This Thursday morning it was announced the release of a security patch to address a dangerous root-level vulnerability in Linux polkit that has been around for more than seven years. Polkit is used instead of sudo by systemd and allows unr privilegiosed users to run processes reserved for administrators.
The vulnerability allowed malicious users to abuse polkit to gain root access to the target system.
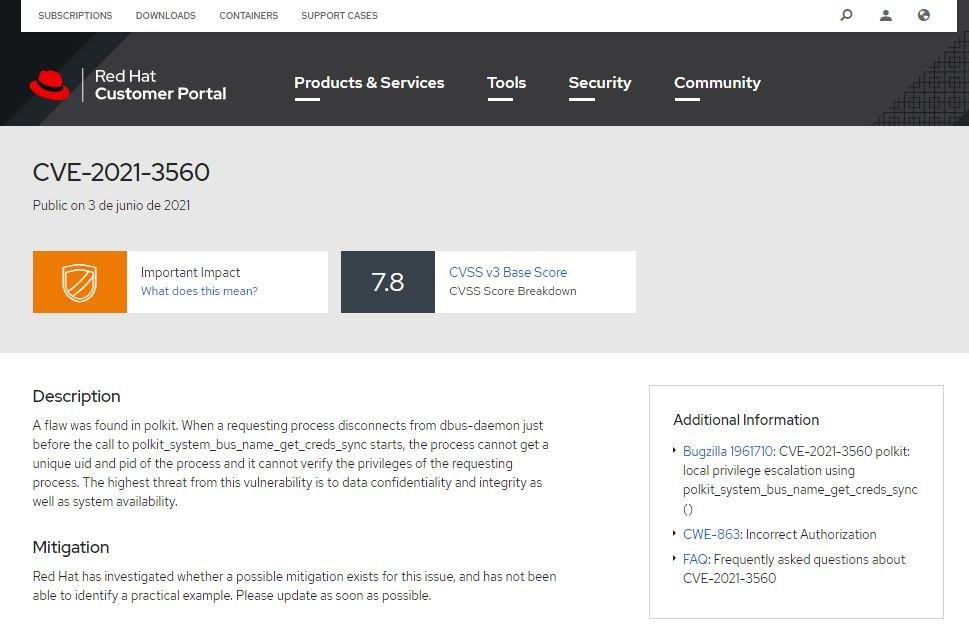
This kind of security flaws are a recurring issue for UNIX and Linux systems. According to cybersecurity specialist Kevin Blackhouse, the flaw in question was detected during a routine analysis and reported to polkit maintainers and research firm Red Hat. The flaw was tracked as CVE-2021-3560 and was corrected on June 3.
Backhouse discovered that an unauthorized local user could easily get a root shell on a vulnerable system using some standard shell tools like bash, kill, and dbus-send. Although the flaw was discovered several years ago, its abuse has arisen until recent times with the distribution of polkit in the most popular Linux distros.
The expert also mentions that the flaw had not been exploited previously because it is not activated every time you run programs that can call it, since polkit asks dbus-daemon for the UID of the requesting process several times in different code paths: “Most of those code paths handle the error correctly, but one of them will trigger an error.”
The expert adds that if the dbus-send command is canceled early, it is handled by one of the correct code paths and the request is rejected. To activate the vulnerable code path, you must disconnect at the appropriate time. And because there are multiple processes involved, the timing of that proper moment varies from one run to the next. In other words, multiple attempts are required to successfully exploit this flaw.
While this flaw does not always result in a successful attack, a threat actor could easily write a script that could activate it after multiple automatic attempts, so the security risk should not be dismissed. Users should update as soon as possible to prevent the risk of exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











