A recent cybersecurity report points to the detection of a critical and unpatched vulnerability in Lexmark printers. According to the report, successful exploitation of these flaws would allow threat actors to deploy very dangerous and even easier to deploy attacks, as they would not require the interaction of the target user.
Julio Aviña, researcher at IBM X-Force Exchange, mentions that the main risk associated with this flaw is the execution of arbitrary code through the deployment of low complexity hacks. The flaw received a score of 8.4/10 according to the Common Vulnerability Scoring System (CVSS), although so far no exploitation attempts have been detected in the wild.
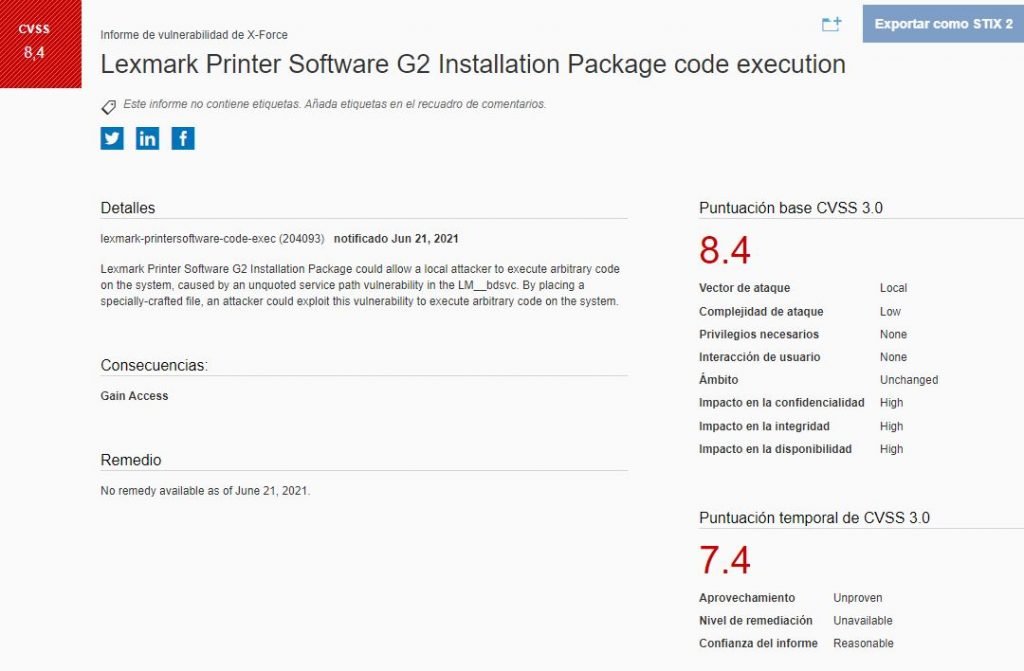
The flaw resides in the Lexmark Printer Software G2 installation package, and exists due to a unquoted service path flaw in “LM_bdsvc”, a package that allows users to customize the software installation process.
The expert mentions that by placing a specially crafted file, threat actors could abuse the flaw for arbitrary code execution on the target system. A later report indicates that LM_bdsvc.exe is a fundamental part of the printer’s communication system. Since the detection of the flaw, multiple reports and updates have been released on the problem, although so far no security patches have been issued to prevent exploitation.
Moreover, the company issued a statement to confirm that it is already working on an update patch: “Lexmark takes the security of all users very seriously. We are aware of a critical flaw in our software and want to assure you that the problem will be corrected shortly.”
This is a considerable problem because these devices are very popular in all kinds of organizations, including U.S. government agencies. In addition, Lexmark devices have been shown to be especially vulnerable to multiple hacking variants, which can put at risk any network these devices connect to.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











