Users of Linux systems are sometimes not aware of all the tools and functions on the system. Thinking about this situation, digital forensics specialists from the International Institute of Cyber Security (IICS) listed the top 10 Linux commands for system administration, network monitoring, and other tasks.
As usual, we remind you that this material was prepared for informational purposes only, so IICS is not responsible for any misuse of this information.
CCZE
This is a tool to decorate system logs.
$ apt-get install ccze
Examples:
$ tailf / var / log / syslog | ccze
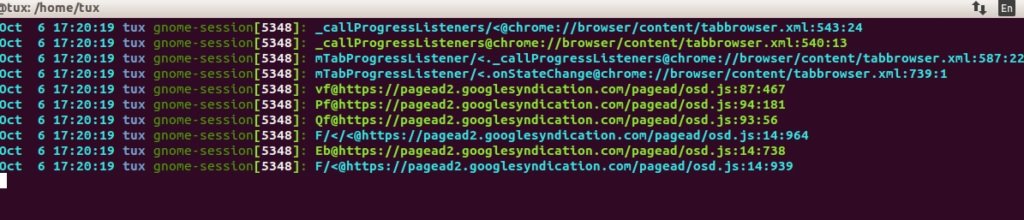
List of modules:
$ ccze –l
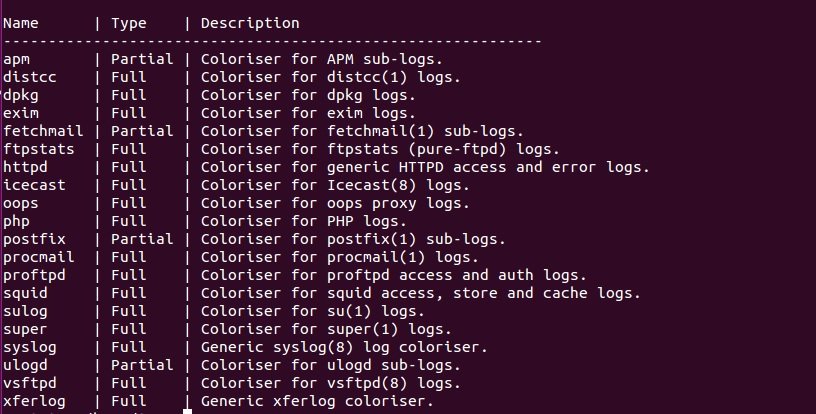
Save the record in HTML format:
tailf / var / log / syslog | ccze -h> /home/tux/Desktop/rajneesh.html
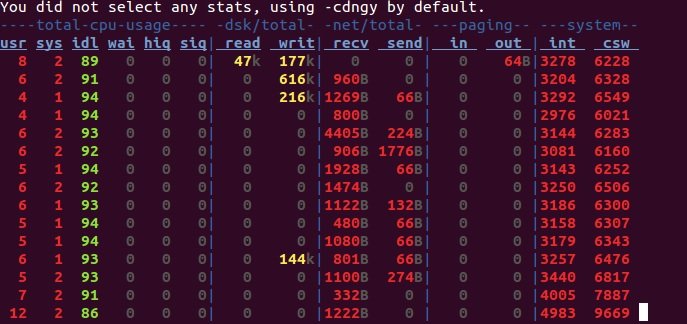
DSTAT
According to digital forensics experts, this is a flexible tool that can be used to monitor memory, processes, networks and more. Not a bad replacement for ifstat, iostat, dmstat and similar tools.
