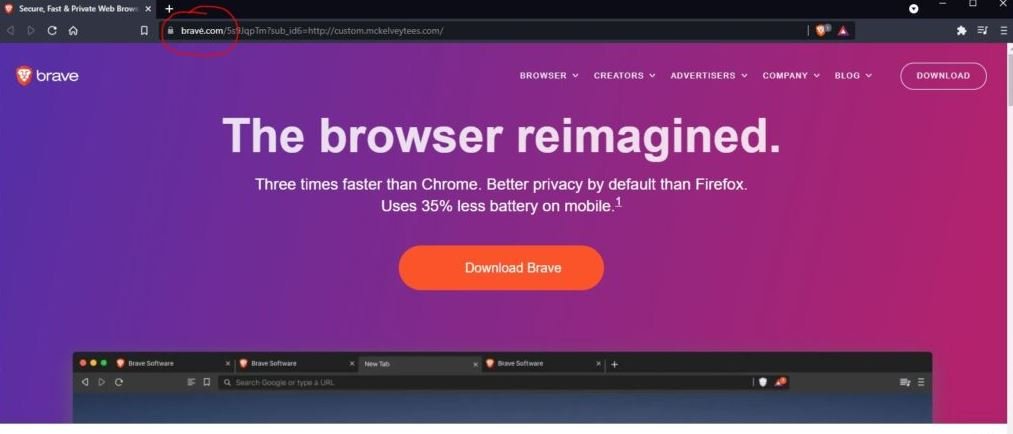
This was a difficult weekend for those users looking for new options to browse the Internet. A security report points to the detection of a malicious campaign in which users were tricked into downloading the Brave browser from a fake ad that redirected them to a malicious website. The website used by the hackers is bravė.com, which is written identically to the original website with the difference that the threat actors used the letter “ė” of the Lithuanian alphabet instead of the letter “e” of the Latin alphabet, which went unnoticed by the affected users.
The site in question was identical to Brave’s legitimate platform, so visitors did not hesitate when the website asked them to download an ISO file that supposedly contained the installer of this browser. While this file actually included such a tool, hidden in the installation package was a version of AarechClient, a malware variant also known as SectopRAT.
According to security specialist Bart Blaze, the main function of this malware is to steal sensitive information from the affected systems, including cryptocurrency addresses. This malware has mechanisms of antivirus evasion and safe environments, trying to prevent security systems from detecting malicious activity.
The recommendation for users who installed brave browser from this malicious website is to reset passwords for all their online accounts to prevent their compromise. In case users have cryptocurrency accounts, it is also recommended that they transfer their virtual assets to new secure addresses.
Through an email sent to various members of the cybersecurity community, Google confirmed that the malicious ad has been removed: “Our policies prohibit ads that intentionally try to evade security mechanisms or that attempt to impersonate other brands,” a spokesperson said.
This variant of hacking is known as an “IDN homograph attack,” which refers to when threat actors register domains using unusual characters that intentionally resemble conventional Latin characters. This type of attack became very common since the use of internationalized glyphs in domain names was approved, to which browser developers responded with the use of non-standard characters using Punycode.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











