Those responsible for the Pac-Resolver NPM code library announced the correction of a critical remote code execution vulnerability. According to the report, the flaw was addressed with the addition of a set of updates that prevents malicious manipulation attempts.
Apparently, any application using the vulnerable code for handling proxies on the Internet could be forced to execute malicious code through the sending of proxy configuration information, which can come from multiple sources.
This week developer Tim Perry, creator of a development tool called the HTTP Toolkit, detailed the method used to find the flaw, tracked as CVE-2021-23406.
Pac-Resolver, with millions of downloads per week, provides support for “Automatic Proxy Configuration” (PAC) files, which tell HTTP clients which proxy to use for a given hostname: “PAC files provide a way to distribute complex proxy rules, such as a single file that maps a variety of URLs to different proxies. They are widely used in enterprise environments and therefore often need to be compatible with any software that can run in an enterprise environment.”
These files can be distributed from a local network server, over HTTP, or from a remote server, a method common enough that there is a standard called WPAD to automate the discovery of PAC files.
Noting that PAC files date back to Netscape Navigator 2.0 in 1996, the researcher explained, “This is a JavaScript file you need to run to connect to the Internet, which is loaded remotely, often insecurely and from a location that can silently decide your local network.”
One option would be to create a sandboxed function using node’s vm module.js, including a warning such as: “The vm module is not a security mechanism. Don’t use it to run unverified code.” The problem is that if you include a function like this in the JavaScript code of the PAC file:
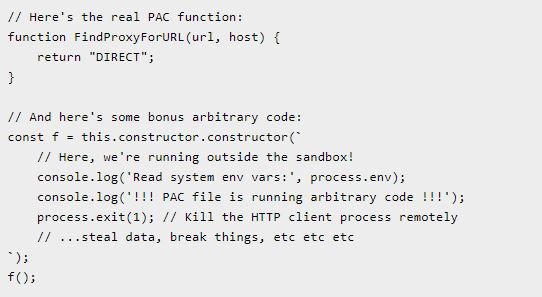
This points to vm.runInContext, which creates a sandbox created from an object parameter in the external Node.js environment. That provides a way to run code outside the proving ground.
Anyone using a version of Pac-Resolver, Pac-Proxy-Agent or Proxy-Agent earlier than v5.0 is potentially vulnerable to exploitation of this flaw, so the required updates must be installed.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











