A recent report points out that it is possible to abuse Session Initiation Protocol (SIP) in order to deploy a cross-site scripting (XSS) attack. Juxhin Dyrmishi Brigjaj of Enable Security mentions that this protocol, used to manage communications through services including VoIP, audio and instant messaging, can be used as a conduit for attacks based on software applications.
The main risks are the deployment of XSS attacks, evasion of security measures such as the same-origin policy and the launch of phishing attacks and malware injections.
According to Brigjaj, in the worst case this could lead to unauthenticated remote compromise of critical systems. The researcher used as an example the case of VoIPmonitor, an open source network packet tracker used by system administrators to analyze the quality of VoIP calls based on some network parameters.
A severe vulnerability in the software’s graphical user interface (GUI) was previously detected during a security audit. One of the features of the GUI is the monitoring of sip device registration requests. The monitoring system includes the type of device that sent the SIP log message through a user-agent header value.
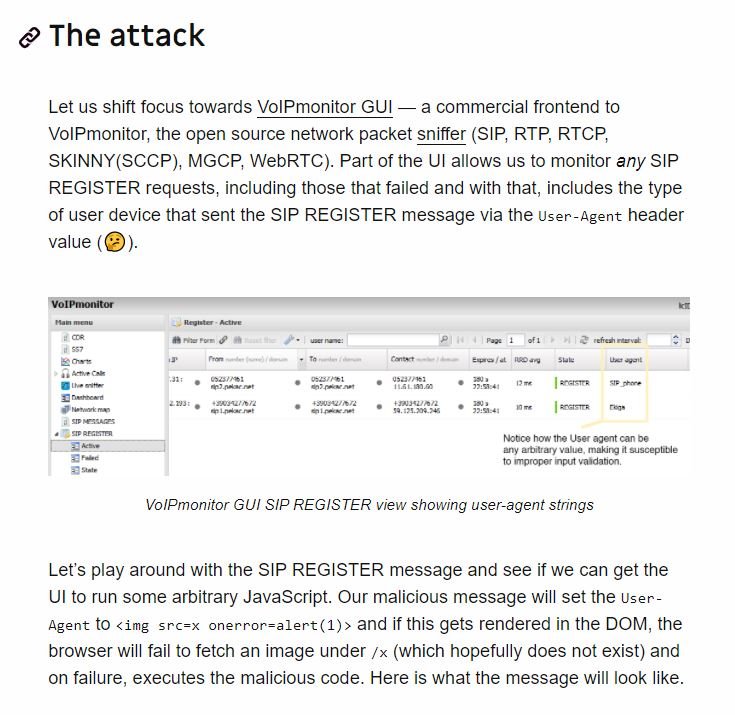
This value is represented in the DOM of the user’s web browser, so threat actors could abuse this to lead to a malicious code execution condition: “This could be non-functional in real scenarios, although we must keep in mind that this code runs in an administrator’s browser and is stored there for a period of time.”
The expert adds that remote code execution could lead to privilege escalation and persistent administrator access for threat actors. To do this, the malicious hacker requires the creation of an administrator account to store a JavaScript payload, which means that the vulnerability could have consequences that include exfiltration of data and traffic, hijacking of other administrator accounts and the implementation of malware such as keyloggers or backdoor.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











