Cybersecurity experts report the discovery of a critical vulnerability in FortiWeb, the web application firewall (WAF) of the technology firm Fortinet. The vulnerability could be exploited for arbitrary code execution, which poses a critical risk to affected system operators, especially if the flaw is chained to other recently discovered bugs.
Positive Technologies researcher Andrey Medov says that the management interface of these devices is exposed to the exploitation of a flaw that would allow authenticated threat actors to execute remote commands through the SAML server configuration page. Tracked as CVE-2021-22123, the flaw was addressed with the release of FortiWeb v6.3.8 and v6.2.4.
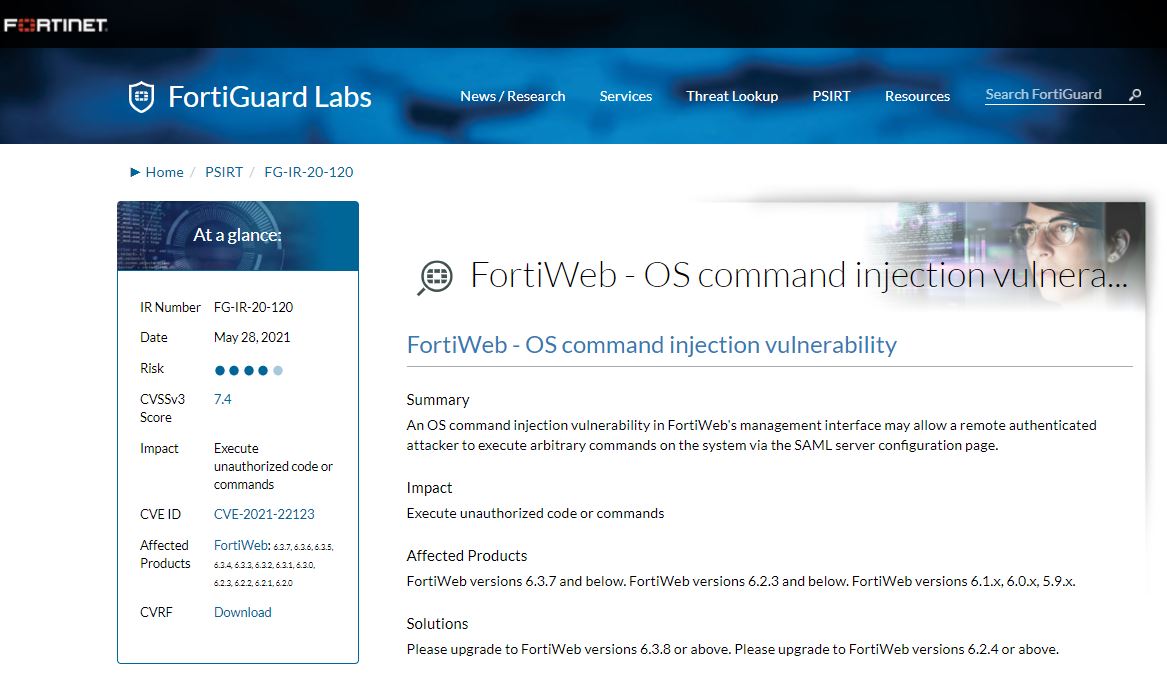
The expert mentions that the flaw can be exploited for the execution of arbitrary commands with high privileges, which would allow attackers to take complete control of the affected servers. Medov adds that the impact of the vulnerability can be even more severe if it is chained with an incorrect configuration and a separate vulnerability previously reported.
The flaw that can be chained to this bug is CVE-2020-29015 and was revealed by Fortinet last January. The vulnerability was described as a highly severe SQL injection issue: “If, as a result of incorrect configuration, the firewall management interface is available on the Internet and the product is out of date, the combination of CVE-2021-22123 and CVE-2020-29015 would allow attackers to penetrate the internal network.”
While Positive Technologies submitted its reports in a timely manner, the firm faces some accusations for alleged collaboration with the Russian government, even receiving a sanction from the U.S. government.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











