Iranian authorities announced the delay or cancellation of some of its train services due to an alleged cyberattack that led to massive disruptions to the national railway company’s systems. While the exact cause of these disruptions is unknown, it has been confirmed that the incident impacted both public transport services and freight transport.
Initial reports indicate that systems for managing train schedules and issuing tickets were affected since Friday morning of local time. Trips scheduled for that day were cancelled and the rest postponed.
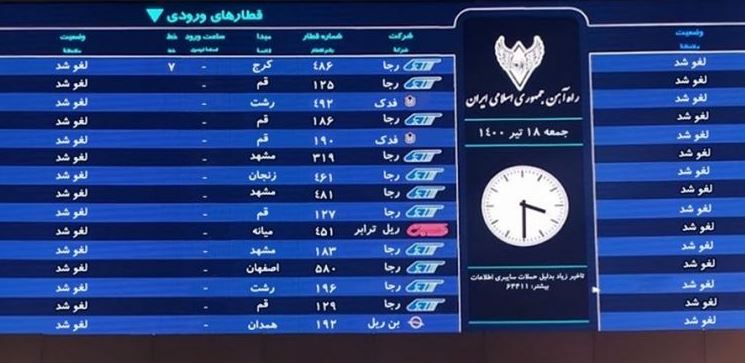
During the incident, managers of some of the affected stations advised users to report the incident to the office of Ayatollah Ali Khamenei for additional information.
On the other hand, representatives of Islamic Republic of Iran Railways (IRIR), the authority responsible for railways in the country denied that the incident was the result of an attempted hacking, although experts say that there are indications that this is a cybercrime incident.
Representatives stated that this incident was related to a technical issue that was fully corrected around 19:00 local time, although by then users were still experiencing some delays. However, shortly afterwards an unidentified actor confirmed the attack by leaking some screenshots from the infected computers.
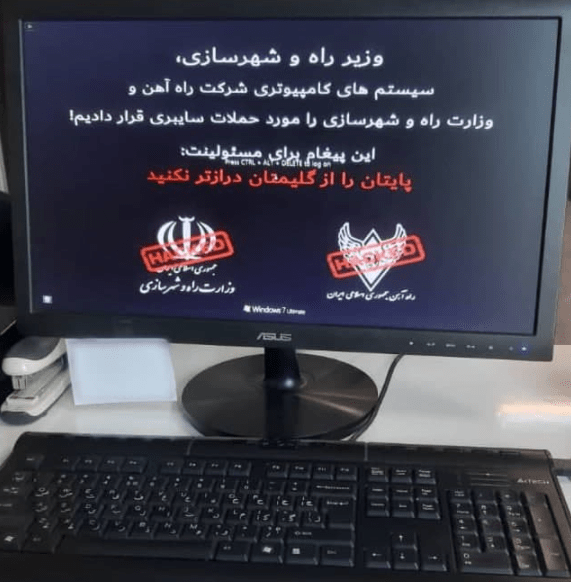
Although nothing has yet been confirmed, experts believe Iran’s government will recognize the attack and attribute it to Israeli authorities.
This wouldn’t be the first time an Israeli-linked hacking group has attacked a critical area in Iran. In May 2020, a group of hackers managed to disrupt activities in the port of Bandar Abbas, this after the Government of Israel accused Iran of funding the hacking groups responsible for the attacks on its water treatment systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











