Cybersecurity specialists report the detection of a malicious campaign targeting Android users in order to hijack their Facebook accounts by stealing session cookies. Identified as FlyTrap, this campaign is based almost entirely on a simple social engineering operation, tricking affected users into entering their Facebook credentials on malicious websites and apps.
Experts from security firm Zimperium detected the malware variant used in this campaign, discovering that the compromised information was accessible to any user who discovered the C&C server used by the threat actors.
This campaign has been active at least since March 2020 and is being distributed through malicious apps available on the Google Play Store and third-party stores. The campaign was attractive to users as threat actors offered supposed gift cards for services such as Netflix or Google AdWords just by participating in a survey related to the UEFA Euro 2020 sports competition, postponed a year due to the pandemic.
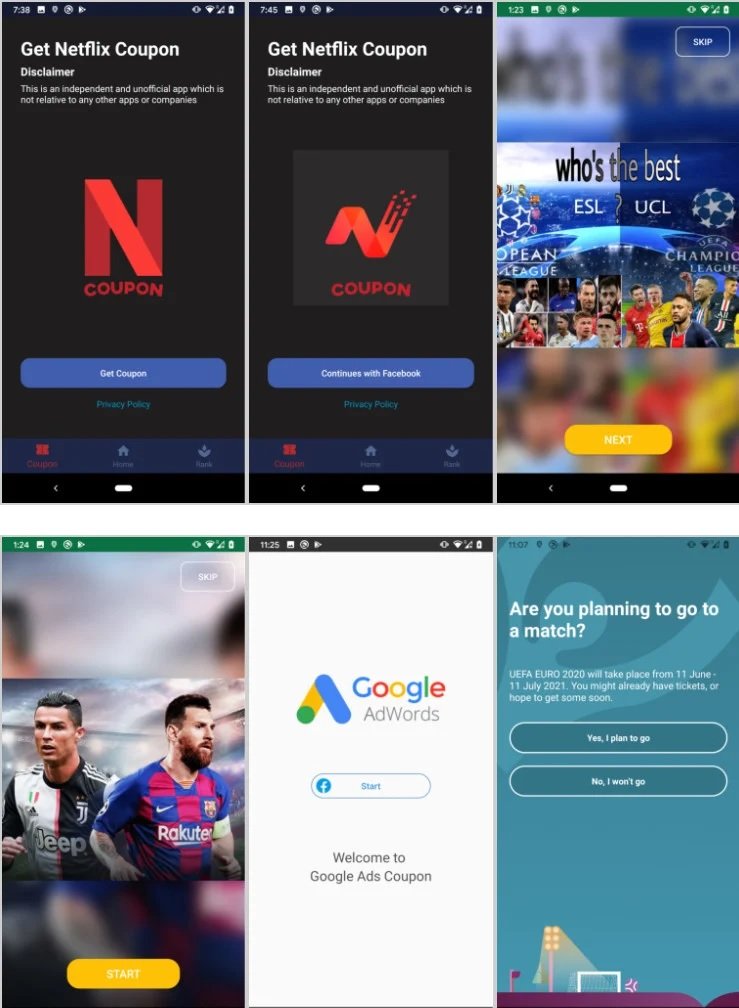
To obtain this supposed prize, users had to log in via Facebook to the malicious app. Unlike other attack variants, FlyTrap relies on JavaScript injection for the collection of sensitive information.
The compromised information is sent to the hackers’ C&C server and they have already infected around 10,000 Android devices in more than 140 countries. This data was obtained directly from the malicious C&C server, which could be analyzed by the researchers because it has no protection measure and is completely exposed on the Internet.
Zimperium’s report mentions that the malicious server is affected by multiple security vulnerabilities, making it easier to access the compromised information. Experts also point out that social media accounts are an attractive target for cybercriminals, as they can use them for fraudulent purposes and even for the deployment of campaigns to artificially increase the popularity of an online page or profile.
As usual, the main security recommendation is to ignore these kinds of ads and any online services that sound too good to be true, as this is almost certainly a scam attempt.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