$apt-get install dstat
Detailed information about the processor, hard disk, and network:
$ dstat
Processor information only:
$ dstat –c
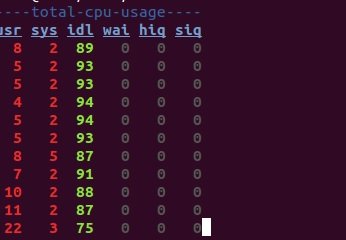
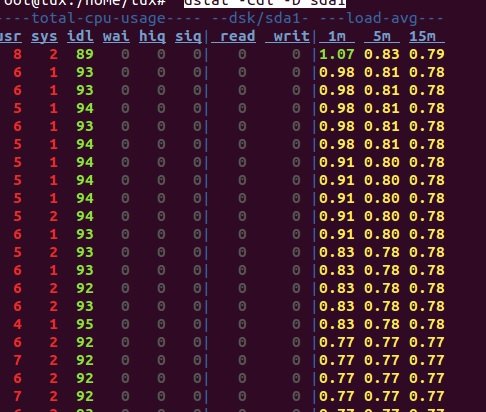
Learn more about the processor:
$ dstat -cdl -D sda1
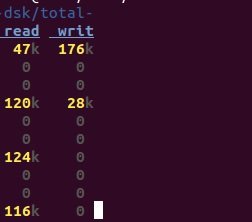
Disk information:
$ dstat –d
FINDMNT
Digital forensics specialists use this command to find mounted file systems. The command displays a list of connected devices, as well as the option to connect and disconnect a device.
Examples:
$ findmnt
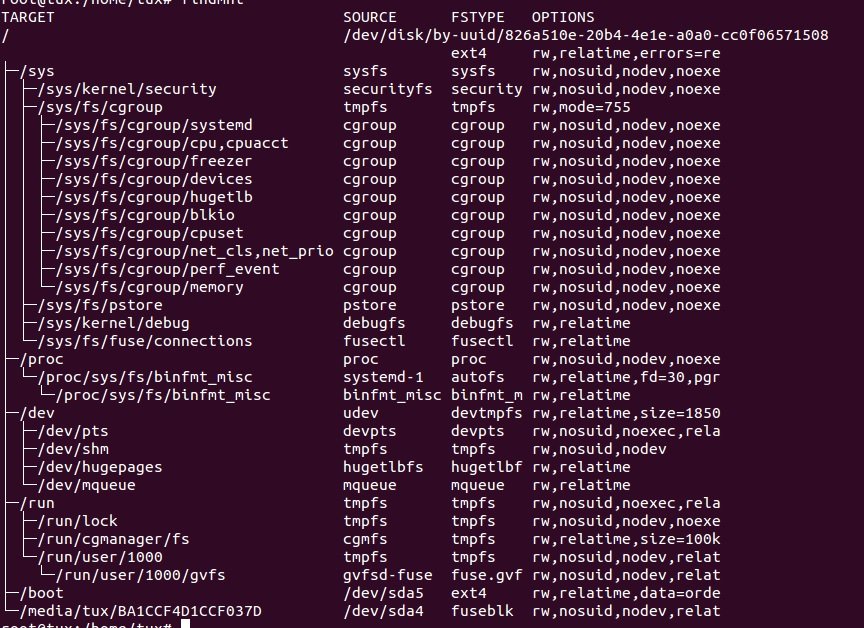
Output in list format:
$ findmnt –l
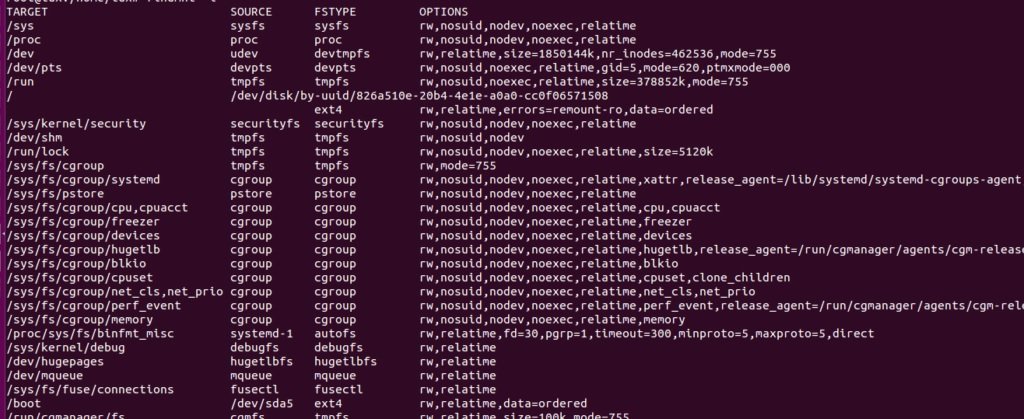
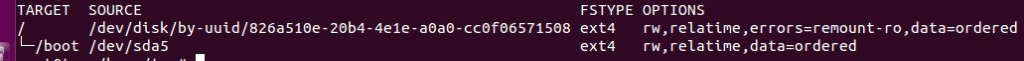
Sort by file type:
$ findmnt -t ext4
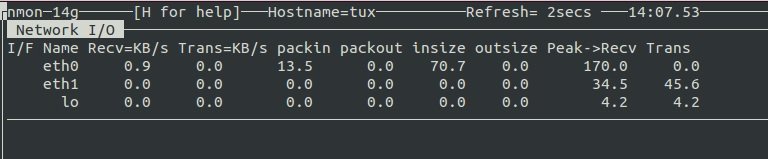
NMON
Nmon is a tool that displays information about system performance.
