Cybersecurity specialists have confirmed that Apache OpenOffice is affected by a remote code execution (RCE) flaw that has been addressed only in its beta version, so active implementations are still affected. In other words, users of this open source suite with millions of downloads are operating vulnerable versions.
Specialist Eugene Lim released a report containing some details of the vulnerability, identified as CVE-2021-33035. The expert describes the failure as a buffer overflow caused by a file .dbf that overrides a return pointer with a DEP and ASLR evasion, which would trigger the execution of arbitrary commands: “A malicious file opened with this software could lead to the total compromise of the affected system,” he says.
The vulnerability was found during a process of parsing the .dbf file format, which first appeared as part of the dBase II application in 1983. The expert reported that the file format .dbf can use one of two values in its header, fieldLength or fieldType, to determine the buffer size of a database record. It is then possible to assign a buffer using one and use the other to set the size of a copy operation on that buffer, leading to a buffer overflow. The Analysis Code .dbf of OpenOffice is as follows:
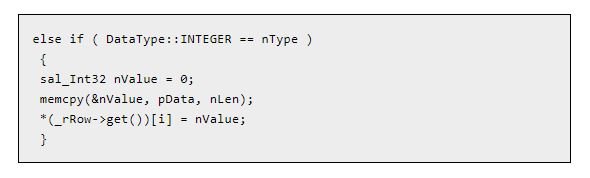
“Here, we can see a sal_Int32-sized (4 bytes) buffer nValue being instantiated for a field of type INTEGER. Subsequently, memcpy copies a buffer of nLen size, which is a value controlled by the attacker, into nValue without validating that nLen is less than or equal to 4, “says the researcher.
By revising its previous payload generator to the entire fieldType (I), it was possible to increase the size of fieldLength to more than sal_Int32 and launch a proof-of-concept (PoC) attack that consisted of opening the file in OpenOffice Calc and generating a crash in the affected application.
The expert adds that the vulnerability also resides in Scalabium dBase Viewer, although this project has already been protected because it is executed by a single developer. Regarding Apache OpenOffice, although the initial disclosure began in May, the complete solution for all users could be ready until the end of this month. In the meantime, users are advised to stay on top of any updates coming from developers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











