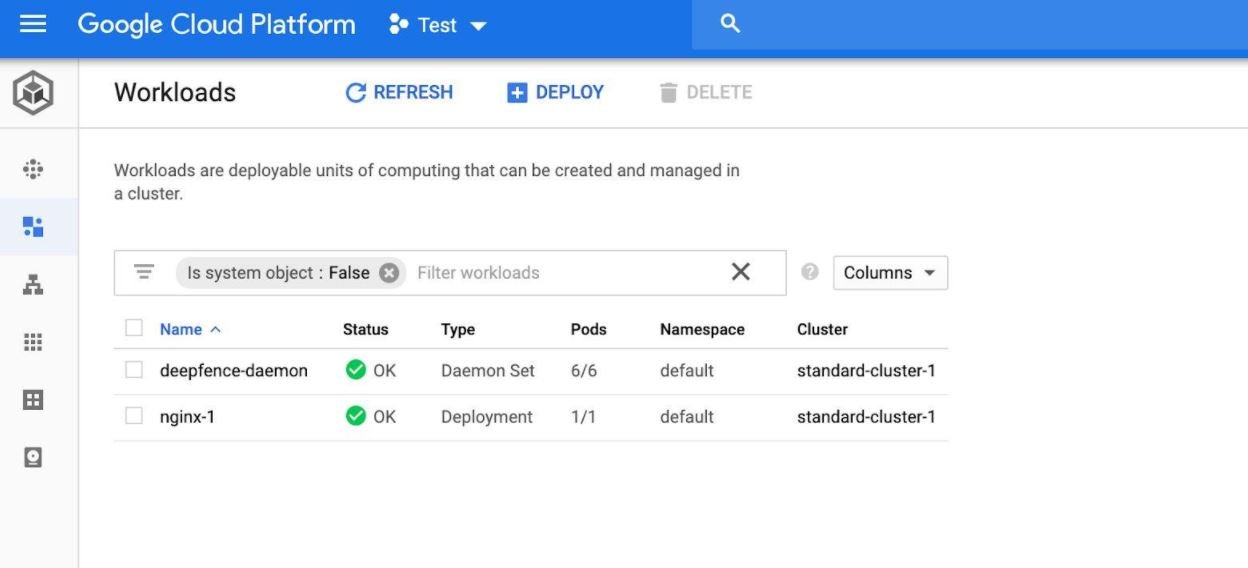
- deepfence-agent-daemon should be visible on the workloads page along with other workloads in the cluster
Install Deepfence Sensors on Azure AKS
The Deepfence Management Console is installed separately outside the AKS cluster according to standard instructions.
Install Deepfence agents by following the steps below:
- Initiate a connection to your AKS cluster
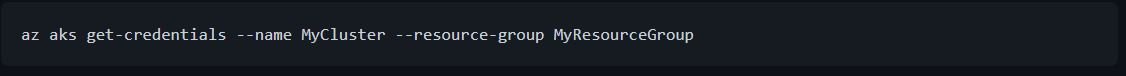
- Start the Deepfence agent
As usual, it is worth mentioning that this material was prepared for informational purposes and should not be taken as a call to action nor should it be used in tests in real environments without the prior consent of the administrator of the target system. IICS is not responsible for the misuse that may occur to the information contained herein.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