$ sudo apt-get install nmon
$ nmon
The tool can display information about network, CPU, memory, and disk usage.
Processor Information:
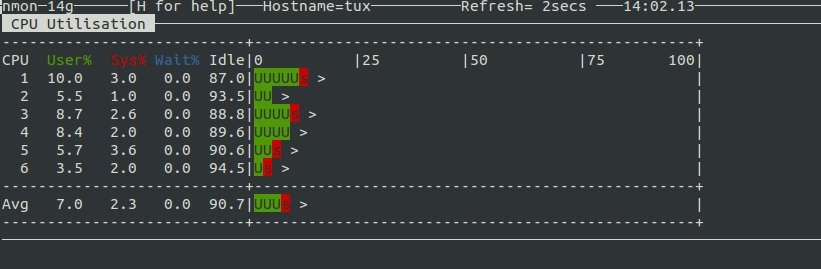
Network information:
NCDU
The ‘du’ version with cursor support is used to analyze the disk space used.
$apt-get install ncdu
$ncdu /
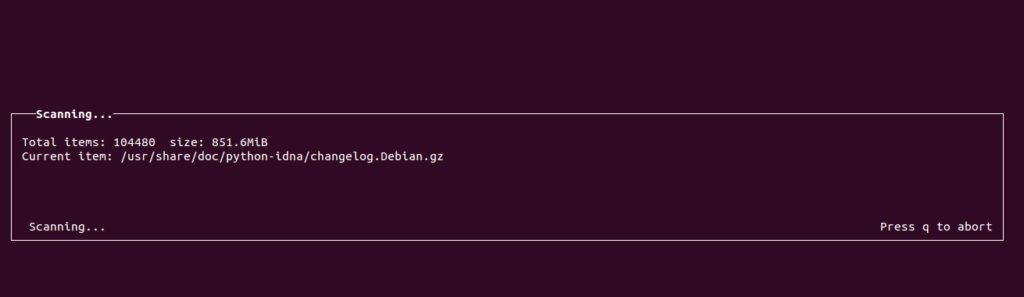
Final output:
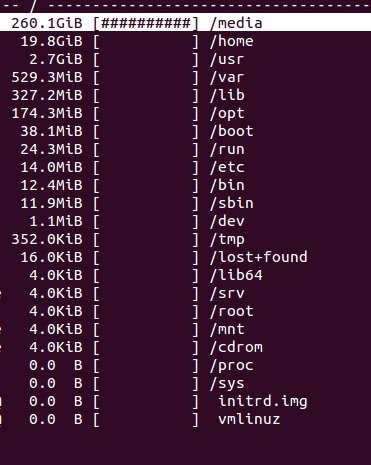
RANWHEN.PY
A useful tool written in Python that can graphically display the system’s activity. The details are represented by colored bar charts.
