A group of hackers is scanning the Internet to find Cisco Adaptive Security Appliance (Cisco ASA) devices vulnerable to a flaw for which a proof of concept (PoC) exploit was leaked on Twitter. Tracked as CVE-2020-3580, this is a cross-site scripting (XSS) flaw reported and corrected in October 2020 whose patches proved insufficient to mitigate the risk of exploitation.
A successful attack would allow unauthenticated threat actors to send phishing emails or malicious links to Cisco ASA users in order to execute JavaScript commands in the context of the victim’s browser. In its security report, Cisco mentions: “A functional exploit would allow hackers to execute arbitrary XSS code in the context of the interface or allow access to sensitive browser-based information.”
As many users may know, after companies or developers fix a security flaw and a time needed to update devices expires, researchers often publish proof of concept (PoC) exploits, in what is one of the most common practices in the cybersecurity community. In this case, experts from the security firm Positive Technologies published the PoC of this flaw on Twitter.
When used in a test environment, the published exploit will display a JavaScript alert in the user’s browser after a malicious website designed for this test is entered. The problem is that the website might have been running other commands to perform malicious tasks; this was taken advantage of by some hacking groups although the nature of the attacks deployed was not confirmed.
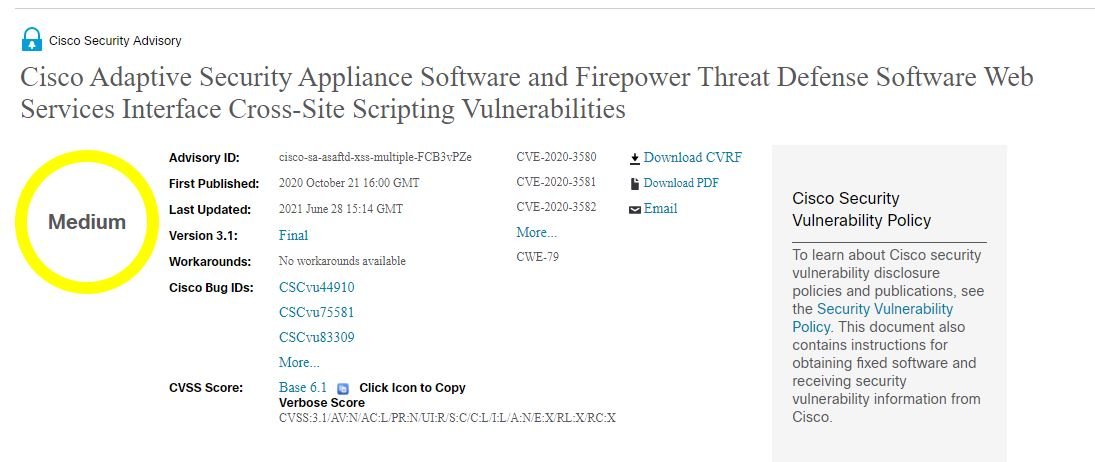
Since some cybercriminal groups are exploiting this flaw in real-world scenarios, it is necessary for administrators of vulnerable Cisco ASA deployments to install the fixes as soon as possible and thus mitigate the risks of exploitation. At the moment, the approximate number of implementations that could have been exposed to the flaw is unknown.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











