Phishing remains one of the most common and dangerous criminal practices for users in general, and every day new and dangerous tools emerge to deploy this attack variant.
On this occasion, the experts of the cybersecurity awareness course of the International Institute of Cyber Security (IICS) will show you the operation of Shark, a powerful phishing tool capable of creating malicious web pages in such a sophisticated way that it is very difficult to determine that it is a copy.
As usual, we remind you that this article was prepared for informational purposes only, so IICS is not responsible for the misuse that may be given to this tool.
According to its developers, Shark is a tool that helps users to perform phishing in an advanced way so that no one can identify malicious activity.
As mentioned earlier by the experts of the cybersecurity awareness course, phishing is a fraudulent practice to obtain confidential information from a target user by using misleading messages or usurping the image of a recognized company. This attack is usually deployed via email, text messages and even voice messages.
Installation
To get started, enter the following commands in Kali Linux:
apt update
apt upgrade
git clone https://github.com/Bhaviktutorials/shark
cd shark
chmod +x *
./setup
shark
After this procedure, we get the following panel:
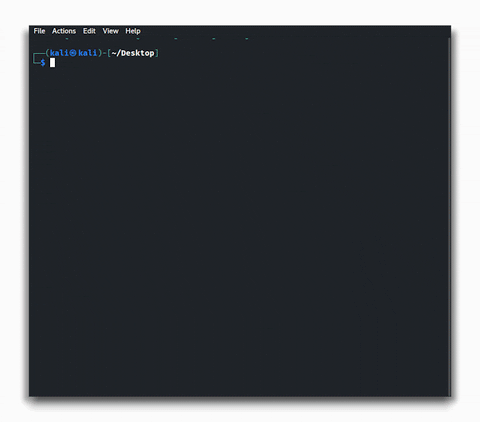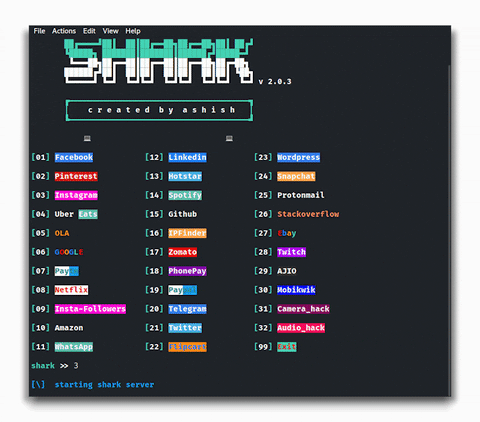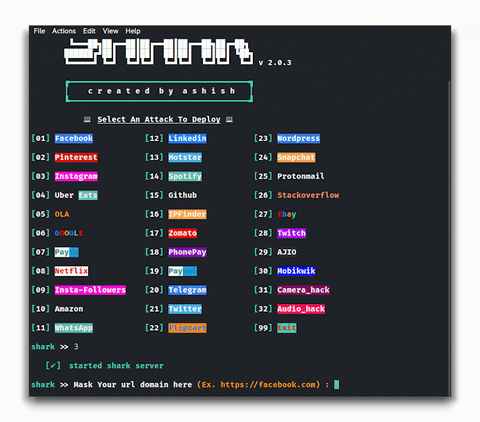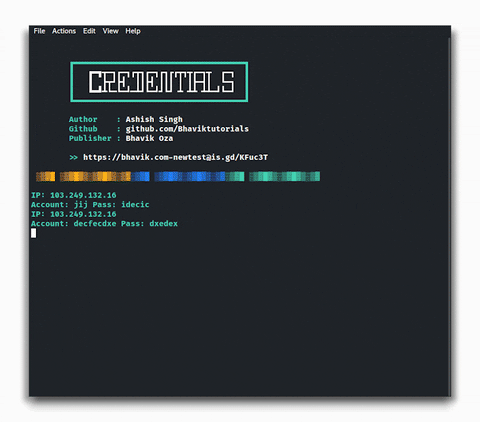
The panel is organized into a list of tools, say the specialists of the cybersecurity awareness course. From 1 to 30, we will find the necessary plugins to copy the pages of popular social or entertainment platforms.
The tools that interest us most about Shark are:
- 31: Hack a camera using a website
- 32: Hack the target user’s microphone
The image above shows the process of operation of this utility. We will not go into detail, as the plugins of this tool are very easy to use on both Kali Linux and Termux.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