Install Python:
$ sudo apt-add-repository ppa:fkrull/deadsnakes
Upgrade your system:
$ sudo apt-get update
Download Python:
$ sudo apt-get install python3.2
Download and unzip ranwhen.py:
$ unzip ranwhen-master.zip && cd ranwhen-master
Run the tool:
$ python3.2 ranwhen.py
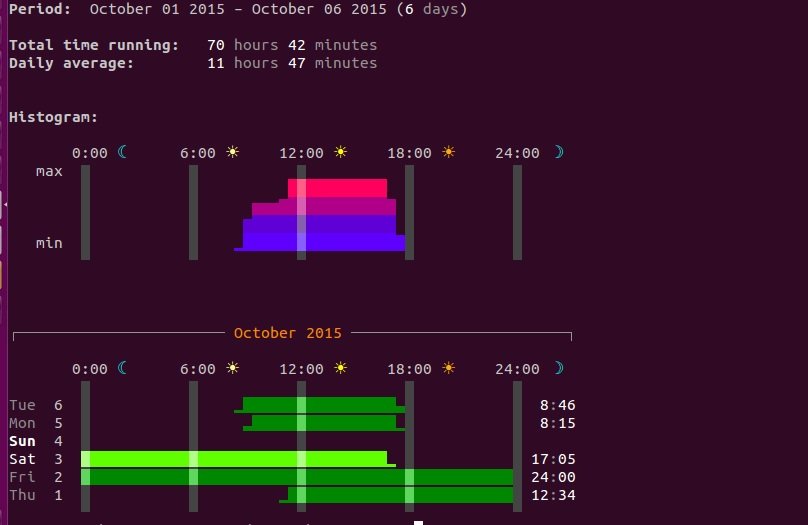
SS
This is a good substitute for netstat and is even faster in certain circumstances.
Examples:
Output of all connections:
$ ss | less
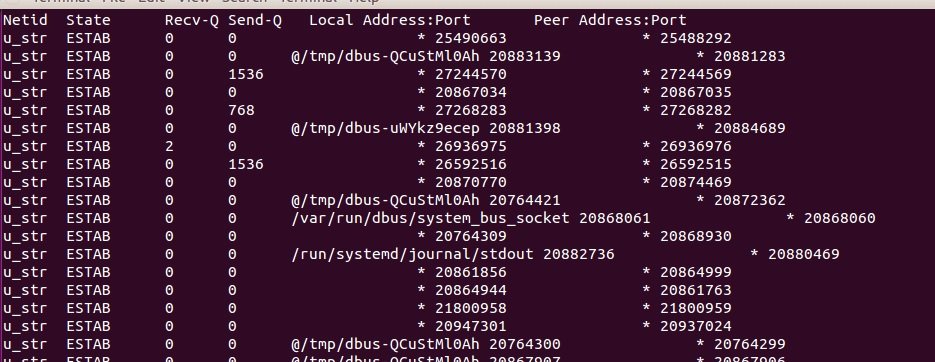
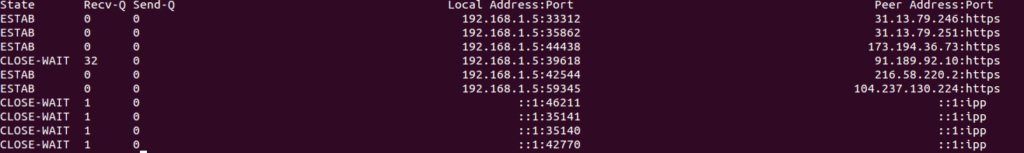
Tcp traffic-only output:
$ ss -A tcp
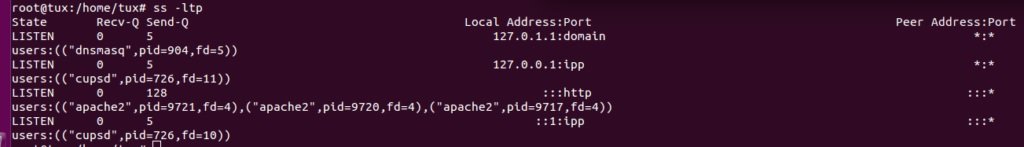
Display of process names and pids:
$ ss –ltp
