Cybersecurity specialists report the detection of a critical vulnerability impacting tens of millions of Internet of Things (IoT) devices. Tracked as CVE-2021-2837, the flaw would allow hackers to access audio and video streams from affected devices and received a score of 9.6/10 according to the Common Vulnerability Scoring System (CVSS).
The report was prepared by the security firm Mandiant and presented to the Cybersecurity and Infrastructure Security Agency (CISA).
According to the report, the exploitation would allow threat actors to compromise a vulnerable IoT device remotely in order to access live audio and video, in addition to extracting credentials for future attacks and reaching other devices on the network. These additional attacks could include remote control maneuvers that are very dangerous to the target system.
The research, by Jake Valletta, Erik Barzdukas and Dillon Franke, points out that it is virtually impossible to draw up a list of vulnerable devices and manufacturers because of the way manufacturers and resellers integrate the Kalay protocol before distributing the devices to end consumers.
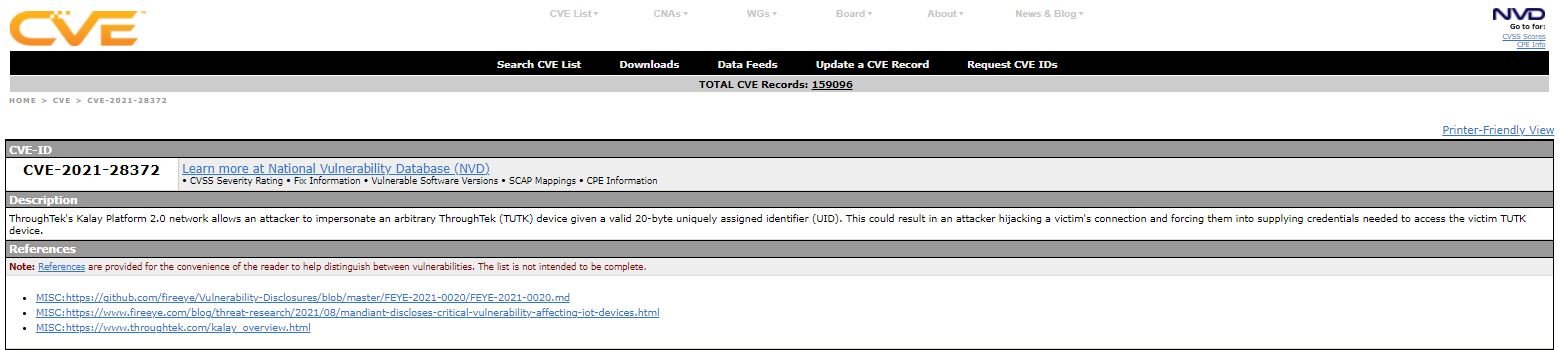
Kalay is a handshake used as a software development kit (SDK) by the ThroughTek platform that provides a plug-and-play network in order to facilitate the connection with smart devices with their respective mobile applications. The image below shows a device registration process and a client connection on the Kalay network. This process describes a user remotely accessing the Kalay-enabled camera on their home network in a mobile app from a remote network.
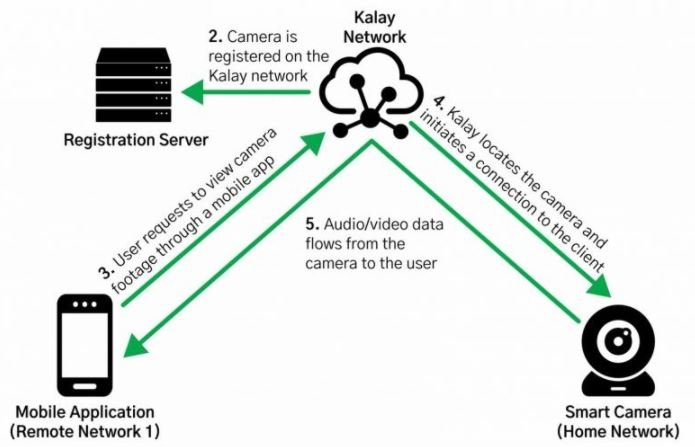
Apparently, the problem lies in the device registration process, which requires only an assigned 20-byte identifier, referred to as UID, to access the network. This UID is provided by a Kalay-enabled client (a mobile app, for example) from an API hosted by vendors for a specific device.
Exploiting this flaw requires hackers to know the Kalay protocol in detail, as well as having access to the UIDs, although this could be evaded through social engineering or other hacking tactics. By having access to this information, threat actors could take control of the affected devices and overwrite the Kalay-enabled devices on the servers and result in connection hijacking.
Subsequently, threat actors can continue the connection process to steal usernames and passwords. The following diagram shows what happens when there is an affected device and a malicious device with the same UID on the network; simply put, the malicious log overwrites the legitimate log and redirects connections to resources controlled by the attacker.
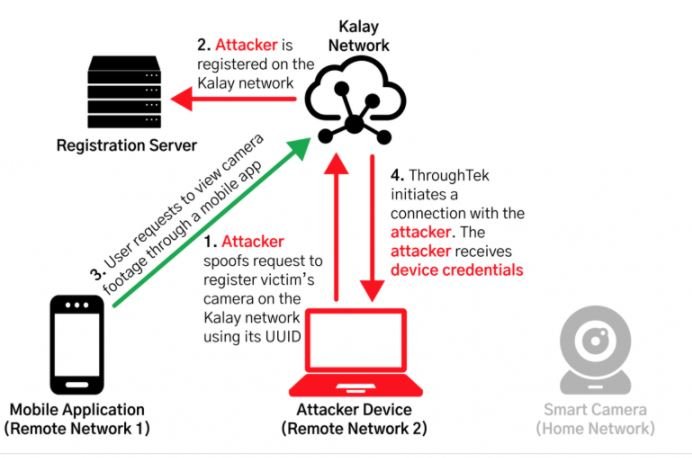
As if that were not enough, threat actors can remotely connect to the affected device and execute remote procedure calls (RPCs) in order to access audiovisual information, leading to the total remote compromise of the affected devices.
On the scope of this flaw, ThroughTek’s official platforms point out that the Kalay protocol is enabled on at least 83 million IoT devices, equivalent to more than a billion monthly connections on the platform. Mandiant’s report notes that affected Kalay products include manufacturers of IoT cameras, baby monitors and digital video recorder (DVR) products, among other equipment.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











