This Tuesday afternoon, the security teams of tech firms Siemens and Schneider Electric published security alerts notifying the finding of dozens of security flaws present in various products. The patches to address these issues are already available, so it is recommended to update as soon as possible.
The patches released by Siemens address a total of 24 vulnerabilities residing in products such as Simcenter Femap, SIMATIC TIM, Solid Edge, SIMATIC NET, Mendix, JT2Go, Teamcenter Visualization and SIMATIC RF. In the notice they refer to 15 critical flaws residing in the Network Time Protocol (NTP) component of SIMANTIC NET CP 443-1 OPC UA. These flaws were detected between 2015 and 2017, although oddly enough there are still exposed implementations.
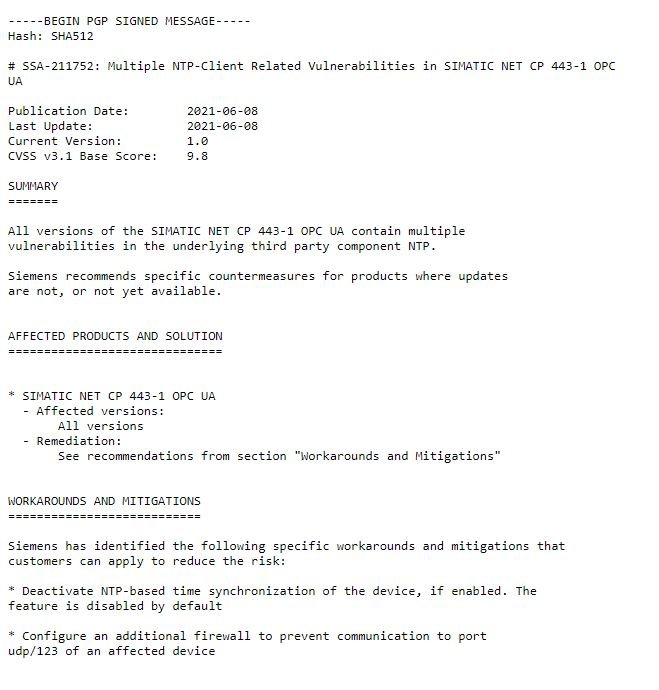
According to the report, NTP flaws can be exploited to trigger denial of service (DoS) conditions, bypassing security mechanisms in affected implementations to execute arbitrary code and extract sensitive information.
The rest of the reports at Siemens refer to flaws of medium severity that can be exploited for the deployment of DoS attacks, arbitrary code execution, data theft and privilege escalations.
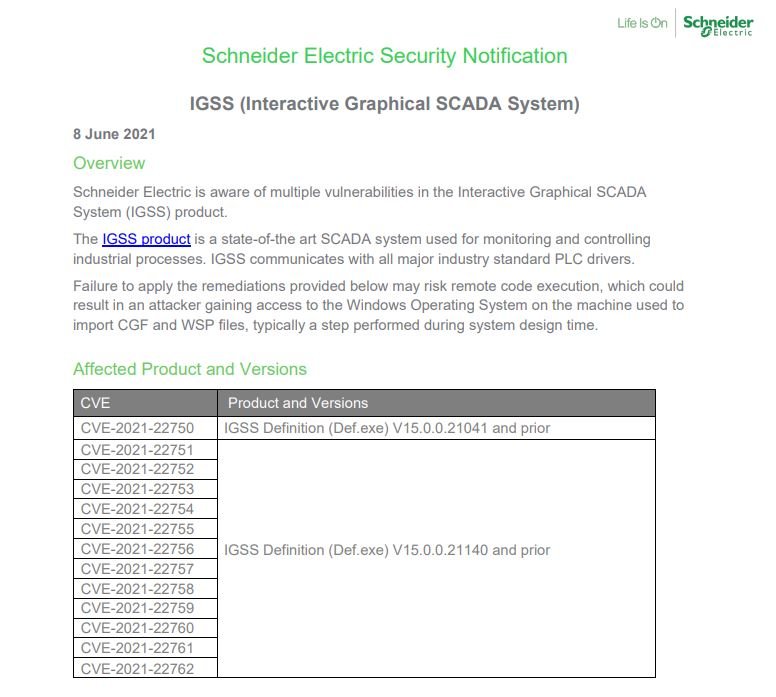
On the other hand, Schneider Electric’s security teams unveiled the fix of at least 20 vulnerabilities in its products, including 13 flaws that reside in its Graphical SCADA System solution. The report notes that successful exploitation of these vulnerabilities can result in data theft or remote code execution attacks. All a threat actor should do is trick the target user into opening a malicious file.
Two additional reports describe at least 20 vulnerabilities affecting two PowerLogic products developed by Schneider. The most severe of these would allow malicious hackers to gain administrator access to a device; these flaws were reported to Schneider by an investigator at cybersecurity firm Dragos.
A separate report alerts organizations to some vulnerabilities in IEC 61131-3 programming and engineering tools. The bugs were introduced by using Rockwell Automation’s ISaGRAF automation software, which is also used by other vendors.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