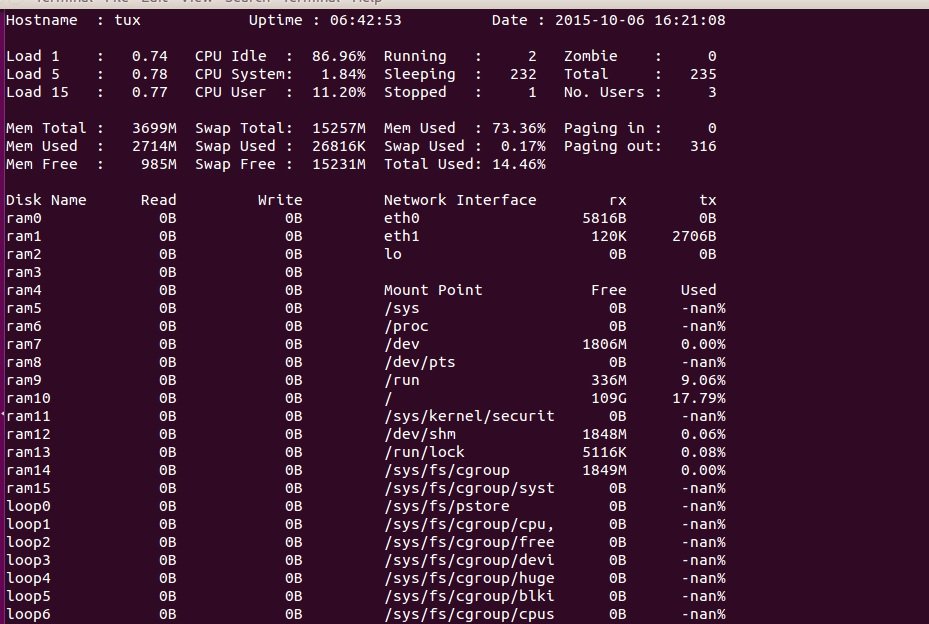
SAIDAR
This is another great utility for system monitoring.
$ sudo apt-get install saidar
Examples:
$ saidar
Colored output:
$ saider –c
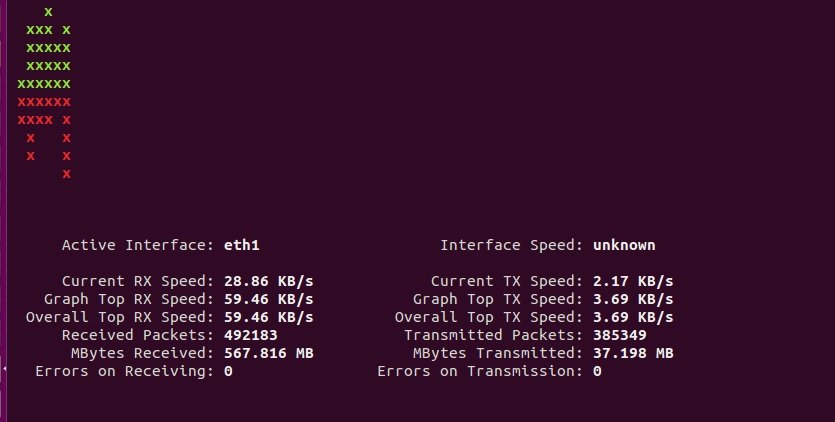
SLURM
According to digital forensics experts, this is a CLI tool designed to monitor network interfaces.
$ apt-get install slurm
Examples:
$ slurm -i <interface>
$ slurm -i eth1
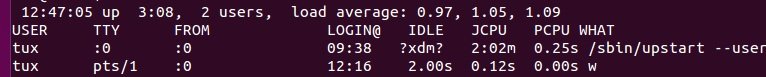
W
This utility lists the logged-on users and the processes they are running.
$w
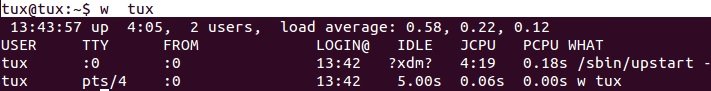
Help:
$ w –h
Current user information:
$ w <username>
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










