In a security report, BlackBerry announced that its QNX Real Time Operating System (RTOS) is affected by a vulnerability known as BadAlloc. Tracked as CVE-2021-22156, this set of flaws could be exploited for remote threat actors to deploy denial of service (DoS) attacks and remote code execution.
QNX RTOS is used in a wide range of solutions deployed in all kinds of environments, so the compromise of these systems could result in a malicious hacker gaining control of highly sensitive systems. This set of vulnerabilities was reported to the Cybersecurity and Infrastructure Security Agency (CISA), which confirms that so far no active exploitation attempts have been detected.
CVE-2021-22156 is an integer overflow vulnerability that affects the calloc() function in the C run-time library of several BlackBerry QNX products. Exploiting this vulnerability would allow DoS attacks to be deployed and arbitrary code to be executed on the affected devices.
To exploit the flaw, a threat actor must have control over the parameters of a call to the calloc() function and the ability to control which memory is accessed after allocation.
All BlackBerry programs that depend on the C library are affected by this security flaw. Many affected devices include critical deployments for various environments, so successful exploitation of faults would allow control of sensitive systems.
The following is a list of vulnerable implementations:
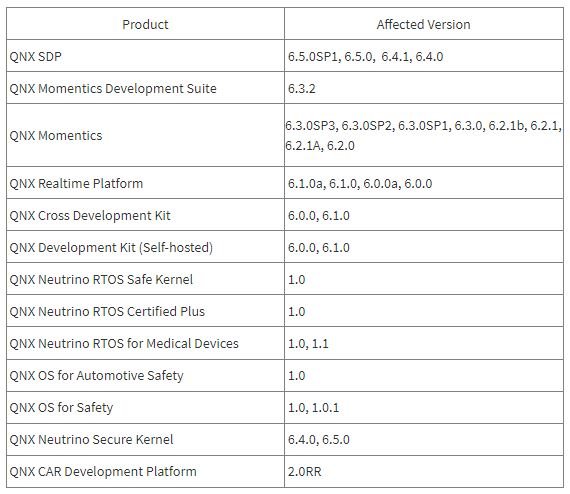
In addition to launching the notification about the failures, CISA issued a series of recommendations to prevent the exploitation of these failures:
- For manufacturers, CISA recommends contacting BlackBerry to obtain the patch code. In some cases, manufacturers may need to develop and test their own security updates
- For end users, CISA recommends contacting manufacturers of the respective products to obtain a patch. If a patch is available, users should apply the patch as soon as possible
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











